Question 121
- (Exam Topic 1)
A Developer reported that IAM CloudTrail was disabled on their account. A Security Engineer investigated the account and discovered the event was undetected by the current security solution. The Security Engineer must recommend a solution that will detect future changes to the CloudTrail configuration and send alerts when changes occur.
What should the Security Engineer do to meet these requirements?
Correct Answer:B
Question 122
- (Exam Topic 4)
A security engineer is defining the controls required to protect the IAM account root user credentials in an IAM Organizations hierarchy. The controls should also limit the impact in case these credentials have been compromised.
Which combination of controls should the security engineer propose? (Select THREE.)
A)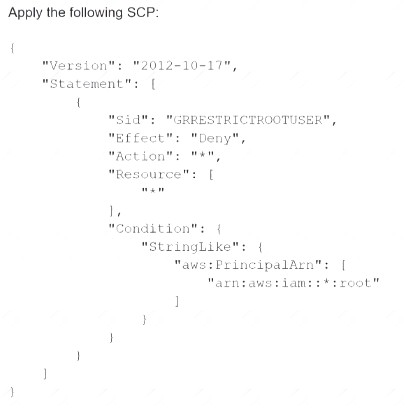
B)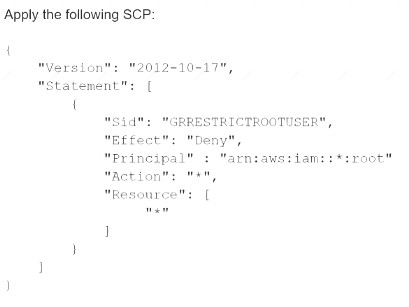
C) Enable multi-factor authentication (MFA) for the root user.
D) Set a strong randomized password and store it in a secure location.
E) Create an access key ID and secret access key, and store them in a secure location.
F) Apply the following permissions boundary to the toot user:
Correct Answer:ACE
Question 123
- (Exam Topic 1)
A company's Security Engineer has been asked to monitor and report all IAM account root user activities. Which of the following would enable the Security Engineer to monitor and report all root user activities?
(Select TWO)
Correct Answer:BE
Question 124
- (Exam Topic 2)
An Amazon EC2 instance is denied access to a newly created IAM KMS CMK used for decrypt actions. The environment has the following configuration: The instance is allowed the kms:Decrypt action in its IAM role for all resources
The instance is allowed the kms:Decrypt action in its IAM role for all resources  The IAM KMS CMK status is set to enabled
The IAM KMS CMK status is set to enabled The instance can communicate with the KMS API using a configured VPC endpoint What is causing the issue?
The instance can communicate with the KMS API using a configured VPC endpoint What is causing the issue?
Correct Answer:D
In a key policy, you use "*" for the resource, which means "this CMK." A key policy applies only to the CMK it is attached to
Question 125
- (Exam Topic 3)
A large organization is planning on IAM to host their resources. They have a number of autonomous departments that wish to use IAM. What could be the strategy to adopt for managing the accounts.
Please select:
Correct Answer:D
A recommendation for this is given in the IAM Security best practices Option A is incorrect since this would be applicable for resources in a VPC Options B and C are incorrect since operationally it would be difficult to manage For more information on IAM Security best practices please refer to the below URL
https://d1.IAMstatic.com/whitepapers/Security/IAM Security Best Practices.pdl
The correct answer is: Use multiple IAM accounts, each account for each department Submit your Feedback/Queries to our Experts
Question 126
- (Exam Topic 2)
During a recent security audit, it was discovered that multiple teams in a large organization have placed restricted data in multiple Amazon S3 buckets, and the data may have been exposed. The auditor has requested that the organization identify all possible objects that contain personally identifiable information (PII) and then determine whether this information has been accessed.
What solution will allow the Security team to complete this request?
Correct Answer:B