Question 19
- (Exam Topic 2)
You have enabled logging on your FortiGate device for Event logs and all Security logs, and you have set up logging to use the FortiGate local disk.
What is the default behavior when the local disk is full?
Correct Answer:C
Reference: https://docs.fortinet.com/document/fortigate/6.4.0/cli-reference/462620/log-disk-setting
Question 20
- (Exam Topic 2)
The HTTP inspection process in web filtering follows a specific order when multiple features are enabled in the web filter profile.
What order must FortiGate use when the web filter profile has features enabled, such as safe search?
Correct Answer:B
Reference: https://fortinet121.rssing.com/chan-67705148/all_p1.html
Question 21
- (Exam Topic 2)
An administrator has a requirement to keep an application session from timing out on port 80. What two changes can the administrator make to resolve the issue without affecting any existing services running through FortiGate? (Choose two.)
Correct Answer:BC
Question 22
- (Exam Topic 2)
Refer to the exhibit.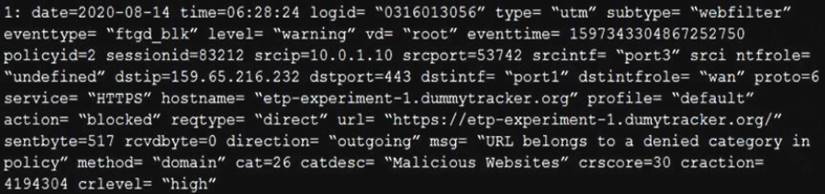
Based on the raw log, which two statements are correct? (Choose two.)
Correct Answer:AC
Question 23
- (Exam Topic 1)
Refer to the exhibit.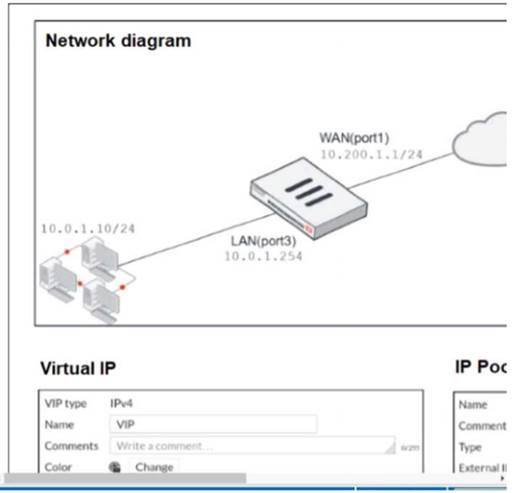
The exhibit contains a network diagram, virtual IP, IP pool, and firewall policies configuration. The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10 .0.1.254. /24. The first firewall policy has NAT enabled using IP Pool.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the internet traffic coming from a workstation with the IP address 10.0.1.10?
Correct Answer:A
Reference:
https://help.fortinet.com/fos60hlp/60/Content/FortiOS/fortigate-firewall/Concepts - Firewall/Static N
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD44529
Question 24
- (Exam Topic 2)
Examine this FortiGate configuration: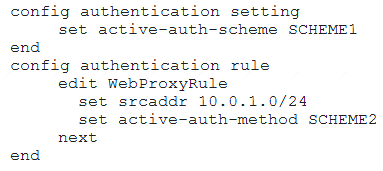
How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?
Correct Answer:D
“What happens to traffic that requires authorization, but does not match any authentication rule? The active and passive SSO schemes to use for those cases is defined under config authentication setting”