Question 7
Which two attachments are necessary to connect a transit gateway to an existing VPC with BGP? (Choose two )
Correct Answer:AC
The correct answer is A and C. A transport attachment and a connect attachment are necessary to connect a transit gateway to an existing VPC with BGP.
According to the AWS documentation for Transit Gateway, a transit gateway is a network transit hub that connects VPCs and on-premises networks. To connect a transit gateway to an existing VPC with BGP, you need to do the following steps:
✑ Create a transport attachment. A transport attachment is a resource that connects a VPC or VPN to a transit gateway. You can specify the BGP options for the transport attachment, such as the autonomous system number (ASN) and the BGP peer IP address.
✑ Create a connect attachment. A connect attachment is a resource that enables you to use your own appliance to provide network services for traffic that flows through the transit gateway. You can use a connect attachment to route traffic between the transport attachment and your appliance using GRE tunnels and BGP.
The other options are incorrect because:
✑ A BGP attachment is not a valid type of attachment for a transit gateway. BGP is a protocol that enables dynamic routing between the transit gateway and the VPC or VPN.
✑ A GRE attachment is not a valid type of attachment for a transit gateway. GRE is a protocol that encapsulates packets for tunneling purposes. GRE tunnels are established between the connect attachment and your appliance.
[Transit Gateways - Amazon Virtual Private Cloud] : [Transit Gateway Connect - Amazon Virtual Private Cloud]
Question 8
How does the immutable infrastructure strategy work in automation?
Correct Answer:C
Immutable infrastructure is a DevOps approach that emphasizes the creation of disposable resources instead of modifying existing ones1. This approach helps to achieve stability, consistency, and predictability in IT operations by reducing the risk of configuration drift and eliminating stateful components1.
One way to implement immutable infrastructure is to use a blue-green deployment strategy, which runs two live environments for configuration changes2. The blue environment is the current production environment, while the green environment is the new version of the application or service. When the green environment is ready, the traffic is switched from blue to green, and the blue environment is destroyed or kept as a backup2. This way, there is no need to update or patch the existing infrastructure, but rather replace it with a new one.
References:
✑ 1: Immutable Infrastructure, Architecture, and its benefits
✑ 2: Introduction to Immutable Infrastructure – BMC Software | Blogs
Question 9
Your administrator instructed you to deploy an Azure vWAN solution to create a connection between the main company site and branch sites to the other company VNETs.
What are the two best connection solutions available between your company headquarters, branch sites, and the Azure vWAN hub? (Choose two.)
Correct Answer:AE
The two best connection solutions available between your company headquarters, branch sites, and the Azure vWAN hub are A. ExpressRoute and E. VPN Gateway.
According to the Azure documentation for Virtual WAN, ExpressRoute and VPN Gateway are two of the supported connectivity options for connecting your on-premises sites and Azure virtual networks to the Azure vWAN hub1. These options provide secure, reliable, and high-performance connectivity for your network traffic.
ExpressRoute is a service that lets you create private connections between your on- premises sites and Azure.ExpressRoute connections do not go over the public internet, and offer more reliability, faster speeds, lower latencies, and higher security than typical connections over the internet2.
VPN Gateway is a service that lets you create encrypted connections between your on- premises sites and Azure over the internet using IPsec/IKE protocols.VPN Gateway also supports point-to-site VPN connections for individual clients using OpenVPN or IKEv2 protocols3.
The other options are incorrect because:
✑ GRE tunnels are not a supported connectivity option for Azure vWAN. GRE is a protocol that encapsulates packets for tunneling purposes.GRE tunnels are established between the connect attachment and your appliance in Azure vWAN4.
✑ SSL VPN connections are not a supported connectivity option for Azure vWAN. SSL VPN is a type of VPN that uses the Secure Sockets Layer (SSL) protocol to secure the connection between a client and a server.SSL VPN is not compatible with the Azure vWAN hub5.
✑ An L2TP connection is not a supported connectivity option for Azure vWAN. L2TP is a protocol that creates a tunnel between two endpoints at the data link layer (Layer 2) of the OSI model.L2TP is not compatible with the Azure vWAN hub.
1:Azure Virtual WAN Overview | Microsoft Learn2: [ExpressRoute overview - Azure ExpressRoute | Microsoft Docs]3: [VPN Gateway - Virtual Networks | Microsoft Azure]4: [Transit Gateway Connect - Amazon Virtual Private Cloud]5: [SSL VPN - Wikipedia] : [Layer 2 Tunneling Protocol - Wikipedia]
Question 10
You are using Red Hat Ansible to change the FortiGate VM configuration.
What is the minimum number of files you must create and which file must you use to configure the target FortiGate IP address?
Correct Answer:B
In using Red Hat Ansible for changing the configuration of a FortiGate VM, the minimum number of files you must create and the file to configure the target FortiGate IP address are:
* B.Create two files and use the hosts file.
✑ Ansible Playbook File (YAML):The playbook file, which is typically a YAML file, contains the desired states and tasks that Ansible will execute on the target hosts.
✑ Inventory File (Hosts):The inventory file, commonly namedhosts, is where you define the target machines, including the FortiGate VM's IP address. Ansible uses this file to determine on which machines to run the playbook.
By creating these two files, you will have the necessary components to configure Ansible for the deployment. The playbook contains the automation tasks, and the hosts file lists the machines where those tasks will be executed.
References:This structure is specified in the Ansible documentation, which details the use of playbooks and inventory files to manage and configure target systems.
Question 11
You have created a TGW route table to route traffic from your spoke VPC to the security VPC where two FortiGate devices are inspecting traffic. Your spoke VPC CIDR block is already propagated to the Transit Gateway (TGW) route table.
Which type of attachment should you use to advertise routes through BGP from the spoke VPC to the security VPC?
Correct Answer:B
A VPC attachment is the type of attachment that allows you to connect a VPC to a TGW and advertise routes through BGP. A VPC attachment creates a VPN connection between the VPC and the TGW, and enables dynamic routing with BGP. A connect attachment is used to connect a VPN or Direct Connect gateway to a TGW. A route attachment is not a valid type of attachment for TGW. A GRE attachment is used to connect a FortiGate device to a TGW using GRE tunnels. References:
✑ Creating the TGW and related resources
✑ Configuring TGW route tables
✑ FortiGate Public Cloud 7.2.0 - Fortinet Documentation
✑ Updating the route table and adding an IAM policy
Question 12
Refer to the exhibit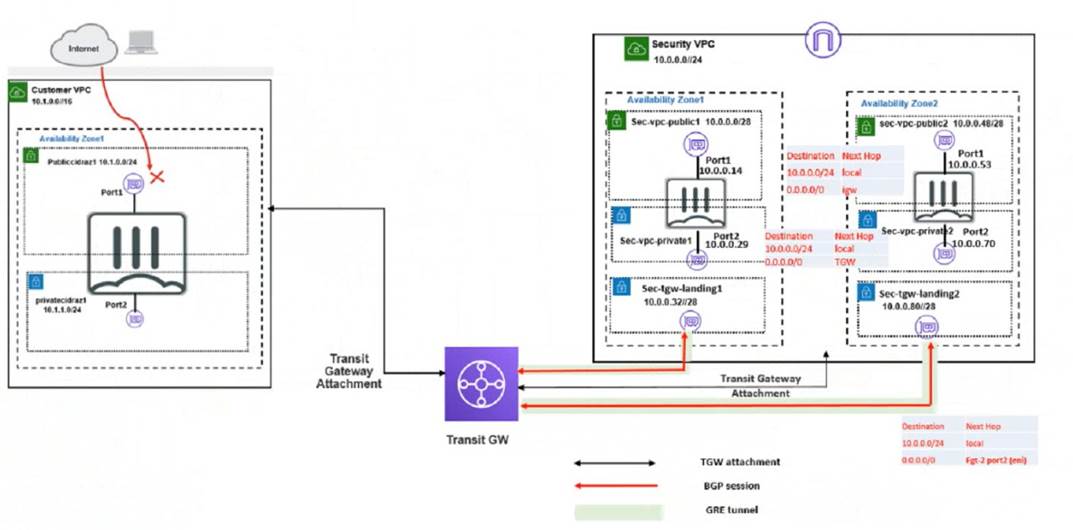
In your Amazon Web Services (AWS), you must allow inbound HTTPS access to the Customer VPC FortiGate VM from the internet However, your HTTPS connection to the FortiGate VM in the Customer VPC is not successful.
Also, you must ensure that the Customer VPC FortiGate VM sends all the outbound Internet traffic through the Security VPC How do you correct this Issue with minimal configuration changes?
(Choose three.)
Correct Answer:BDE
* B. Add route destination 0.0.0.0/0 to target the transit gateway. This will ensure that the Customer VPC FortiGate VM sends all the outbound internet traffic through the Security VPC, where it can be inspected by the Security VPC FortiGate VMs1. The transit gateway is a network device that connects multiple VPCs and on-premises networks in a hub-and-spoke model2. D. Deploy an internet gateway, associate an EIP in the private subnet, edit route tables, and add a new route destination 0.0.0.0/0 to the target internet gateway. This will allow inbound HTTPS access to the Customer VPC FortiGate VM from the internet, by creating a public route for the private subnet where the FortiGate VM is located3. An internet gateway is a service that enables communication between your VPC and the internet4. An EIP is a public IPv4 address that you can allocate to your AWS account and associate with your resources. E. Deploy an internet gateway, associate an EIP in the public subnet, and attach the internet gateway to the Customer VPC. This will also allow inbound HTTPS access to the Customer VPC FortiGate VM from the internet, by creating a public route for the public subnet where the FortiGate VM is located3. This is an alternative solution to option D, depending on which subnet you want to use for the FortiGate VM.
The other options are incorrect because:
✑ Adding a route with your local internet public IP address as the destination and target transit gateway will not allow inbound HTTPS access to the Customer VPC FortiGate VM from the internet, because it will only apply to traffic coming from your specific IP address, not from any other source on the internet1. Moreover, it will not ensure that the outbound internet traffic goes through the Security VPC, because it will only apply to traffic going to your specific IP address, not to any other destination on the internet1.
✑ Adding a route with your local internet public IP address as the destination and target internet gateway will not allow inbound HTTPS access to the Customer VPC FortiGate VM from the internet, because it will bypass the Security VPC and send the traffic directly to the Customer VPC1. Moreover, it will not ensure that the outbound internet traffic goes through the Security VPC, because it will only apply to traffic going to your specific IP address, not to any other destination on the internet1.