Question 43
- (Topic 2)
A network technician is observing the behavior of an unmanaged switch when a new device is added to the network and transmits data. Which of the following BEST describes how the switch processes this information?
Correct Answer:C
The switch processes the data by flooding it out of every port, except the one on which it came in. Flooding is a process where a switch sends a data frame to all ports except the source port when it does not have an entry for the destination MAC address in its MAC address table. Flooding allows the switch to learn the MAC addresses of the devices connected to its ports and update its MAC address table accordingly. Flooding also ensures that the data frame reaches its intended destination, even if the switch does not know its location. References: https://www.cisco.com/c/en/us/support/docs/lan- switching/spanning-tree-protocol/10556-16.html
Question 44
- (Topic 3)
A network engineer is investigating reports of poor performance on a videoconferencing application. Upon reviewing the report, the engineer finds that available bandwidth at the WAN connection is low.
Which Of the following is the MOST appropriate mechanism to handle this issue?
Correct Answer:A
Traffic shaping is a congestion management method that regulates network data transfer by delaying the flow of less important or less desired packets1. Traffic shaping can help to improve the performance of a videoconferencing application by prioritizing its packets over other types of traffic and smoothing out traffic bursts. Traffic shaping can also help to avoid packet loss and ensure fair allocation of bandwidth among different applications or users. Flow control is a mechanism that prevents a sender from overwhelming a receiver with more data than it can handle. Flow control can help to avoid buffer overflow and data loss, but it does not prioritize different types of traffic or smooth out traffic bursts. Flow control operates at the data link layer or the transport layer, while traffic shaping operates at the network layer or above.
NetFlow is a protocol that collects and analyzes network traffic data for monitoring and troubleshooting purposes2. NetFlow can help to identify the sources, destinations, volumes, and types of traffic on a network, but it does not regulate or shape the traffic flow. NetFlow operates at the network layer or above.
Link aggregation is a technique that combines multiple physical links into one logical link for increased bandwidth, redundancy, and load balancing. Link aggregation can help to improve the performance of a videoconferencing application by providing more available bandwidth at the WAN connection, but it does not prioritize different types of traffic or smooth out traffic bursts. Link aggregation operates at the data link layer.
Question 45
- (Topic 3)
A network administrator needs to create a way to redirect a network resource that has been on the local network but is now hosted as a SaaS solution. Which of the following
records should be used to accomplish the task?
Correct Answer:D
CNAME stands for Canonical Name, and it is a type of DNS record that creates an alias for another domain name. A CNAME record can be used to redirect a network resource that has been moved to a different location, such as a SaaS solution. For example, if a web server that was previously hosted on the local network with the domain name www.example.com is now hosted by a SaaS provider with the domain name www.saasprovider.com, a CNAME record can be created to point www.example.com to www.saasprovider.com. This way, the users can still access the web server using the original domain name, and the DNS server will resolve it to the new domain name. References
✑ CNAME is one of the common DNS record types covered in Objective 1.6 of the
CompTIA Network+ N10-008 certification exam1.
✑ CNAME can be used to redirect a network resource that has been moved to a different location23.
✑ CNAME creates an alias for another domain name23.
1: CompTIA Network+ Certification Exam Objectives, page 4 2: DNS Record Types – N10- 008 CompTIA Network+ : 1.6 3: The Official CompTIA Network+ Student Guide (Exam N10-008), Chapter 1, page 32
Question 46
- (Topic 3)
An office area contains two PoE-enabled WAPs. After the area was remodeled, new cable uplinks were installed in the ceiling above the fluorescent lights. However, after the WAPs were reconnected, users reported slowness and application errors. An intern reviewed the network and discovered a lot of CRC errors. A network engineer reviewed the intern's work and realized UTP cabling was used. Which of the following is the MOST likely cause of the CRC errors?
Correct Answer:C
"EMI is a problem when cables are installed near electrical devices, such as air conditioners or fluorescent light fixtures. If a network medium is placed close enough to such a device, the signal within the cable might become corrupt. Network media vary in their resistance to the effects of EMI. Standard unshielded twisted-pair (UTP) cable is susceptible to EMI, whereas fiber cable, with its light transmissions, is resistant to EMI. When deciding on a particular medium, consider where it will run and the impact EMI can have on the installation."
Question 47
- (Topic 3)
A network engineer is installing hardware in a newly renovated data center. Major concerns that were addressed during the renovation induded air circulation, building power redundancy, and the need for continuous monitoring. The network engineer IS creating alerts based on the following operation specifications: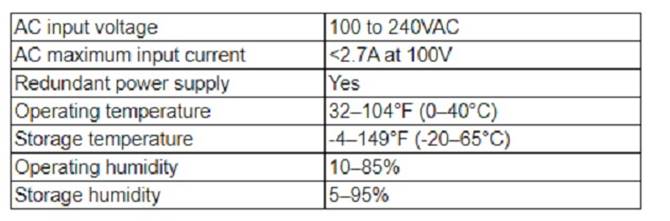
Which of the following should the network engineer configure?
Correct Answer:C
The alert that the network engineer should configure based on the operation specifications is SNMP traps to report when the chassis temperature exceeds 95°F (35°C). SNMP (Simple Network Management Protocol) is a protocol that allows network devices to communicate their status and performance information to a central management system, called an SNMP manager. SNMP traps are messages that are sent by network devices to notify the SNMP manager of an event or condition that requires attention, such as an error, a failure, or a threshold violation. In this case, the network engineer should configure SNMP traps on the network devices to send an alert when their chassis temperature exceeds 95°F (35°C), which is the maximum operating temperature specified in the table. This alert would help the network engineer monitor and troubleshoot any overheating issues that could affect the network performance or availability. References: CompTIA Network+ N10-008 Certification Study Guide, page 228; The Official CompTIA Network+ Student Guide (Exam N10-008), page 8-11.
Question 48
- (Topic 2)
A lab environment hosts Internet-facing web servers and other experimental machines, which technicians use for various tasks A technician installs software on one of the web servers to allow communication to the company's file server, but it is unable to connect to it Other machines in the building are able to retrieve files from the file server. Which of the following is the MOST likely reason the web server cannot retrieve the files, and what should be done to resolve the problem?
Correct Answer:B
The lab environment is located in the DMZ, and traffic to the LAN zone is denied by default. This is the most likely reason why the web server cannot retrieve files from the file server, and the technician can either move the computer to another zone or request an exception from the administrator to resolve the problem. A DMZ (Demilitarized Zone) is a network segment that separates the internal network (LAN) from the external network (Internet). It usually hosts public-facing servers such as web servers, email servers, or FTP servers that need to be accessed by both internal and external users. A firewall is used to control the traffic between the DMZ and the LAN zones, and usually denies traffic from the DMZ to the LAN by default for security reasons. Therefore, if a web server in the DMZ needs to communicate with a file server in the LAN, it would need a special rule or permission from the firewall administrator. References: https://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html