Question 55
- (Topic 3)
Which of the following policies outlines the software and hardware requirements for using personally owned devices to conduct business?
Correct Answer:C
The policy that outlines the software and hardware requirements for using personally owned devices to conduct business is BYOD (Bring Your Own Device). BYOD is a practice that allows employees to use their own devices, such as laptops, tablets, or smartphones, to access corporate resources and applications. BYOD can offer benefits such as increased productivity, flexibility, and satisfaction for employees, as well as reduced costs for employers. However, BYOD also poses challenges and risks, such as security, compatibility, and support issues. Therefore, a BYOD policy is needed to define the rules and expectations for using personal devices in a business environment. A BYOD policy typically covers topics such as device eligibility, security requirements, acceptable use, data ownership, privacy, and liability. References: CompTIA Network+ N10-008 Certification Study Guide, page 362; The Official CompTIA Network+ Student Guide (Exam N10-008), page 14-2.
Question 56
- (Topic 3)
Given the following Information: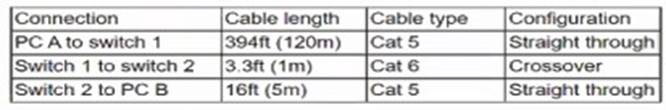
Which of the following would cause performance degradation between PC A and PC B'?
Correct Answer:D
Question 57
- (Topic 3)
An organization set up its offices so that a desktop is connected to the network through a VoIP phone. The VoIP vendor requested that voice traffic be segmented separately from non-voice traffic. Which of the following would allow the organization to configure multiple devices with network isolation on a single switch port?
Correct Answer:A
Question 58
- (Topic 3)
A network technician needs to ensure the company's external mail server can pass reverse lookup checks. Which of the following records would the technician MOST likely configure? (Choose Correct option and give explanation directly from CompTIA Network+ Study guide or documents)
Correct Answer:A
A PTR (Pointer) record is used to map an IP address to a domain name, which is necessary for reverse lookup checks. Reverse lookup checks are performed by external mail servers to verify the identity of the sender of the email. By configuring a PTR record, the network technician can ensure that the company's external mail server can pass these checks. According to the CompTIA Network+ Study Guide, "A PTR record is used to map an IP address to a domain name, and it is often used for email authentication."
Question 59
- (Topic 3)
A technician manages a DHCP scope but needs to allocate a portion of the scope’s subnet for statically assigned devices. Which of the following DHCP concepts would be BEST to use to prevent IP address conflicts?
Correct Answer:B
To prevent IP address conflicts when allocating a portion of a DHCP scope's subnet for statically assigned devices, it is recommended to use the concept of DHCP exclusion ranges. DHCP exclusion ranges allow a DHCP administrator to specify a range of IP addresses within the scope that should not be assigned to DHCP clients. This can be useful in situations where some devices on the network need to be assigned static IP addresses, as it ensures that the statically assigned addresses do not overlap with addresses assigned by the DHCP server. To set up a DHCP exclusion range, the administrator needs to specify the start and end IP addresses of the range, as well as the subnet mask. The DHCP server will then exclude the specified range of addresses from its pool of available addresses, and will not assign them to DHCP clients. By using DHCP exclusion ranges, the technician can ensure that the statically assigned addresses do not conflict with addresses assigned by the DHCP server, and can prevent IP address conflicts on the network.
Anthony Sequeira
"Another frequent configuration you might make in a DHCP implementation is to configure an exclusion range. This is a portion of the address pool that you never want leased out to clients in the network. Perhaps you have numbered your servers 192.168.1.1–192.168.1.10. Because the servers are statically configured with these addresses, you exclude these addresses from the 192.168.1.0/24 pool of addresses."
Mike Meyers
"Exclusion ranges represent an IP address or range of IP addresses from the pool of addresses that are not to be given out by the DHCP server. Exclusions should be made for the static addresses manually configured on servers and router interfaces, so these IP addresses won’t be offered to DHCP clients."
Question 60
- (Topic 3)
A divide-and-conquer approach is a troubleshooting method that involves breaking a complex problem into smaller and more manageable parts, and then testing each part to isolate the cause of the problem. In this scenario, the technician is using a divide-and- conquer approach by pinging the default gateway and DNS server of the workstation, which are two possible sources of connectivity issues. By pinging these devices, the technician can determine if the problem is related to the local network or the external network.
Which of the following most likely requires the use of subinterfaces?
Correct Answer:A
Subinterfaces are logical divisions of a physical interface that allow a router to communicate with multiple networks using a single LAN port. Subinterfaces can have different IP addresses, VLANs, and routing protocols. They are useful for reducing the number of physical interfaces and cables needed, as well as improving network performance and security.
References:
✑ Subinterfaces - CompTIA Network+ N10-008 Domain 1.21 - YouTube1
✑ CompTIA Network+ Certification Exam Objectives, page 92