Online NSE6_FWF-6.4 Practice TestMore Fortinet Products >
Free Fortinet NSE6_FWF-6.4 Exam Dumps Questions
Fortinet NSE6_FWF-6.4: Fortinet NSE 6 - Secure Wireless LAN 6.4
- Get instant access to NSE6_FWF-6.4 practice exam questions
- Get ready to pass the Fortinet NSE 6 - Secure Wireless LAN 6.4 exam right now using our Fortinet NSE6_FWF-6.4 exam package, which includes Fortinet NSE6_FWF-6.4 practice test plus an Fortinet NSE6_FWF-6.4 Exam Simulator.
- The best online NSE6_FWF-6.4 exam study material and preparation tool is here.
Question 1
Refer to the exhibits.
Exhibit A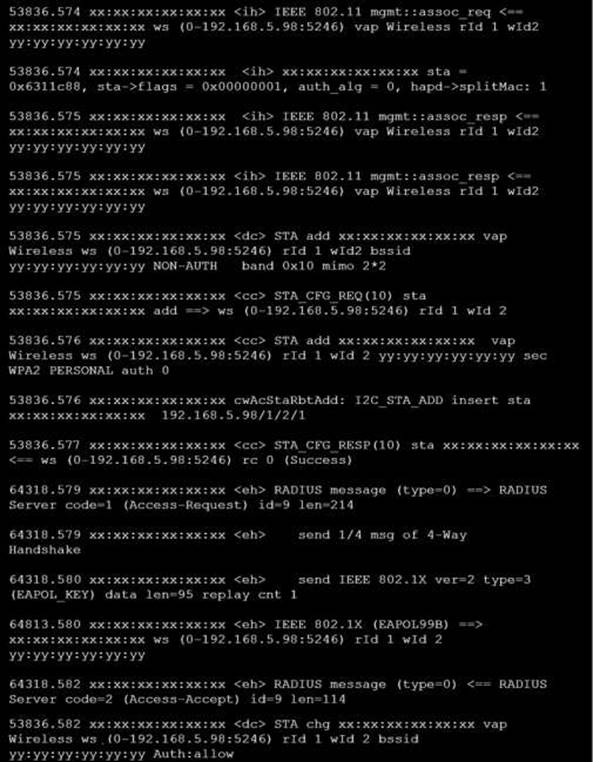
Exhibit B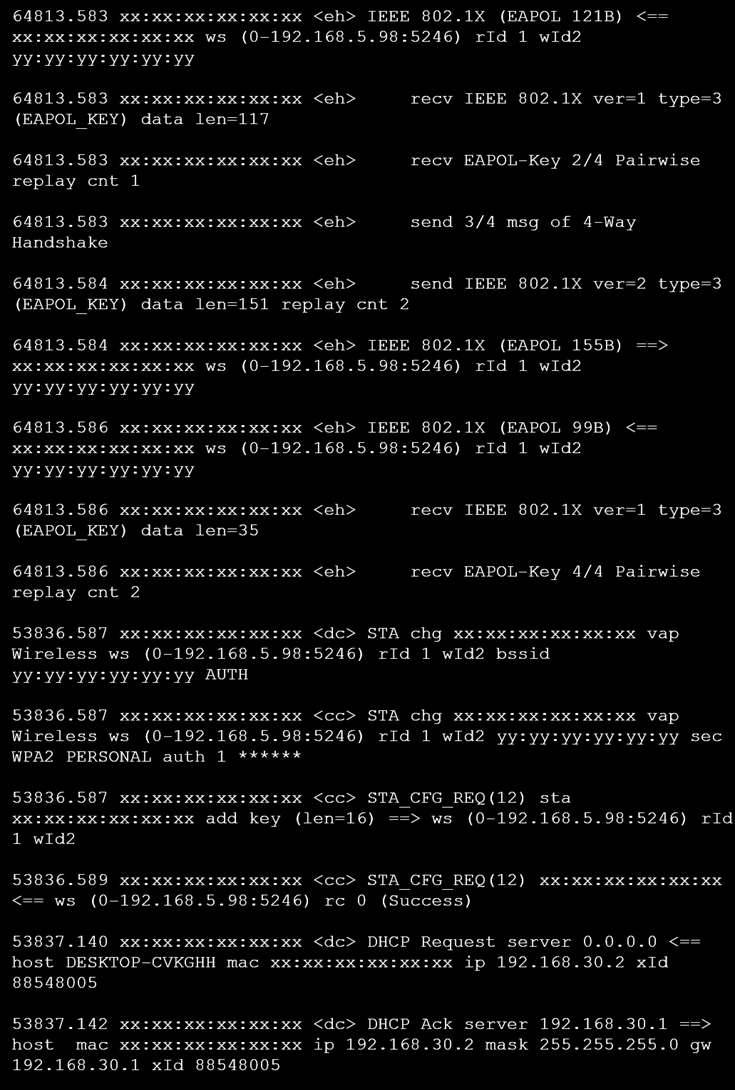
The exhibits show the diagnose debug log of a station connection taken on the controller CLI. Which security mode is used by the wireless connection?
Correct Answer:C
Question 2
When deploying a wireless network that is authenticated using EAP PEAP, which two configurations are required? (Choose two.)
Correct Answer:BD
Question 3
As a network administrator, you are responsible for managing an enterprise secure wireless LAN. The controller is based in the United States, and you have been asked to deploy a number of managed APs in a remote office in Germany.
What is the correct way to ensure that the RF channels and transmission power limits are appropriately configured for the remote APs?
Correct Answer:C
Question 4
What type of design model does FortiPlanner use in wireless design project?
Correct Answer:B
Question 5
Which administrative access method must be enabled on a FortiGate interface to allow APs to connect and function?
Correct Answer:A
Question 6
Six APs are located in a remotely based branch office and are managed by a centrally hosted FortiGate. Multiple wireless users frequently connect and roam between the APs in the remote office.
The network they connect to, is secured with WPA2-PSK. As currently configured, the WAN connection between the branch office and the centrally hosted FortiGate is unreliable.
Which configuration would enable the most reliable wireless connectivity for the remote clients?
Correct Answer:A