Online PCNSA Practice TestMore Paloalto-Networks Products >
Free Paloalto-Networks PCNSA Exam Dumps Questions
Paloalto-Networks PCNSA: Palo Alto Networks Certified Network Security Administrator
- Get instant access to PCNSA practice exam questions
- Get ready to pass the Palo Alto Networks Certified Network Security Administrator exam right now using our Paloalto-Networks PCNSA exam package, which includes Paloalto-Networks PCNSA practice test plus an Paloalto-Networks PCNSA Exam Simulator.
- The best online PCNSA exam study material and preparation tool is here.
Question 1
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?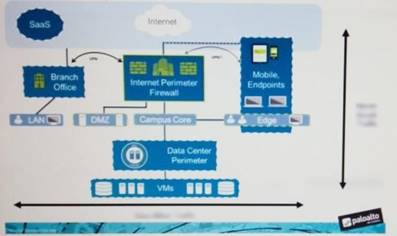
Correct Answer:D
Question 2
DRAG DROP
Match the Palo Alto Networks Security Operating Platform architecture to its description.
Select and Place: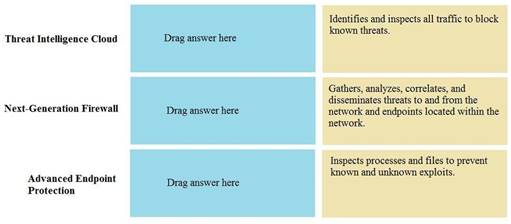
Solution: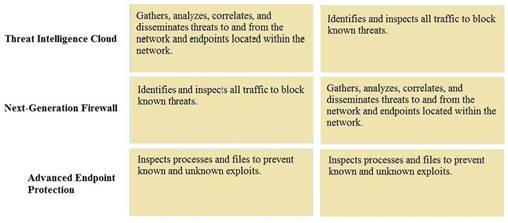
Does this meet the goal?
Correct Answer:A
Question 3
To use Active Directory to authenticate administrators, which server profile is required in the authentication profile?
Correct Answer:C
Question 4
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.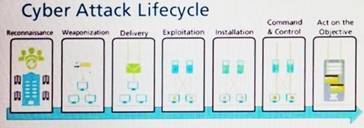
Correct Answer:A
Question 5
Based on the security policy rules shown, ssh will be allowed on which port?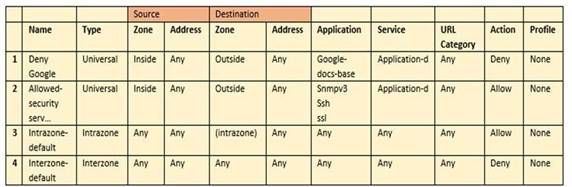
Correct Answer:C
Question 6
Which two App-ID applications will need to be allowed to use Facebook- chat? (Choose two.)
Correct Answer:BC