Question 31
- (Exam Topic 1)
A recent security audit identified that a company's application team injects database credentials into the environment variables of an IAM Fargate task. The company's security policy mandates that all sensitive data be encrypted at rest and in transit.
When combination of actions should the security team take to make the application compliant within the security policy? (Select THREE)
Correct Answer:BEF
Question 32
- (Exam Topic 3)
A company hosts data in S3. There is a requirement to control access to the S3 buckets. Which are the 2 ways in which this can be achieved?
Please select:
Correct Answer:AC
The IAM Documentation mentions the following
Amazon S3 offers access policy options broadly categorized as resource-based policies and user policies. Access policies you attach to your resources (buckets and objects) are referred to as resource-based policies. For example, bucket policies and access control lists (ACLs) are resource-based policies. You can also attach access policies to users in your account. These are called user policies. You may choose to use resource-based policies, user policies, or some combination of these to manage permissions to your Amazon S3 resources.
Option B and D are invalid because these cannot be used to control access to S3 buckets For more information on S3 access control, please refer to the below Link: https://docs.IAM.amazon.com/AmazonS3/latest/dev/s3-access-control.htmll
The correct answers are: Use Bucket policies. Use IAM user policies Submit your Feedback/Queries to our Experts
Question 33
- (Exam Topic 3)
Which technique can be used to integrate IAM IAM (Identity and Access Management) with an on-premise LDAP (Lightweight Directory Access Protocol) directory service?
Please select:
Correct Answer:B
On the IAM Blog site the following information is present to help on this context
The newly released whitepaper. Single Sign-On: Integrating IAM, OpenLDAP, and Shibboleth, will help you integrate your existing LDAP-based user directory with IAM. When you integrate your existing directory with IAM, your users can access IAM by using their existing credentials. This means that your users don't need to maintain yet another user name and password just to access IAM resources.
Option A.C and D are all invalid because in this sort of configuration, you have to use SAML to enable single sign on.
For more information on integrating IAM with LDAP for Single Sign-On, please visit the following URL:
https://IAM.amazon.eom/blogs/security/new-whitepaper-sinEle-sign-on-inteErating-IAM-openldap-and-shibbol
The correct answer is: Use SAML (Security Assertion Markup Language) to enable single sign-on between IAM and LDAP. Submit your Feedback/Queries to our Experts
Question 34
- (Exam Topic 4)
A company has multiple Amazon S3 buckets encrypted with customer-managed CMKs Due to regulatory requirements the keys must be rotated every year. The company's Security Engineer has enabled automatic key rotation for the CMKs; however the company wants to verity that the rotation has occurred.
What should the Security Engineer do to accomplish this?
Correct Answer:C
Question 35
- (Exam Topic 2)
A Security Engineer has created an Amazon CloudWatch event that invokes an IAM Lambda function daily. The Lambda function runs an Amazon Athena query that checks IAM CloudTrail logs in Amazon S3 to detect whether any IAM user accounts or credentials have been created in the past 30 days. The results of the Athena query are created in the same S3 bucket. The Engineer runs a test execution of the Lambda function via the IAM Console, and the function runs successfully.
After several minutes, the Engineer finds that his Athena query has failed with the error message: “Insufficient Permissions”. The IAM permissions of the Security Engineer and the Lambda function are shown below:
Security Engineer
Lambda function execution role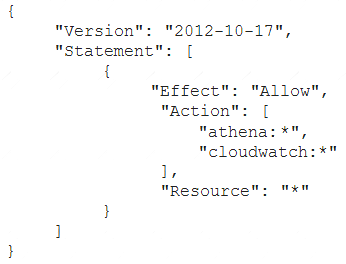
What is causing the error?
Correct Answer:D
Question 36
- (Exam Topic 3)
A company hosts data in S3. There is now a mandate that going forward all data in the S3 bucket needs to encrypt at rest. How can this be achieved?
Please select:
Correct Answer:C
The IAM Documentation mentions the following
Server-side encryption is about data encryption at rest—that is, Amazon S3 encrypts your data at the object level as it writes it to disks in its data centers and decrypts it for you when you access it. As long as you authenticate your request and you have access permissions, there is no difference in the way you access encrypted or unencrypted objects.
Options A and B are invalid because neither Access Keys nor SSL certificates can be used to encrypt data. Option D is invalid because MFA is just used as an extra level of security for S3 buckets
For more information on S3 server side encryption, please refer to the below Link: https://docs.IAM.amazon.com/AmazonS3/latest/dev/serv-side-encryption.html Submit your Feedback/Queries to our Experts