Question 13
Refer to the exhibit showing a debug flow output.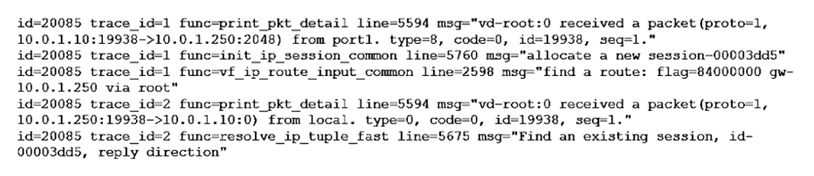
What two conclusions can you make from the debug flow output? (Choose two.)
Correct Answer:AC
Question 14
Refer to the exhibit.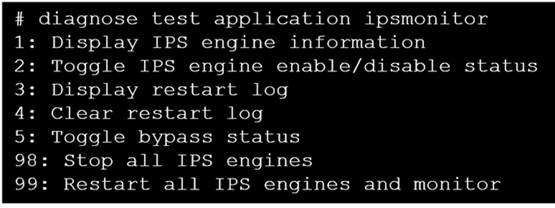
Examine the intrusion prevention system (IPS) diagnostic command.
Which statement is correct If option 5 was used with the IPS diagnostic command and the outcome was a decrease in the CPU usage?
Correct Answer:A
Question 15
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).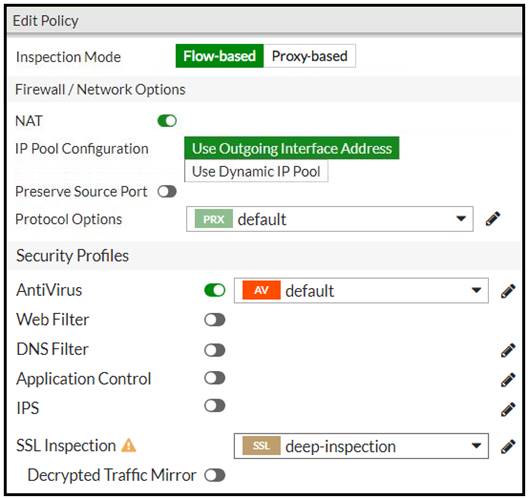
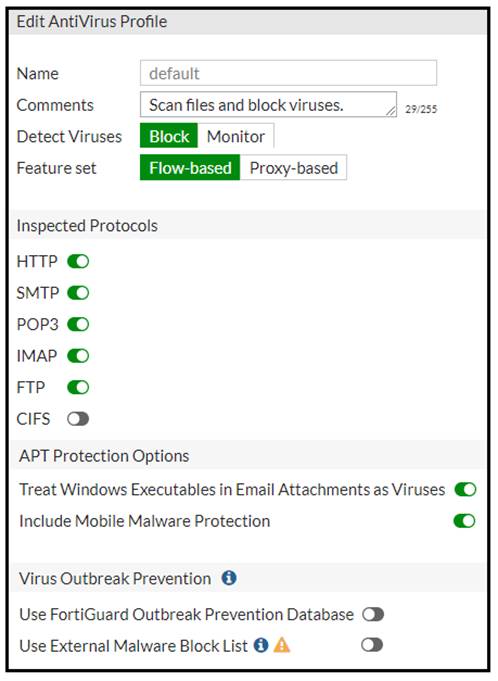
Which statement is correct if a user is unable to receive a block replacement message when downloading an infected file for the first time?
Correct Answer:B
· "ONLY" If the virus is detected at the "START" of the connection, the IPS engine sends the block replacement message immediately
· When a virus is detected on a TCP session (FIRST TIME), but where "SOME PACKETS" have been already forwarded to the receiver, FortiGate "resets the connection" and does not send the last piece of the file. Although the receiver got most of the file content, the file has been truncated and therefore, can't be opened. The IPS engine also caches the URL of the infected file, so that if a "SECOND ATTEMPT" to transmit the file is made, the IPS engine will then send a block replacement message to the client instead of scanning the file again.
In flow mode, the FortiGate drops the last packet killing the file. But because of that the block replacement message cannot be displayed. If the file is attempted to download again the block message will be shown.
Question 16
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
Correct Answer:C
https://docs.fortinet.com/document/fortigate/5.6.0/cookbook/38324/ngfw-policy-based-mode
Question 17
Which two statements explain antivirus scanning modes? (Choose two.)
Correct Answer:BC
An antivirus profile in full scan mode buffers up to your specified file size limit. The default is 10 MB. That is large enough for most files, except video files. If your FortiGate model has more RAM, you may be able to increase this threshold. Without a limit, very large files could exhaust the scan memory. So, this threshold balances risk and performance. Is this tradeoff unique to FortiGate, or to a specific model? No. Regardless of vendor or model, you must make a choice. This is because of the difference between scans in theory, that have no limits, and scans on real-world devices, that have finite RAM. In order to detect 100% of malware regardless of file size, a firewall would need infinitely large RAM--something that no device has in the real world. Most viruses are very small. This table shows a typical tradeoff. You can see that with the default 10 MB threshold, only 0.01% of viruses pass through.
Question 18
Refer to the exhibits.
The exhibits contain a network diagram, and virtual IP, IP pool, and firewall policies configuration information.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
The first firewall policy has NAT enabled using IP pool.
The second firewall policy is configured with a VIP as the destination address.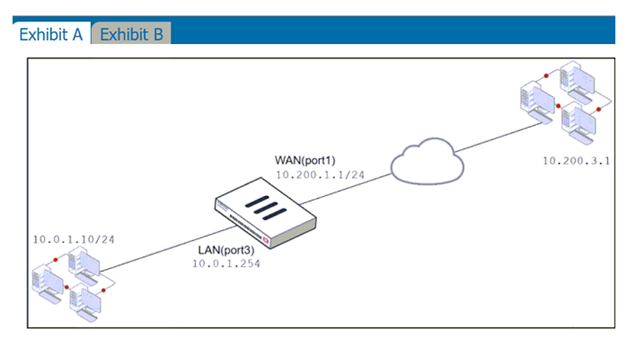
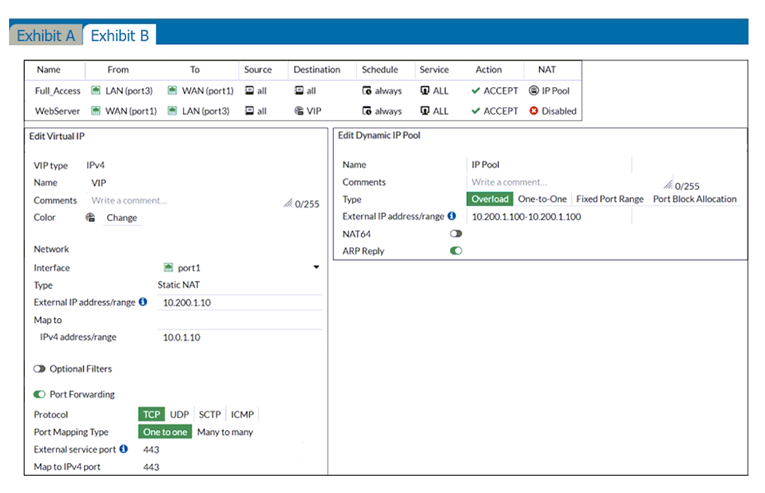
Which IP address will be used to source NAT (SNAT) the internet traffic coming from a workstation with the IP address 10.0.1.10?
Correct Answer:D