Question 13
Which of the following CPU register does the penetration tester need to overwrite in order to explogt a simple butter overflow?
Correct Answer:D
Question 14
An email sent from the Chief Executive Officer (CEO) to the Chief Financial Officer (CFO) states a wire transfer is needed to pay a new vendor. Neither is aware of the vendor, and the CEO denies ever
sending the email. Which of the following types of motivation was used m this attack?
Correct Answer:E
Question 15
A. penetration tester wants to check manually if a "ghost" vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
Correct Answer:D
Question 16
After several attempts, an attacker was able to gain unauthorized access through a biometric sensor using the attacker's actual fingerprint without explogtation. Which of the following is the MOST likely explanation of what happened?
Correct Answer:A
Question 17
While prioritizing findings and recommendations for an executive summary, which of the following considerations would De MOST valuable to the client?
Correct Answer:C
Question 18
DRAG DROP
Performance based
You are a penetration Inter reviewing a client's website through a web browser. Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present. Remediate ONLY the highest vulnerability from either the certificate source or cookies.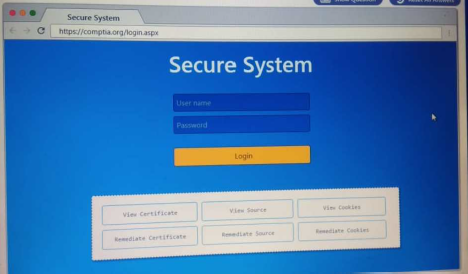
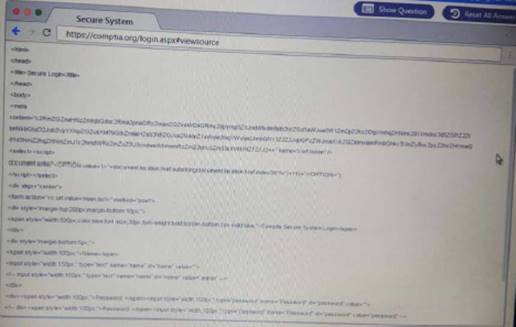
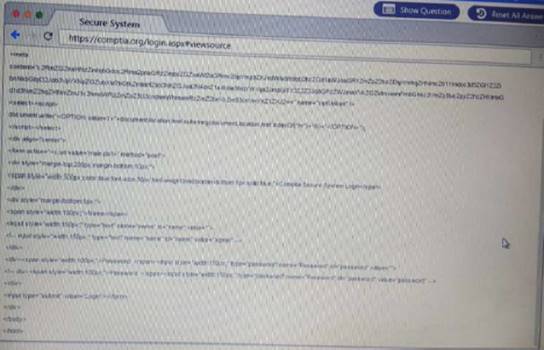
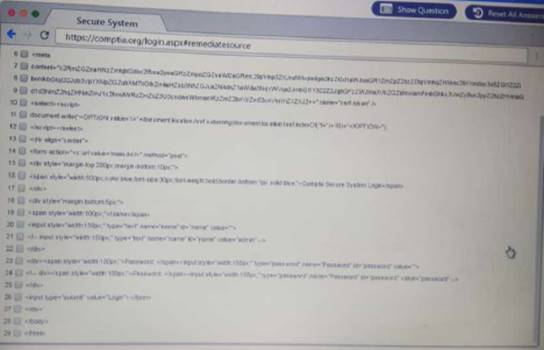
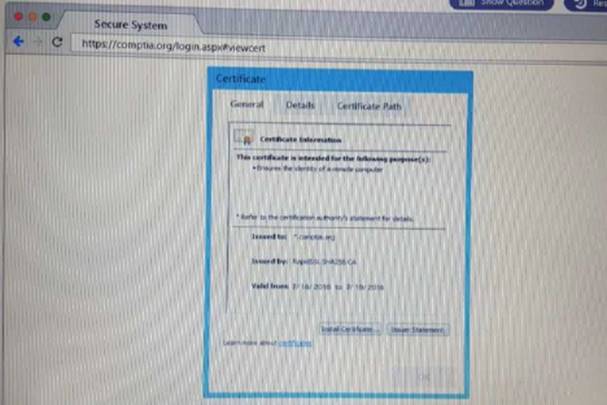
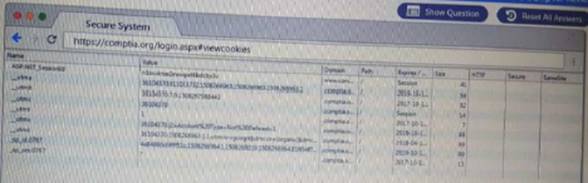
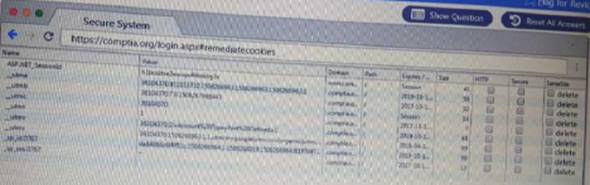
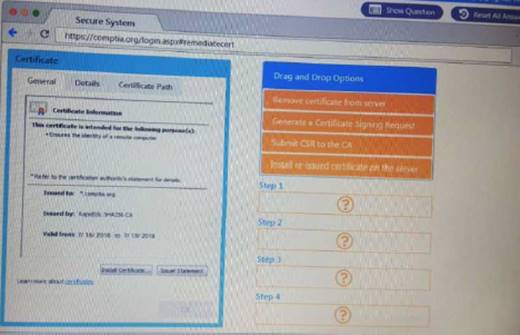
Solution: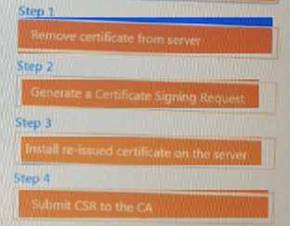
Does this meet the goal?
Correct Answer:A