Question 7
Which of the following tasks would ensure the key outputs from a penetration test are not lost as part of the cleanup and restoration activities?
Correct Answer:A
Preserving artifacts ensures that key outputs from the penetration test, such as logs,
screenshots, captured data, and any generated reports, are retained for analysis, reporting, and future reference.
✑ Importance of Preserving Artifacts:
✑ Types of Artifacts:
✑ Best Practices:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
Question 8
A penetration tester established an initial compromise on a host. The tester wants to pivot to other targets and set up an appropriate relay. The tester needs to enumerate through the compromised host as a relay from the tester's machine. Which of the following commands should the tester use to do this task from the tester's host?
Correct Answer:D
ProxyChains is a tool that allows you to route your traffic through a chain of proxy servers, which can be used to anonymize your network activity. In this context, it is being used to route Nmap scan traffic through the compromised host, allowing the penetration tester to pivot and enumerate other targets within the network.
✑ Understanding ProxyChains:
✑ Command Breakdown:
✑ Setting Up ProxyChains: Step-by-Step Explanationplaintext Copy code
socks4 127.0.0.1 1080
✑ Execution:
proxychains nmap -sT
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
Question 9
During a security assessment, a penetration tester needs to exploit a vulnerability in a wireless network's authentication mechanism to gain unauthorized access to the network. Which of the following attacks would the tester most likely perform to gain access?
Correct Answer:A
To exploit a vulnerability in a wireless network's authentication mechanism and gain unauthorized access, the penetration tester would most likely perform a KARMA attack.
✑ KARMA Attack:
✑ Purpose:
✑ Other Options:
Pentest References:
✑ Wireless Security Assessments: Understanding common attack techniques such as KARMA is crucial for identifying and exploiting vulnerabilities in wireless networks.
✑ Rogue Access Points: Setting up rogue APs to capture credentials or perform man-in-the-middle attacks is a common tactic in wireless penetration testing.
By performing a KARMA attack, the penetration tester can exploit the wireless network's authentication mechanism and gain unauthorized access to the network.
=================
Question 10
A penetration tester performs an assessment on the target company's Kubernetes cluster using kube-hunter. Which of the following types of vulnerabilities could be detected with the tool?
Correct Answer:B
kube-hunter is a tool designed to perform security assessments on Kubernetes clusters. It identifies various vulnerabilities, focusing on weaknesses and misconfigurations. Here??s why option B is correct:
✑ Kube-hunter: It scans Kubernetes clusters to identify security issues, such as
misconfigurations, insecure settings, and potential attack vectors.
✑ Network Configuration Errors: While kube-hunter might identify some network- related issues, its primary focus is on Kubernetes-specific vulnerabilities and misconfigurations.
✑ Application Deployment Issues: These are more related to the applications running within the cluster, not the cluster configuration itself.
✑ Security Vulnerabilities in Docker Containers: Kube-hunter focuses on the Kubernetes environment rather than Docker container-specific vulnerabilities.
References from Pentest:
✑ Forge HTB: Highlights the use of specialized tools to identify misconfigurations in environments, similar to how kube-hunter operates within Kubernetes clusters.
✑ Anubis HTB: Demonstrates the importance of identifying and fixing misconfigurations within complex environments like Kubernetes clusters.
Conclusion:
Option B, weaknesses and misconfigurations in the Kubernetes cluster, accurately describes the type of vulnerabilities that kube-hunter is designed to detect.
=================
Question 11
SIMULATION
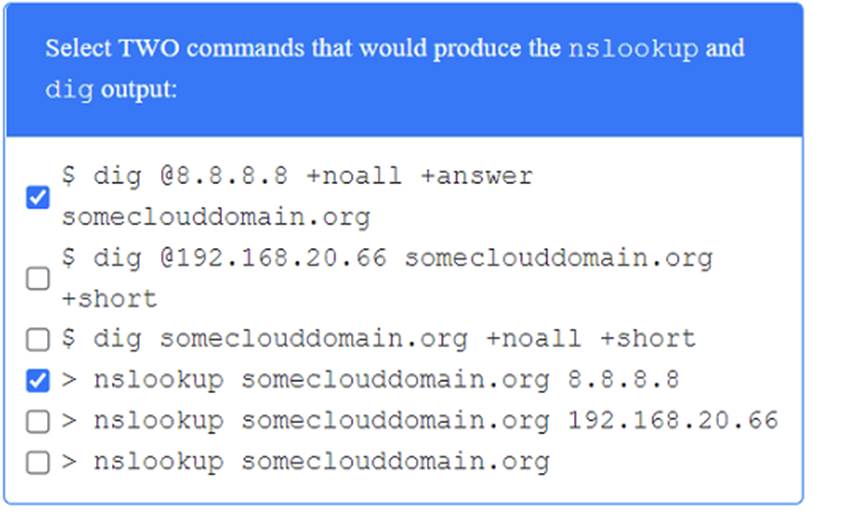
A penetration tester has been provided with only the public domain name and must enumerate additional information for the public-facing assets.
INSTRUCTIONS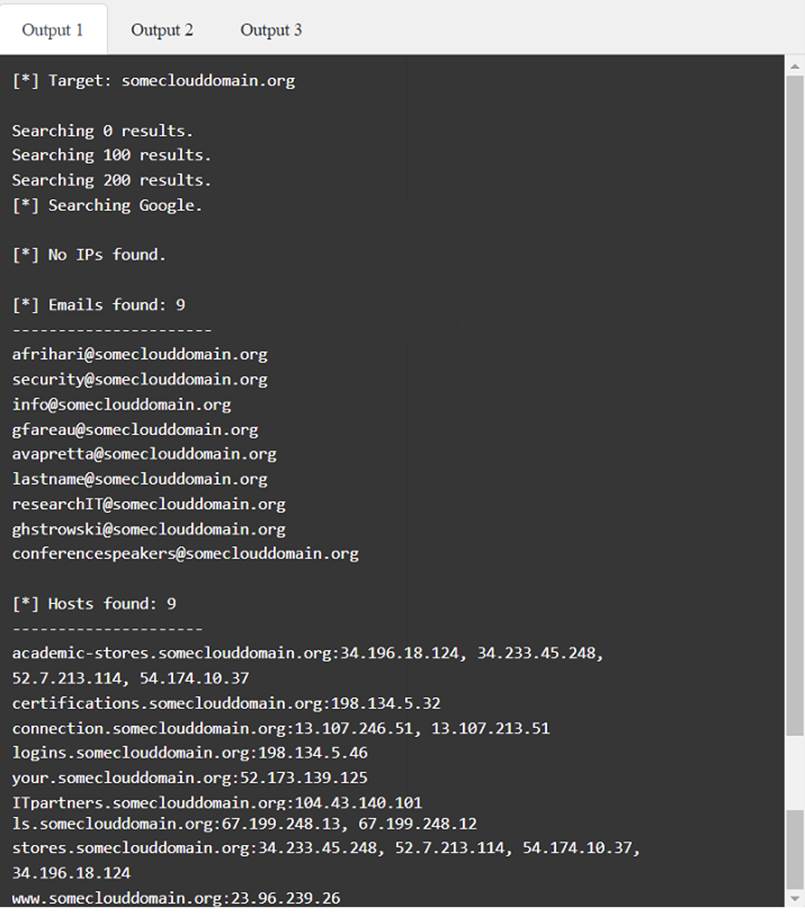
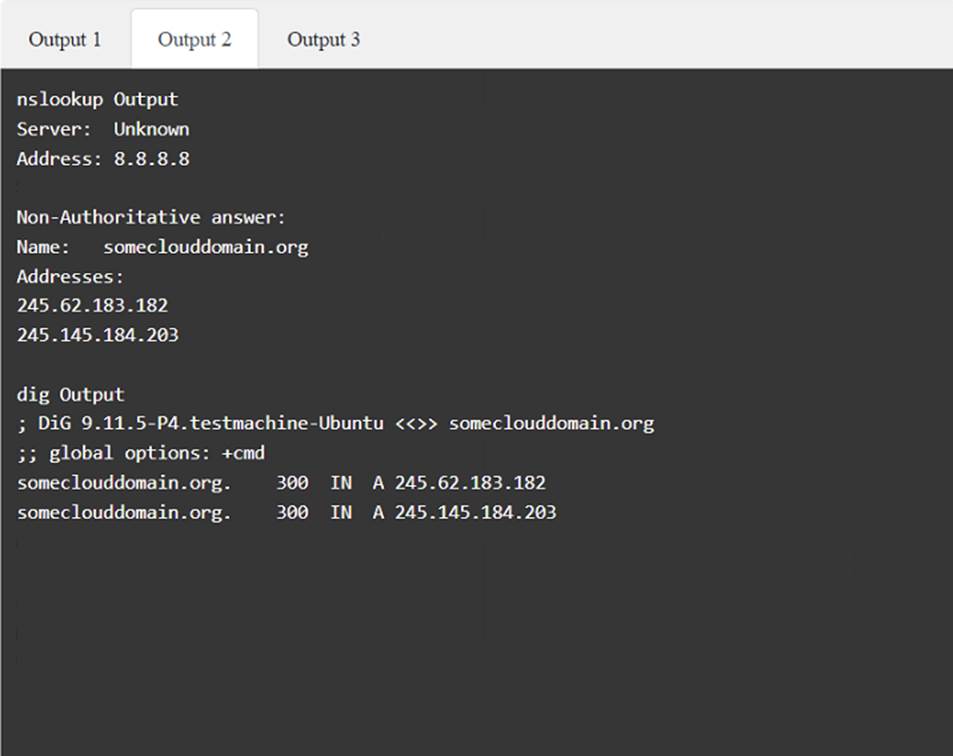
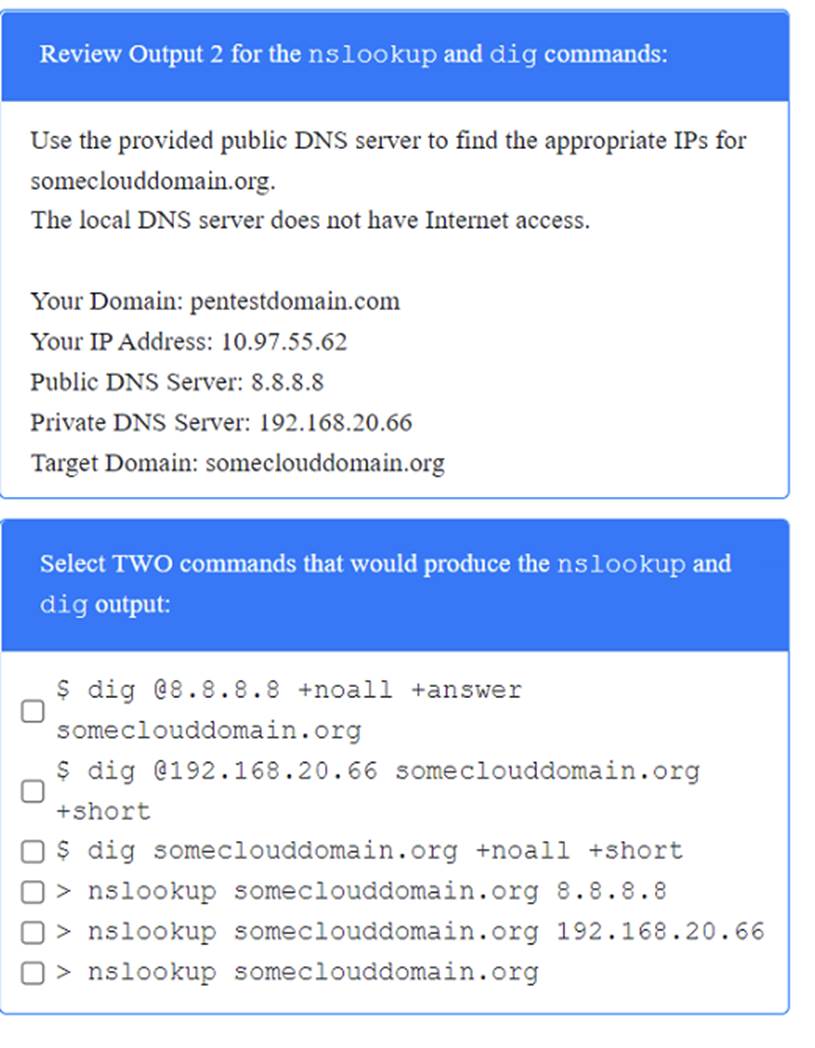
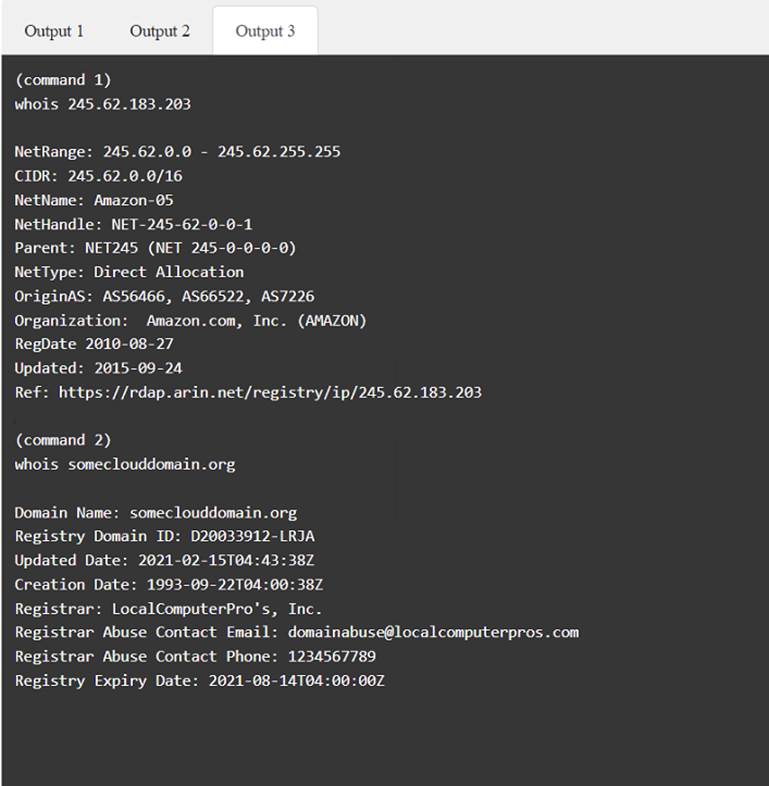
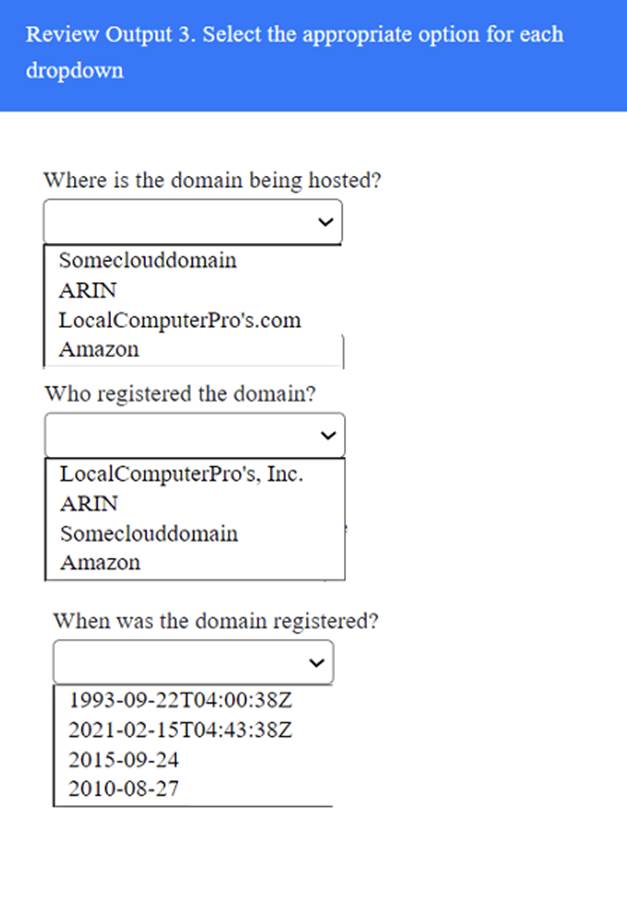
Solution: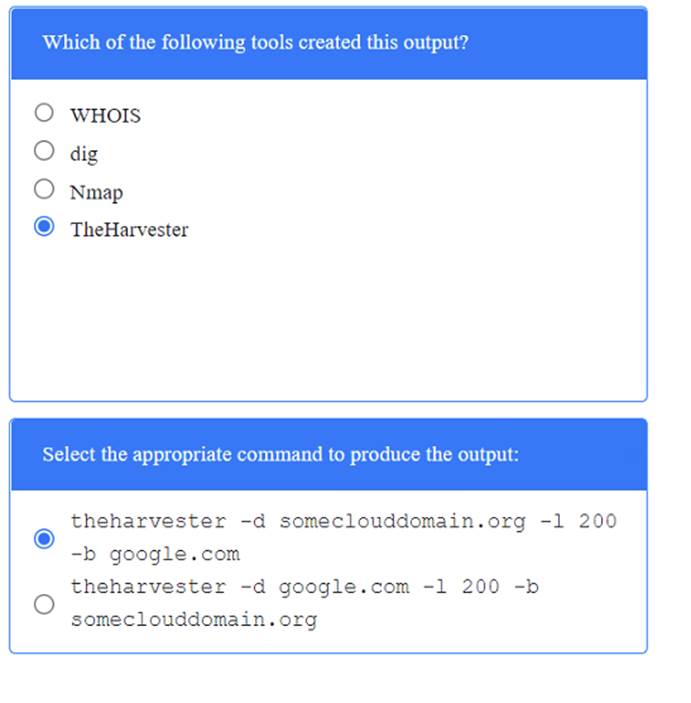
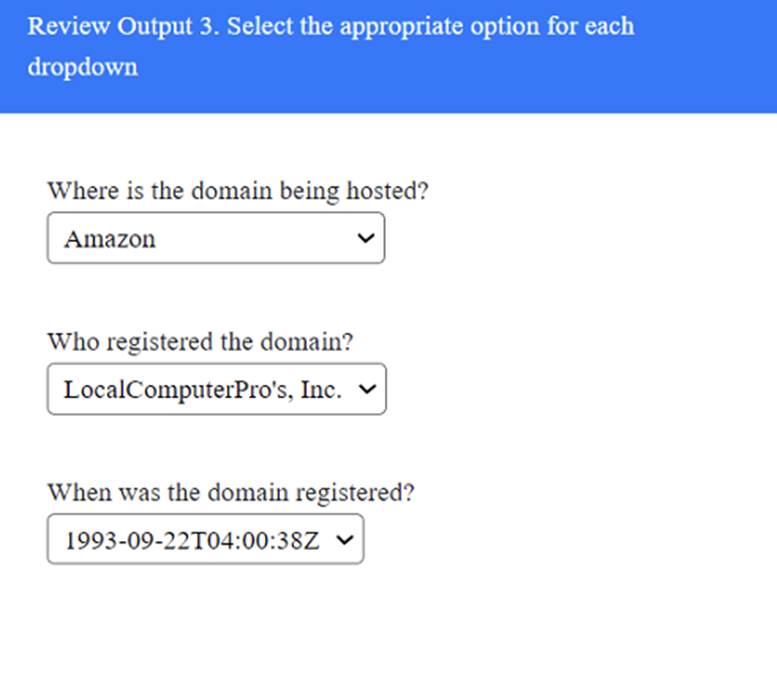
Does this meet the goal?
Correct Answer:A
Question 12
A penetration tester is conducting a wireless security assessment for a client with 2.4GHz and 5GHz access points. The tester places a wireless USB dongle in the laptop to start capturing WPA2 handshakes. Which of the following steps should the tester take next?
Correct Answer:A
Enabling monitoring mode on the wireless adapter is the essential step before capturing WPA2 handshakes. Monitoring mode allows the adapter to capture all wireless traffic in its vicinity, which is necessary for capturing handshakes.
✑ Preparation:
✑ Enable Monitoring Mode:
Step-by-Step Explanationairmon-ng start wlan0
✑ uk.co.certification.simulator.questionpool.PList@3327f1d6 iwconfig
✑ Capture WPA2 Handshakes: airodump-ng wlan0mon
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================