Online SC-200 Practice TestMore Microsoft Products >
Free Microsoft SC-200 Exam Dumps Questions
Microsoft SC-200: Microsoft Security Operations Analyst
- Get instant access to SC-200 practice exam questions
- Get ready to pass the Microsoft Security Operations Analyst exam right now using our Microsoft SC-200 exam package, which includes Microsoft SC-200 practice test plus an Microsoft SC-200 Exam Simulator.
- The best online SC-200 exam study material and preparation tool is here.
Question 1
- (Exam Topic 3)
You have the following advanced hunting query in Microsoft 365 Defender.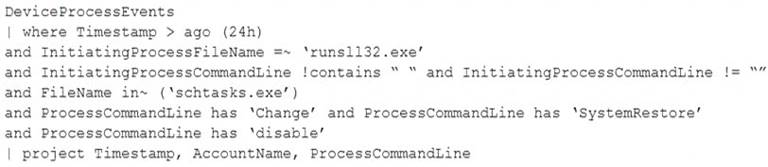
You need to receive an alert when any process disables System Restore on a device managed by Microsoft Defender during the last 24 hours.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Correct Answer:AE
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/custom-detection- rules
Question 2
- (Exam Topic 3)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Security alerts, you select the alert, select Take Action, and then expand the Mitigate the threat section.
Does this meet the goal?
Correct Answer:A
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
Question 3
- (Exam Topic 3)
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365.
You have Microsoft SharePoint Online sites that contain sensitive documents. The documents contain customer account numbers that each consists of 32 alphanumeric characters.
You need to create a data loss prevention (DLP) policy to protect the sensitive documents. What should you use to detect which documents are sensitive?
Correct Answer:C
Reference:
https://docs.microsoft.com/en-us/azure/information-protection/what-is-information-protection
Question 4
- (Exam Topic 3)
You need to visualize Azure Sentinel data and enrich the data by using third-party data sources to identify indicators of compromise (IoC).
What should you use?
Correct Answer:A
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/notebooks
Question 5
- (Exam Topic 1)
The issue for which team can be resolved by using Microsoft Defender for Endpoint?
Correct Answer:B
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/microsoft- defender-atp-ios
Question 6
- (Exam Topic 3)
You manage the security posture of an Azure subscription that contains two virtual machines name vm1 and vm2.
The secure score in Azure Security Center is shown in the Security Center exhibit. (Click the Security Center tab.)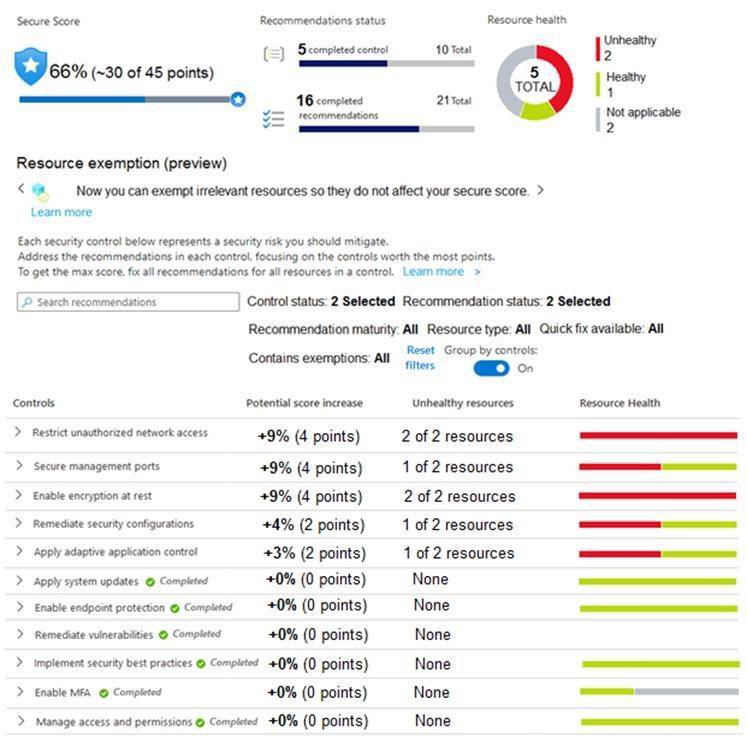
Azure Policy assignments are configured as shown in the Policies exhibit. (Click the Policies tab.)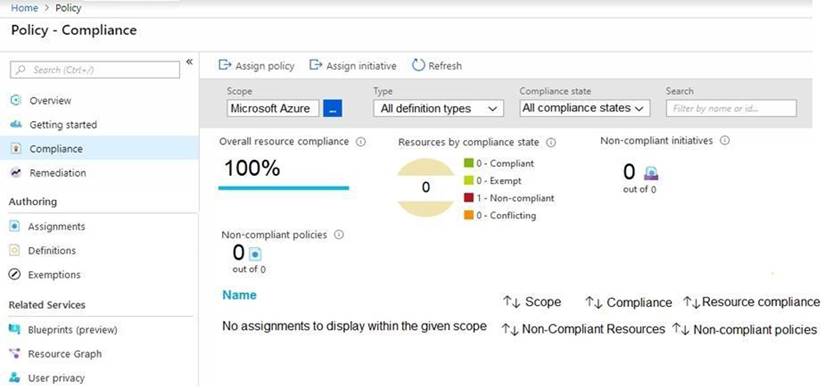
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.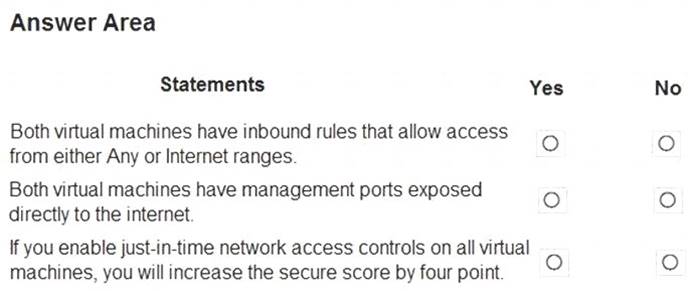
Solution:
Reference:
https://techcommunity.microsoft.com/t5/azure-security-center/security-control-restrict-unauthorized-network-ac https://techcommunity.microsoft.com/t5/azure-security-center/security-control-secure-management-ports/ba-p/1
Does this meet the goal?
Correct Answer:A