Question 13
An attacker was easily able to log in to a company's security camera by performing a basic online search for a setup guide for that particular camera brand and model Which of the following BEST describes the configurations the attacker exploited?
Correct Answer:C
Question 14
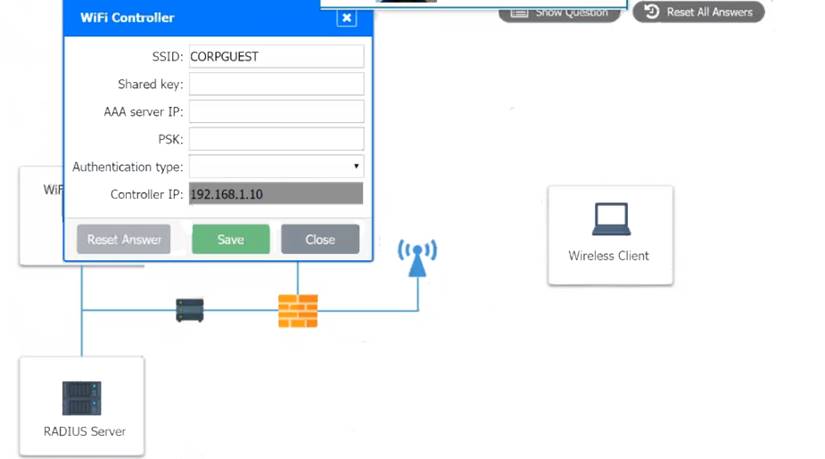
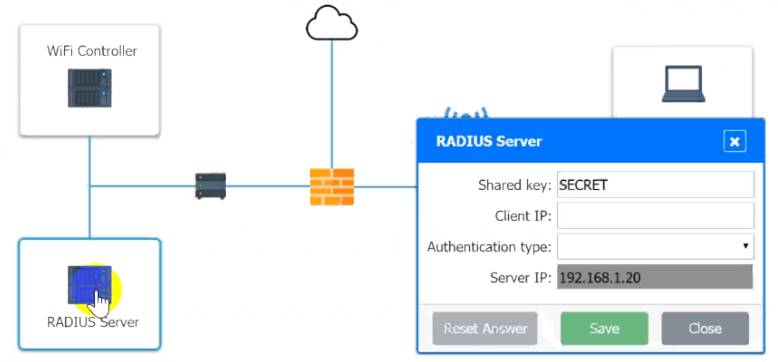
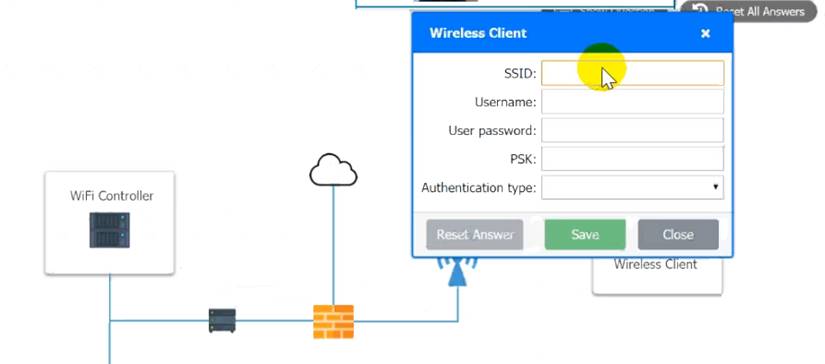
A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
Perform the following slops:
* 1. Configure the RADIUS server.
* 2. Configure the WiFi controller.
* 3. Preconfigure the client for an incoming guest.
The guest AD credentials are: User: guest01
Password: guestpass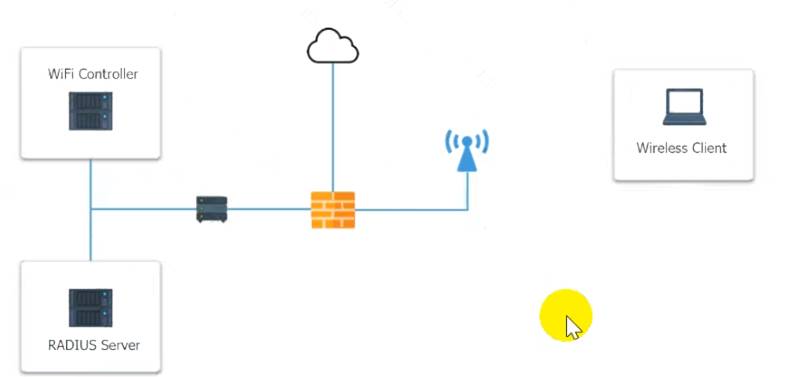
Solution:
Use the same settings as describe in below images.
Graphical user interface, application Description automatically generated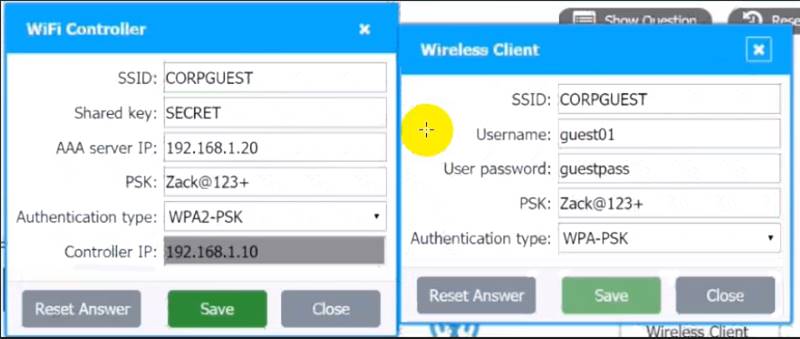
Graphical user interface, text, application, chat or text message Description automatically generated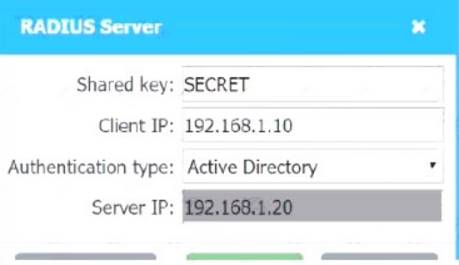
Does this meet the goal?
Correct Answer:A
Question 15
Which of the following BEST describes a security exploit for which a vendor patch is not readily available?
Correct Answer:B
Question 16
A security analyst is reviewing logs on a server and observes the following output: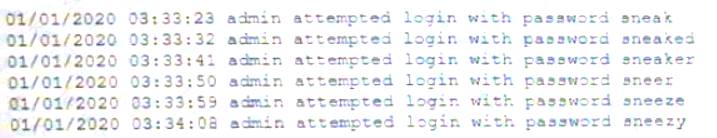
Which of the following is the security analyst observing?
Correct Answer:C
Question 17
Which of the following would cause a Chief Information Security Officer (CISO) the MOST concern regarding newly installed Internet-accessible 4K surveillance cameras?
Correct Answer:A
Question 18
Which of the following is MOST likely to contain ranked and ordered information on the likelihood and potential impact of catastrophic events that may affect business processes and systems, while also highlighting the residual risks that need to be managed after mitigating controls have been implemented?
Correct Answer:B