Online NSE7_OTS-6.4 Practice TestMore Fortinet Products >
Free Fortinet NSE7_OTS-6.4 Exam Dumps Questions
Fortinet NSE7_OTS-6.4: Fortinet NSE 7 - OT Security 6.4
- Get instant access to NSE7_OTS-6.4 practice exam questions
- Get ready to pass the Fortinet NSE 7 - OT Security 6.4 exam right now using our Fortinet NSE7_OTS-6.4 exam package, which includes Fortinet NSE7_OTS-6.4 practice test plus an Fortinet NSE7_OTS-6.4 Exam Simulator.
- The best online NSE7_OTS-6.4 exam study material and preparation tool is here.
Question 1
When you create a user or host profile, which three criteria can you use? (Choose three.)
Correct Answer:ADE
Question 2
Which three methods of communication are used by FortiNAC to gather visibility information? (Choose three.)
Correct Answer:ACD
Question 3
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
Correct Answer:BC
Ref: https://docs.fortinet.com/document/fortianalyzer/7.0.0/administration-guide/268882/fortisoc
Question 4
What triggers Layer 2 polling of infrastructure devices connected in the network?
Correct Answer:D
Question 5
Refer to the exhibit, which shows a non-protected OT environment.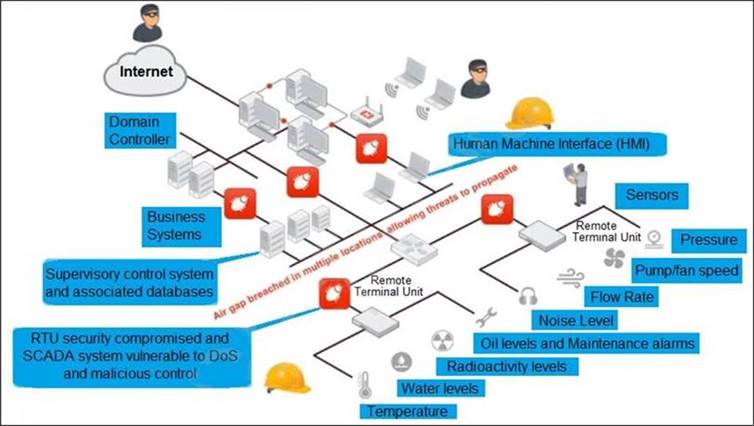
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
Correct Answer:ACD
Question 6
Refer to the exhibit and analyze the output.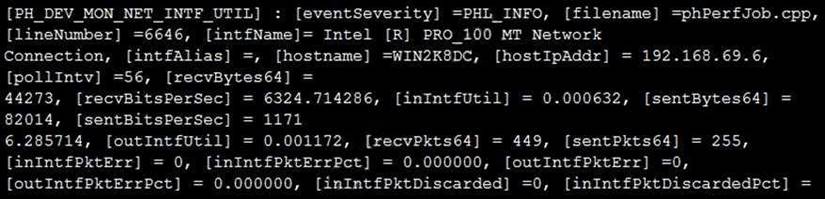
Which statement about the output is true?
Correct Answer:A