Question 7
Refer to the exhibit.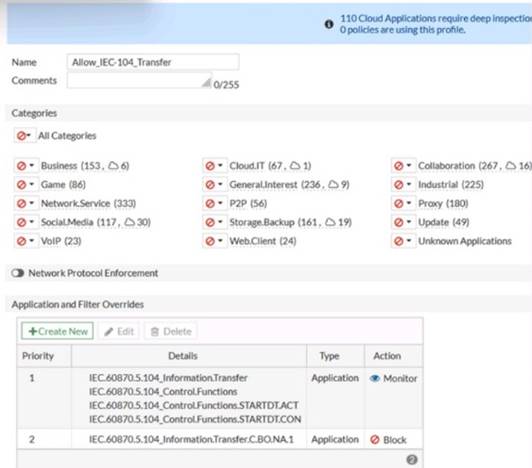
An OT network security audit concluded that the application sensor requires changes to ensure the correct security action is committed against the overrides filters.
Which change must the OT network administrator make?
Correct Answer:C
According to the Fortinet NSE 7 - OT Security 6.4 exam guide1, the application sensor settings allow you to configure the security action for each application category andnetwork protocol override. The security action determines how the FortiGate unit handles traffic that matches the application category or network protocol override. The security action can be one of the following:
✑ Allow: The FortiGate unit allows the traffic without any further inspection.
✑ Monitor: The FortiGate unit allows the traffic and logs it for monitoring purposes.
✑ Block: The FortiGate unit blocks the traffic and logs it as an attack.
The priority of the network protocol override determines the order in which the FortiGate unit applies the security action to the traffic. The lower the priority number, the higher the priority. For example, a priority of 1 is higher than a priority of 10.
In the exhibit, the application sensor has the following settings:
✑ The industrial category has a security action of allow, which means that the FortiGate unit will not inspect or log any traffic that belongs to this category.
✑ The IEC.60870.5.104 Information.Transfer network protocol override has a
security action of block, which means that the FortiGate unit will block and log any traffic that matches this protocol.
✑ The IEC.60870.5.104 Control.Functions network protocol override has a security
action of monitor, which means that the FortiGate unit will allow and log any traffic that matches this protocol.
✑ The IEC.60870.5.104 Start/Stop network protocol override has a security action of
allow, which means that the FortiGate unit will not inspect or log any traffic that matches this protocol.
✑ The IEC.60870.5.104 Transfer.C.BO.NA.1 network protocol override has a
security action of block, which means that the FortiGate unit will block and log any traffic that matches this protocol.
The problem with these settings is that the IEC.60870.5.104 Transfer.C.BO.NA.1 network protocol override has a lower priority than the IEC.60870.5.104 Information.Transfer network protocol override. This means that if the traffic matches both protocols, the FortiGate unit will apply the security action of the higher priority override, which is block. However, the IEC.60870.5.104 Transfer.C.BO.NA.1 protocol is used to transfer binary outputs, which are essential for controlling OT devices. Therefore, blocking this protocol could have negative consequences for the OT network.
To fix this issue, the OT network administrator must set the priority of the IEC.60870.5.104 Transfer.C.BO.NA.1 network protocol override to 1, which is higher than the priority of the IEC.60870.5.104 Information.Transfer network protocol override. This way, the FortiGate unit will apply the security action of the lower priority override, which is allow, to the traffic that matches both protocols. This will ensure that the FortiGate unit does not block the traffic that is used to transfer binary outputs, while still blocking the traffic that is used to transfer information.
1: NSE 7 Network Security Architect - Fortinet
Question 8
You are investigating a series of incidents that occurred in the OT network over past 24 hours in FortiSIEM.
Which three FortiSIEM options can you use to investigate these incidents? (Choose three.)
Correct Answer:CDE
Question 9
What triggers Layer 2 polling of infrastructure devices connected in the network?
Correct Answer:D
Question 10
What are two benefits of a Nozomi integration with FortiNAC? (Choose two.)
Correct Answer:AD
The two benefits of a Nozomi integration with FortiNAC are enhanced point of connection details and importation and classification of hosts. Enhanced point of connection details allows for the identification and separation of traffic from multiple points of connection, such as Wi-Fi, wired, cellular, and VPN. Importation and classification of hosts allows for the automated importing and classification of host and device information into FortiNAC. This allows for better visibility and control of the network.
Question 11
Refer to the exhibit.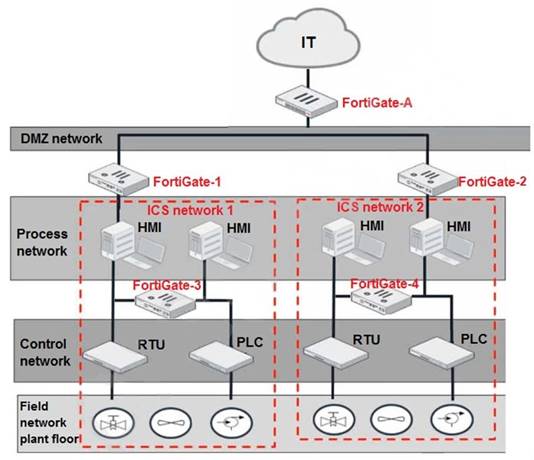
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
Correct Answer:AC
Question 12
Refer to the exhibit.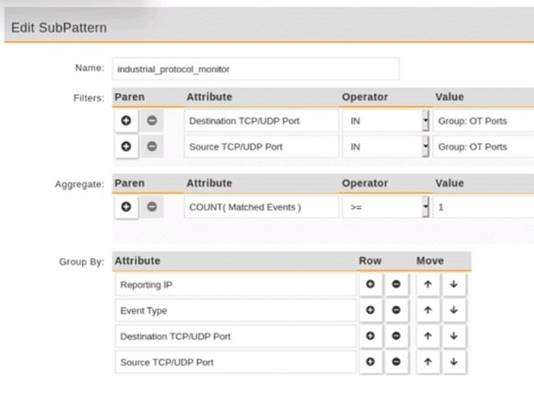
An operational technology rule is created and successfully activated to monitor the Modbus protocol on FortiSIEM. However, the rule does not trigger incidents despite Modbus traffic and application logs being received correctly by FortiSIEM.
Which statement correctly describes the issue on the rule configuration?
Correct Answer:B