Online MS-102 Practice TestMore Microsoft Products >
Free Microsoft MS-102 Exam Dumps Questions
Microsoft MS-102: Microsoft 365 Administrator Exam
- Get instant access to MS-102 practice exam questions
- Get ready to pass the Microsoft 365 Administrator Exam exam right now using our Microsoft MS-102 exam package, which includes Microsoft MS-102 practice test plus an Microsoft MS-102 Exam Simulator.
- The best online MS-102 exam study material and preparation tool is here.
Question 1
HOTSPOT - (Topic 6)
HOTSPOT
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint and contains the devices shown in the following table.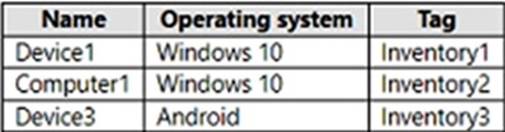
Defender for Endpoint has the device groups shown in the following table.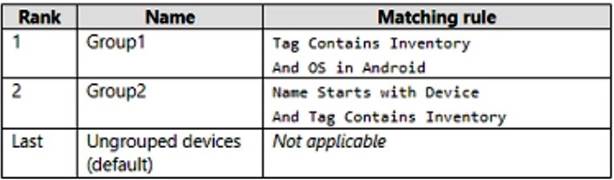
You create an incident email notification rule configured as shown in the following table.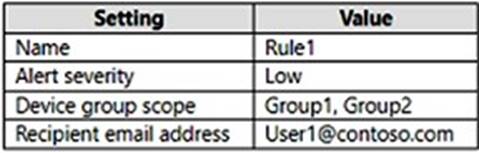
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.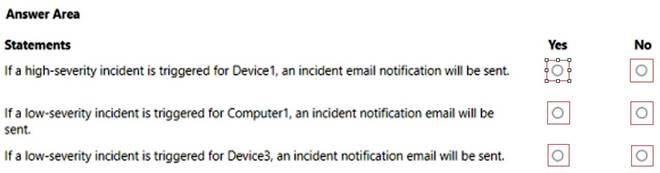
Solution:
Box 1: No
Device1 is in Group2 as Name starts with Device and Tag contains Inventory. However, the Group2 has alert severity low.
Box 2: No
Computer1 does not belong to either Group1 or Group2
Box 3: Yes
Device3 belongs to both Group1 and Group2.
Note: Understanding alert severity
Microsoft Defender Antivirus and Defender for Endpoint alert severities are different because they represent different scopes.
The Microsoft Defender Antivirus threat severity represents the absolute severity of the detected threat (malware), and is assigned based on the potential risk to the individual device, if infected.
Does this meet the goal?
Correct Answer:A
Question 2
HOTSPOT - (Topic 6)
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.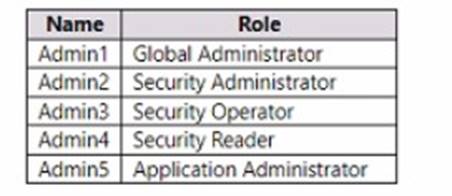
You ate implementing Microsoft Defender for Endpoint
You need to enable role-based access control (RBAQ to restrict access to the Microsoft 365 Defender portal.
Which users can enable RBAC, and winch users will no longer have access to the Microsoft 365 Defender portal after RBAC is enabled? To answer, select the appropriate options in the answer area.
NOTE Each correct selection is worth one point.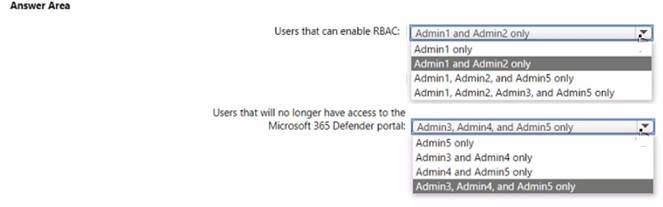
Solution: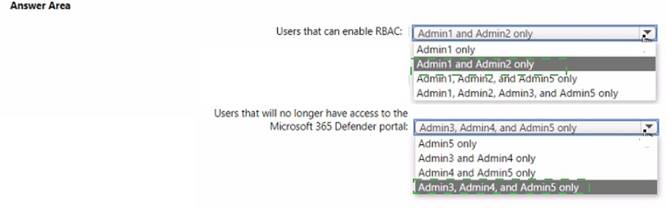
Does this meet the goal?
Correct Answer:A
Question 3
HOTSPOT - (Topic 1)
You need to configure a conditional access policy to meet the compliance requirements. You add Exchange Online as a cloud app.
Which two additional settings should you configure in Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.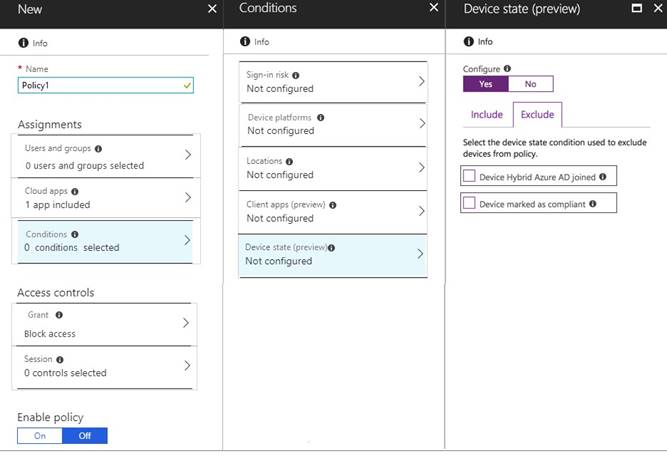
Solution:
References:https://docs.microsoft.com/en-us/intune/create-conditional-access-intune
Does this meet the goal?
Correct Answer:A
Question 4
DRAG DROP - (Topic 2)
You need to meet the requirement for the legal department.
Which three actions should you perform in sequence from the Security & Compliance admin center? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Solution:
References: https://www.sherweb.com/blog/ediscovery-office-365/
Does this meet the goal?
Correct Answer:A
Question 5
HOTSPOT - (Topic 6)
You have a Microsoft 365 subscription that contains the administrative units shown in the following table.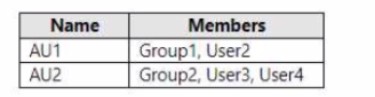
The groups contain the members shown in the following table.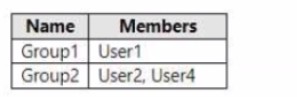
The users are assigned the roles shown in the following table.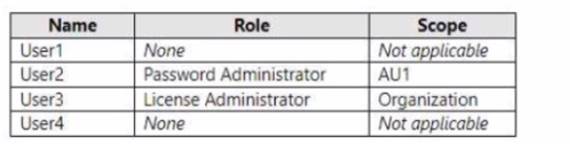
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.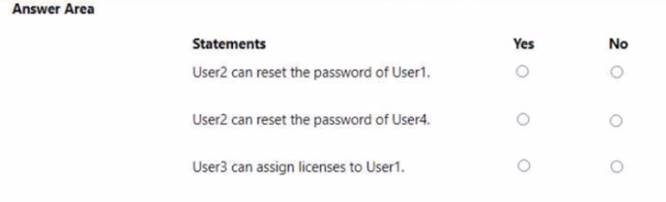
Solution: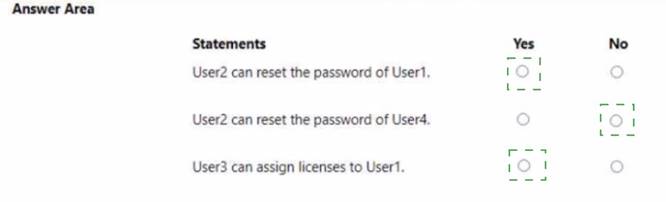
Does this meet the goal?
Correct Answer:A
Question 6
- (Topic 6)
From the Security & Compliance admin center, you create a content export as shown in the exhibit. (Click the Exhibit tab.)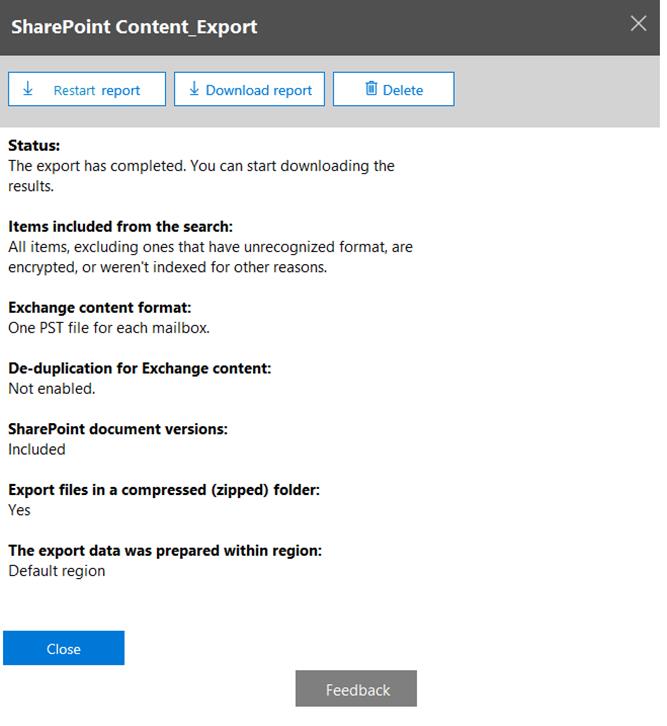
What will be excluded from the export?
Correct Answer:B
Unrecognized file formats are excluded from the search.
Certain types of files, such as Bitmap or MP3 files, don't contain content that can be indexed. As a result, the search indexing servers in Exchange and SharePoint don't perform full-text indexing on these types of files. These types of files are considered to be
unsupported file types.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/partially-indexed-items-in-content-search?view=o365-worldwide
https://docs.microsoft.com/en-us/office365/securitycompliance/export-a-content-search- report