Question 7
Where are logical network values defined?
Correct Answer:A
In FortiNAC, logical networks are an integral part of device management and network segmentation. These logical networks are defined and appear within the model configuration of each infrastructure device that is modeled in the topology tree. The configuration allows for the assignment of unique names and, optionally, descriptions to each logical network, thereby clarifying their purpose or use within the network infrastructure.
References: FortiNAC 7.2 Study Guide, Logical Networks Security Fabric and Firewall Tags section.
Question 8
Refer to the exhibit.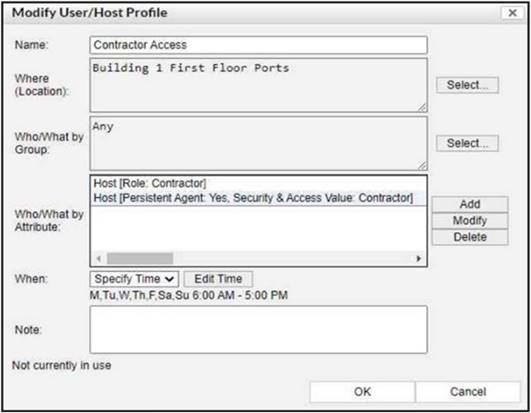
If a host is connected to a port in the Building 1 First Floor Ports group, what must also be true to match this user/host profile?
Correct Answer:D
Looking at the provided exhibit which shows the Modify User/Host Profile window, the following must be true for a host to match the user/host profile:
✑ The host must be connected to a port within the "Building 1 First Floor Ports" group.
✑ The host must fulfill at least one of the following attributes:
✑ The host must be connected between the specified times of 6 AM and 5 PM on any day of the week.
The profile specifies that the host can match the profile by having any one of the listed attributes (Role as Contractor, Persistent Agent installed with specific security & access value), and the time condition must also be met. Therefore, the correct answer is D, which includes "or" conditions for the role value and persistent agent and specifies the correct time frame.
Question 9
When configuring isolation networks in the configuration wizard, why does a Layer 3 network type allow for more than one DHCP scope for each isolation network type?
Correct Answer:A
Question 10
Where do you look to determine which network access policy, if any is being applied to a particular host?
Correct Answer:A
To determine which network access policy is applied to a particular host, you should look at the Policy Details window. This window provides information about the types of policies applied (such as Network Access, Authentication, Supplicant, etc.), including the profile name, policy name, configuration name, and any settings that make up the configuration.
FortiNAC p 382: "Under Network Access Settings - Policy Name - Name of the Network Access Policy that currently applies to the host."
Question 11
Refer to the exhibit, and then answer the question below.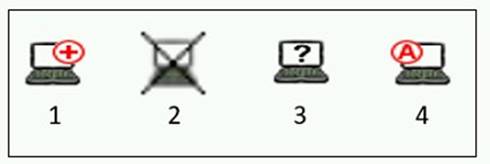
Which host is rogue?
Correct Answer:B
Reference: https://docs.fortinet.com/document/fortinac/8.6.0/administration-guide/283146/evaluating-rogue-hosts
Question 12
How are logical networks assigned to endpoints?
Correct Answer:A
Logical networks are assigned to endpoints through device profiling rules in FortiNAC. These networks appear in device Model Configuration views and are used for endpoint isolation based on the endpoint’s state or status