Question 13
During a security assessment, a penetration tester needs to exploit a vulnerability in a wireless network's authentication mechanism to gain unauthorized access to the network. Which of the following attacks would the tester most likely perform to gain access?
Correct Answer:C
MAC address spoofing involves changing the MAC address of a network interface to mimic another device on the network. This technique is often used to bypass network access controls and gain unauthorized access to a network.
✑ Understanding MAC Address Spoofing:
✑ Purpose:
✑ Tools and Techniques:
Step-by-Step Explanationifconfig eth0 hw ether 00:11:22:33:44:55
✑ uk.co.certification.simulator.questionpool.PList@55bce337
✑ Impact:
✑ Detection and Mitigation:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups Top of Form
Bottom of Form
=================
Question 14
SIMULATION
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.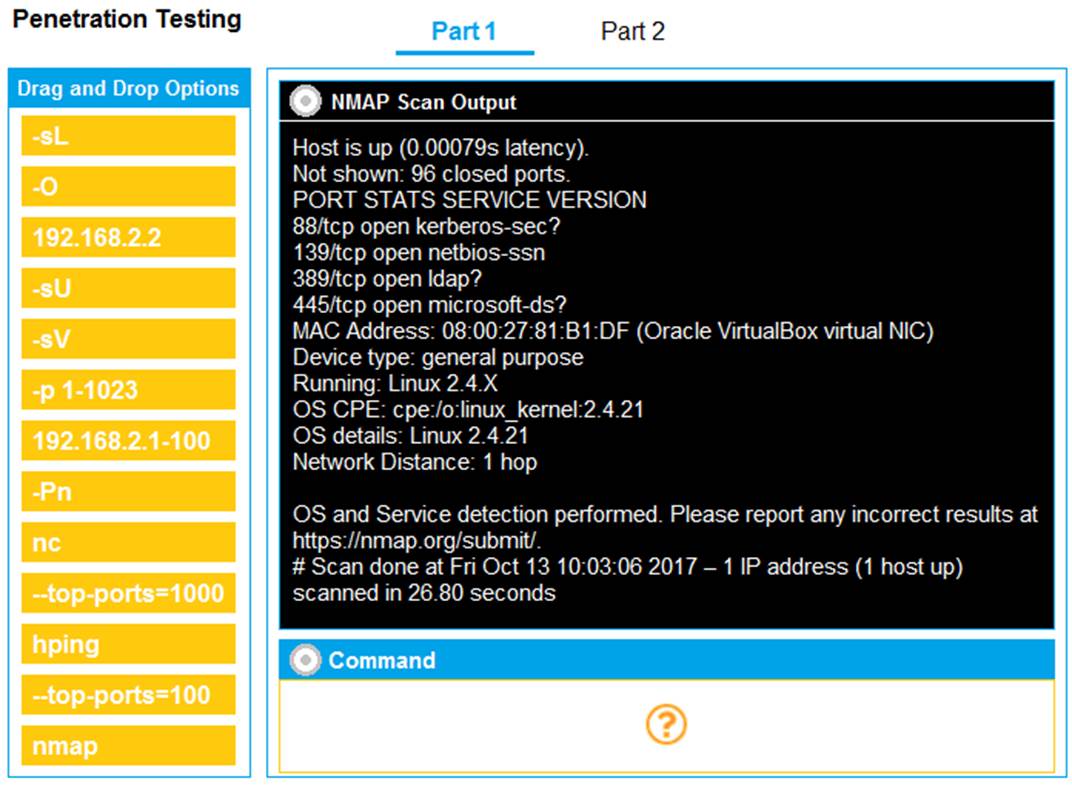
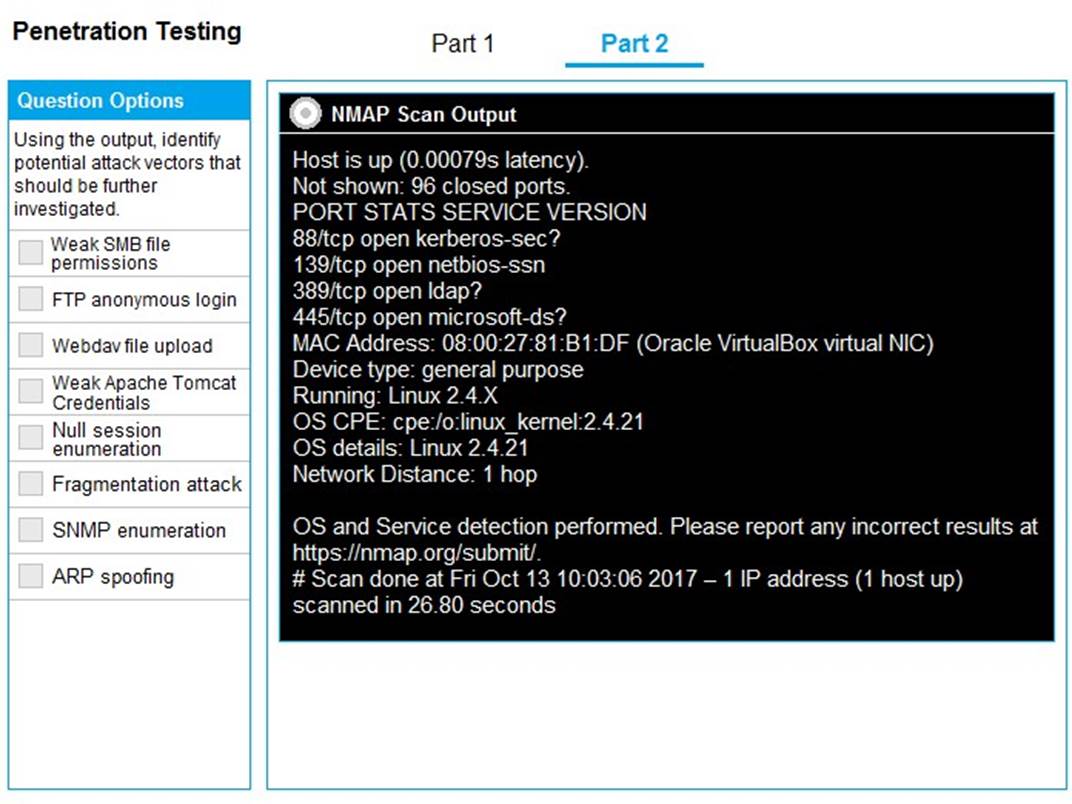
Solution:
Part 1 - 192.168.2.2 -O -sV --top-ports=100 and SMB vulns Part 2 - Weak SMB file permissions
https://subscription.packtpub.com/book/networking-and-
servers/9781786467454/1/ch01lvl1sec13/fingerprinting-os-and-services-running-on-a- target-host
Does this meet the goal?
Correct Answer:A
Question 15
A penetration tester needs to launch an Nmap scan to find the state of the port for both TCP and UDP services. Which of the following commands should the tester use?
Correct Answer:C
✑ Comparison with Other Options:
=================
Question 16
A penetration tester needs to collect information over the network for further steps in an internal assessment. Which of the following would most likely accomplish this goal?
Correct Answer:C
To collect information over the network, especially during an internal assessment, tools that can capture and analyze network traffic are essential. Responder is specifically designed for this purpose, and it can capture NTLM hashes and other credentials by poisoning various network protocols. Here??s a breakdown of the options:
✑ Option A: ntlmrelayx.py -t 192.168.1.0/24 -1 1234
✑ Option B: nc -tulpn 1234 192.168.1.2
✑ Option C: responder.py -I eth0 -wP
✑ Option D: crackmapexec smb 192.168.1.0/24
References from Pentest:
✑ Anubis HTB: Highlights the use of Responder to capture network credentials and hashes during internal assessments.
✑ Horizontall HTB: Demonstrates the effectiveness of Responder in capturing and analyzing network traffic for further exploitation.
=================
Question 17
Which of the following OT protocols sends information in cleartext?
Correct Answer:C
Operational Technology (OT) protocols are used in industrial control systems (ICS) to manage and automate physical processes. Here??s an analysis of each protocol regarding whether it sends information in cleartext:
✑ TTEthernet (Option A):
✑ DNP3 (Option B):
✑ Modbus (Answer: C):
✑ PROFINET (Option D):
Conclusion: Modbus is the protocol that most commonly sends information in cleartext, making it vulnerable to eavesdropping and interception.
Question 18
During a security assessment, a penetration tester gains access to an internal server and manipulates some data to hide its presence. Which of the following is the best way for the penetration tester to hide the activities performed?
Correct Answer:A
During a penetration test, one of the critical steps for maintaining access and covering tracks is to clear evidence of the attack. Manipulating data to hide activities on an internal server involves ensuring that logs and traces of the attack are removed. Here's a detailed explanation of why clearing the Windows event logs is the best method for this scenario:
✑ Understanding Windows Event Logs: Windows event logs are a key forensic
artifact that records system, security, and application events. These logs can provide detailed information about user activities, system changes, and potential security incidents.
✑ Why Clear Windows Event Logs:
✑ Method to Clear Event Logs:
shell
Copy code wevtutil cl System wevtutil cl Security
wevtutil cl Application
✑ uk.co.certification.simulator.questionpool.PList@6126ce2a
✑ Alternative Options and Their Drawbacks:
✑ Case References:
In conclusion, clearing Windows event logs is a well-established practice for hiding activities during a penetration test. It is the most effective way to remove evidence of the attack from the system, thereby maintaining stealth and ensuring that the tester's actions remain undetected.
=================