Online NSE6_FNC-7.2 Practice TestMore Fortinet Products >
Free Fortinet NSE6_FNC-7.2 Exam Dumps Questions
Fortinet NSE6_FNC-7.2: Fortinet NSE 6 - FortiNAC 7.2
- Get instant access to NSE6_FNC-7.2 practice exam questions
- Get ready to pass the Fortinet NSE 6 - FortiNAC 7.2 exam right now using our Fortinet NSE6_FNC-7.2 exam package, which includes Fortinet NSE6_FNC-7.2 practice test plus an Fortinet NSE6_FNC-7.2 Exam Simulator.
- The best online NSE6_FNC-7.2 exam study material and preparation tool is here.
Question 1
Which group type can have members added directly from the FortiNAC Control Manager?
Correct Answer:B
The study guide explains that there are six different types of groups in FortiNAC, including device, host, IP phone, port, user, and administrator groups. Groups created by administrative users or imported as a result of an LDAP integration can be used to organize elements but do not enforce any type of control or functionality directly
Question 2
When FortiNAC passes a firewall tag to FortiGate, what determines the value that is passed?
Correct Answer:B
Question 3
View the command and output.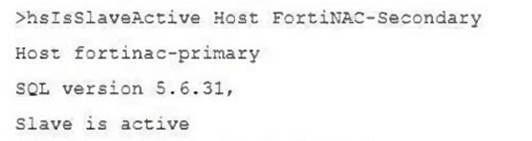
What is the state of database replication?
Correct Answer:D
The command and output shown in the exhibit indicate that the host FortiNAC-Secondary is referencing FortiNAC-Primary, and it states "Slave is active." In database replication terminology within a high availability setup, the term "Slave is active" typically means that the secondary server (slave) is actively receiving data from the primary server (master). This implies that the synchronization process from the primary to the secondary database has been successful and is currently active.
References
✑ FortiNAC 7.2 Study Guide, Security Policies section
Question 4
View the command and output shown in the exhibit.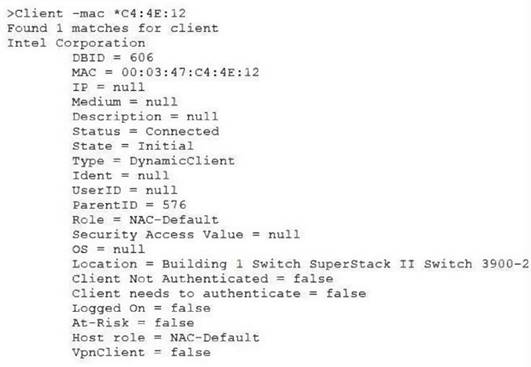
What is the current state of this host?
Correct Answer:A
The exhibit's command and output detail various attributes for a specific host, including the MAC address, connection status, and various other parameters. The status "Connected" and state "Initial" indicate that the host has been detected on the network but has not yet completed any authentication process. The lines "Client Not Authenticated = true" and "Client needs to authenticate = false" suggest that the host has not yet been authenticated. Therefore, the current state of the host is "Not authenticated," since there is a clear indication that the authentication process has not been completed for this host.
Question 5
Where do you look to determine when and why the FortiNAC made an automated network access change?
Correct Answer:B
Reference: https://docs.fortinet.com/document/fortigate/6.2.3/cookbook/536166/viewing- event-logs
Study Guide p. 356: Any time FortiNAC changes network access for an endpoint, the change is documented on the Port Changes view. This provides an administrator with valuable information when validating control configurations and enforcement.
Question 6
What would occur if both an unknown (rogue) device and a known (trusted) device simultaneously appeared on a port that is a member of the Forced Registration port group?
Correct Answer:C
When a rogue device connects to a port in the Forced Registration port group, FortiNAC's response is to isolate that device by moving it to a registration captive network. This is part of FortiNAC's state-based control mechanism, where the system acts based on the state of the device (normal, rogue, etc.) and the group or port it is connected to. In this specific scenario, the focus is on the isolation of the rogue device, and the guide does not explicitly detail the simultaneous handling of the normal device.
References: FortiNAC 7.2 Study Guide, State-Based Control section.