Online NSE7_PBC-7.2 Practice TestMore Fortinet Products >
Free Fortinet NSE7_PBC-7.2 Exam Dumps Questions
Fortinet NSE7_PBC-7.2: Fortinet NSE 7 - Public Cloud Security 7.2
- Get instant access to NSE7_PBC-7.2 practice exam questions
- Get ready to pass the Fortinet NSE 7 - Public Cloud Security 7.2 exam right now using our Fortinet NSE7_PBC-7.2 exam package, which includes Fortinet NSE7_PBC-7.2 practice test plus an Fortinet NSE7_PBC-7.2 Exam Simulator.
- The best online NSE7_PBC-7.2 exam study material and preparation tool is here.
Question 1
Refer to the exhibit.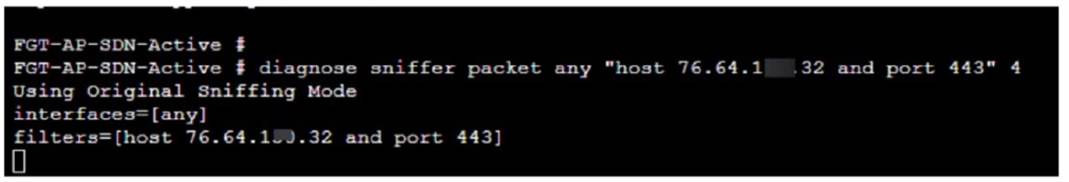
An administrator has deployed a FortiGate VM in Amazon Web Services (AWS) and is trying to access it using its public IP address from their local computer However, the connection is not successful and at the same time FortiGate is not receiving any HTTPS or SSH traffic to its external interface
What should the administrator check for possible issue?
Correct Answer:D
Considering the situation where the administrator is unable to access the FortiGate VM using its public IP address and no traffic is reaching the FortiGate's external interface, the administrator should check: D.Check the inbound network security group rules.
✑ Network Security Group Rules:AWS uses security groups as a virtual firewall that controls inbound and outbound traffic to AWS resources such as EC2 instances. If the FortiGate VM??s public interface is not receiving HTTPS or SSH traffic, it's likely because the inbound security group rules associated with that interface are not allowing access on the necessary ports (HTTPS - port 443, SSH - port 22).
✑ Troubleshooting:The administrator should verify that the security group rules for the FortiGate VM??s network interface allow inbound traffic on the specific ports used for management access. If these rules are absent or misconfigured, the intended traffic will be blocked, resulting in the inability to connect.
References:The role of security groups in network traffic management is a core concept in AWS and is outlined in AWS documentation. Checking security group rules is a standard troubleshooting step when dealing with connectivity issues to AWS resources.
Question 2
What are two main features in Amazon Web Services (AWS) network access control lists (ACLs)? (Choose two.)
Correct Answer:BC
* B. The default network ACL is configured to allow all traffic. This means that when you create a VPC, AWS automatically creates a default network ACL for that VPC, and associates it with all the subnets in the VPC1. By default, the default network ACL allows all inbound and outbound IPv4 traffic and, if applicable, IPv6 traffic1. You can modify the default network ACL, but you cannot delete it1. C. Network ACLs are stateless, and inbound and outbound rules are used for traffic filtering. This means that network ACLs do not keep track of the traffic that they allow or deny, and they evaluate each packet separately1. Therefore, you need to create both inbound and outbound rules for each type of traffic that you want to allow or deny1. For example, if you want to allow SSH traffic from a specific IP address to your subnet, you need to create an inbound rule to allow TCP port 22 from that IP address, and an outbound rule to allow TCP port 1024-65535 (the ephemeral ports) to that IP address2.
The other options are incorrect because:
✑ You can use network ACL and security group at the same time. Network ACL and security group are two different types of security layers for your VPC that can work together to control traffic3. Network ACLacts as a firewall for your subnets, while security group acts as a firewall for your instances3. You can use both of them to create a more granular and effective security policy for your VPC.
✑ Network ACLs are not tied to an instance. Network ACLs are associated with subnets, not instances1. This means that network ACLs apply to all the instances in the subnets that they are associated with1. You cannot associate a network ACL with a specific instance. However, you can associate a security group with a specific instance or multiple instances3.
Question 3
You are adding more spoke VPCs to an existing hub and spoke topology Your goal is to finish this task in the minimum amount of time without making errors.
Which Amazon AWS services must you subscribe to accomplish your goal?
Correct Answer:D
The correct answer is D. CloudWatch and S3.
According to the GitHub repository for the Fortinet aws-lambda-tgw script1, this function requires the following AWS services:
✑ CloudWatch: A monitoring and observability service that collects and processes
events from various AWS resources, including Transit Gateway attachments and route tables.
✑ S3: A scalable object storage service that can store the configuration files and logs
generated by the Lambda function.
By using the Fortinet aws-lambda-tgwscript, you can automate the creation and
configuration of Transit Gateway Connect attachments for your FortiGate devices.This can help you save time and avoid errors when adding more spoke VPCs to an existing hub and spoke topology1.
The other AWS services mentioned in the options are not required for this task. GuardDuty is a threat detection service that monitors for malicious and unauthorized behavior to help protect AWS accounts and workloads. WAF is a web application firewall that helps protect web applications from common web exploits. Inspector is a security assessment service that helps improve the security and compliance of applications deployed on AWS. DynamoDB is a fast and flexible NoSQL database service that can store various types of data.
1:GitHub - fortinet/aws-lambda-tgw
Question 4
Refer to the exhibit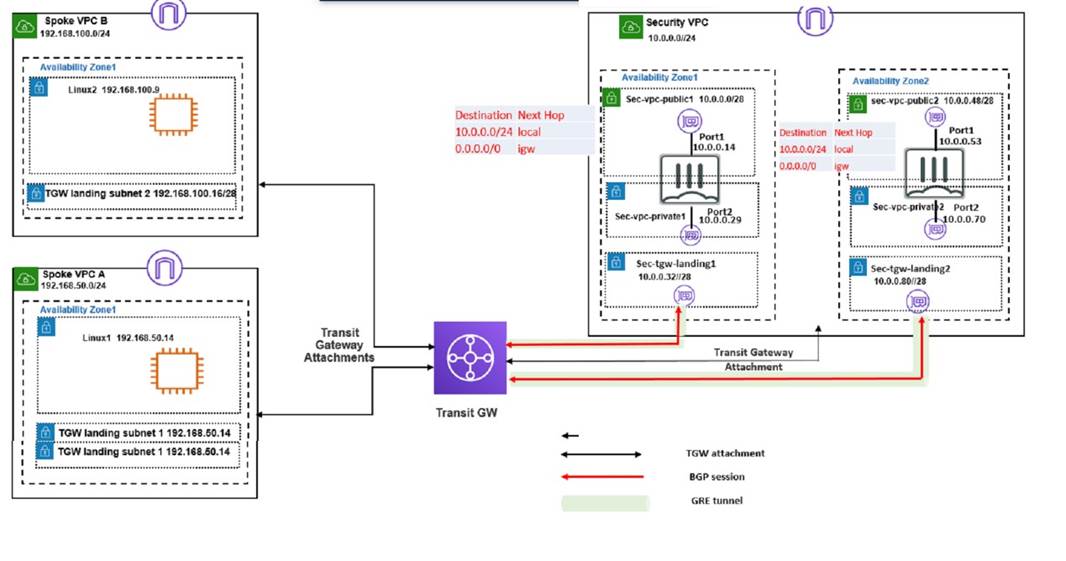
A customer has deployed an environment in Amazon Web Services (AWS) and is now trying to send outbound traffic from the Linux1 and Linux2 instances to the internet through the security VPC (virtual private cloud). The FortiGate policies are configured to allow all outbound traffic; however, the traffic is not reaching the FortiGate internal interface. Assume there are no issues with the Transit Gateway (TGW) configuration
Which two settings must the customer add to correct the issue? (Choose two.)
Correct Answer:BC
The correct answer is B and C. Both landing subnets in the spoke VPCs must have a 0.0.0.0/0 traffic route to the TGW. Both landing subnets in the security VPC must have a 0.0.0.0/0 traffic route to the FortiGate port2.
According to the AWS documentation for Transit Gateway, a transit gateway is a network transit hub that connects VPCs and on-premises networks. To send outbound traffic from the Linux instances to the internet through the security VPC, you need to do the following steps:
✑ In the main subnet routing table in the spoke VPCs, add a new route with destination 0.0.0.0/0, next hop TGW. This route directs all traffic from the Linux instances to the TGW, which can then forward it to the appropriate destination based on the TGW route table.
✑ In the main subnet routing table in the security VPC, add a new route with destination 0.0.0.0/0, next hop FortiGate port2. This route directs all traffic from the TGW to the FortiGate internal interface, where it can be inspected and allowed by the FortiGate policies.
The other options are incorrect because:
✑ Adding a 0.0.0.0/0 traffic route to the Internet Gateway (IGW) in the spoke VPCs is not correct, as this would bypass the TGW and the security VPC and send all traffic directly to the internet.
✑ Adding a 0.0.0.0/0 traffic route to the TGW in all the VPCs is not necessary, as only the spoke VPCs need to send traffic to the TGW. The security VPC needs to send traffic to the FortiGate port2.
Transit Gateways - Amazon Virtual Private Cloud:Fortinet Documentation Library - Deploying FortiGate VMs on AWS
Question 5
What are three important steps required to get Terraform ready using Microsoft Azure Cloud Shell? (Choose three.)
Correct Answer:ADE
To get Terraform ready using Microsoft Azure Cloud Shell, you need to perform the following steps:
✑ Set up a storage account in Azure. This is required to store the Terraform state file in a blob container, which enables collaboration and persistence of the infrastructure configuration1.
✑ Use the wget (terraform_version) command to upload Terraform. This command downloads the latest version of Terraform from the official website and saves it as a zip file in the current directory2.
✑ Move the Terraform file to the bin directory. This step extracts the Terraform executable from the zip file and moves it to the bin directory, which is part of the PATH environment variable. This allows you to run Terraform commands from any directory in Cloud Shell2.
The other options are incorrect because:
✑ You do not need to use the -O command to download Terraform. This command is used to specify a different output file name for the downloaded file, but it is not necessary for this task3.
✑ You do not need to subscribe to Terraform in Azure. Terraform is an open-source tool that can be used with any cloud provider, and there is no subscription or registration required to use it with Azure4. References:
✑ Updating the route table and adding an IAM policy
✑ Configure Terraform in Azure Cloud Shell with Bash
✑ wget(1) - Linux man page
✑ Terraform by HashiCorp
Question 6
Refer to the exhibit.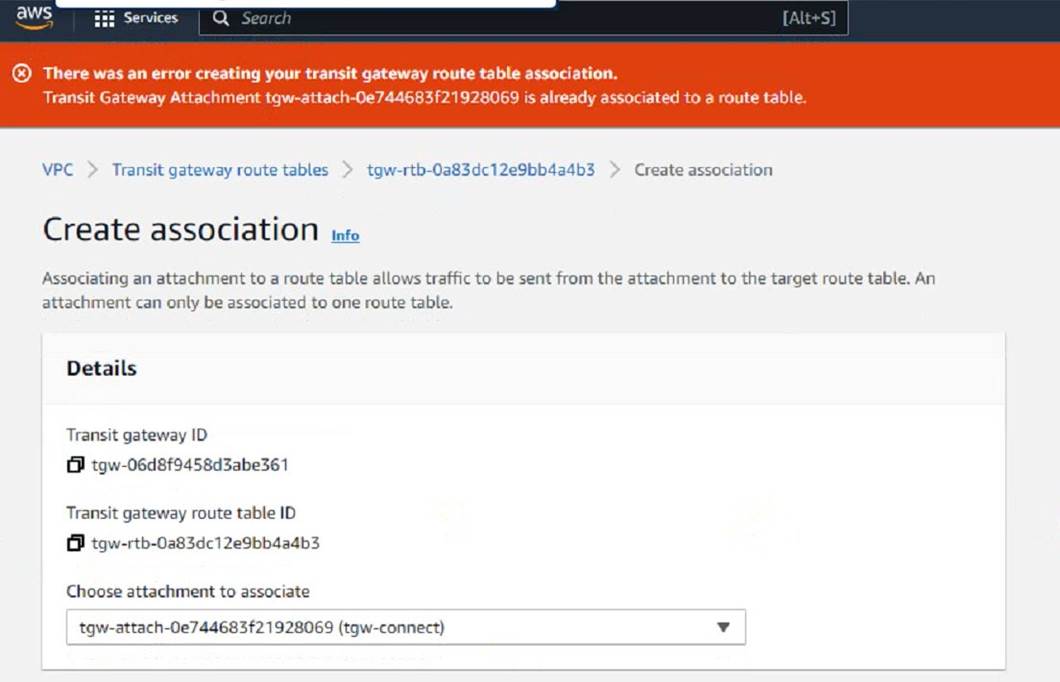
You are configuring a second route table on a Transit Gateway to accommodate east-west traffic inspection between two VPCs_ However, you are getting an error during the transit gateway route table association With the Connect attachment.
Which action Should you take to fulfill your requirement?
Correct Answer:D
The error message indicates that the Connect attachment is already associated with another transit gateway route table. You cannot associate the same attachment with more than one route table. However, you can propagate the same attachment to multiple route tables. Therefore, to fulfill your requirement of configuring a second route table for east- west traffic inspection between two VPCs, you need to create a propagation with the Connect attachment in the second route table. This will allow the second route table to learn the routes from the Connect attachment and forward the traffic to the
securityVPC1. You also need to associate the second route table with the Transport attachment, which is the transit gateway attachment for the security VPC1. References:
✑ Transit gateway route tables - Amazon VPC | AWS Documentation
✑ Getting started with transit gateways - Amazon VPC | AWS Documentation
✑ Configuring TGW route tables | FortiGate Public Cloud 7.4.0 | Fortinet Document Library