Question 13
- (Exam Topic 4)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
A user named User1 has a computer named Computer1 that runs Windows 10. Computer1 is joined to an Azure Active Directory (Azure AD) tenant named contoso.com. User1 joins Computer1 to contoso.com by using user1@contoso.com.
Computer1 contains a folder named Folder1. Folder1 is in drive C and is shared as Share1. Share1 has the permission shown in the following table.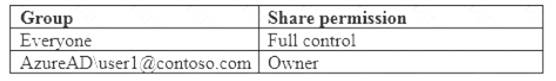
A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using user2@contoso.com.
User2 attempts to access Share1 and receives the following error message: “The username or password is incorrect.”
You need to ensure that User2 can connect to Share1.
Solution: In Azure AD, you create a group named Group1 that contains User1 and User2. You grant Group1 Modify access to Folder1.
Does this meet the goal?
Correct Answer:A
References:
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc75417
Question 14
- (Exam Topic 1)
You need to recommend a solution to configure the employee VPN connections. What should you include in the recommendation?
Correct Answer:D
References:
https://docs.microsoft.com/en-us/windows-server/remote/remote-access/vpn/always-on-vpn/deploy/vpn-deploy
Question 15
- (Exam Topic 1)
You need to recommend a solution to monitor update deployments. What should you include in the recommendation?
Correct Answer:C
References:
https://docs.microsoft.com/en-us/windows/deployment/update/update-compliance-monitor
Question 16
- (Exam Topic 4)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You manage devices that run Windows 10.
Ten sales users will travel to a location that has limited bandwidth that is expensive. The sales users will be at the location for three weeks.
You need to prevent all Windows updates from downloading for the duration of the trip. The solution must not prevent access to email and the Internet.
Solution: From Network & Internet in the Settings app, you set a data limit. Does this meet the goal?
Correct Answer:B
Question 17
- (Exam Topic 4)
You have a computer named Computer1 that runs Windows 10.
You need to modify the Security Settings of Computer1 to meet the following requirements:  A local group named Branch_Admins must be able to view and clear the Security log.
A local group named Branch_Admins must be able to view and clear the Security log. Local users must be prompted to change their password three days before the password expires.
Local users must be prompted to change their password three days before the password expires.
Which two nodes of the Local Group Policy Editor should you access to configure the settings? To answer, select the appropriate nodes in the answer area.
NOTE: Each correct selection is worth one point.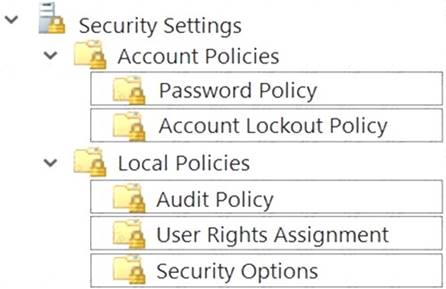
Solution:
Graphical user interface, text, application, chat or text message Description automatically generated
User Rights Assignment > Manage auditing and security log.
Security Options > Interactive Logon: Prompt user to change password before expiration: 3 days.
Does this meet the goal?
Correct Answer:A
Question 18
- (Exam Topic 4)
You have a computer named Computer5 that runs Windows 10 that is used to share documents in a workgroup.
You create three users named User-a, User-b, User-c. The users plan to access Computer5 from the network only.
You have a folder named Data. The Advanced Security Settings for the Data folder are shown in the Security exhibit. (Click the Security Exhibit tab).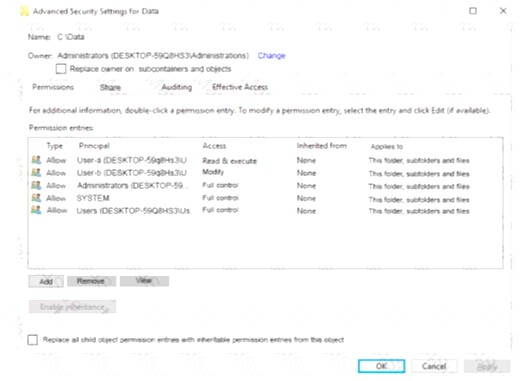
You share the Data folder. The permission for User-a are shown in the User-a exhibit (Click the User-a tab.)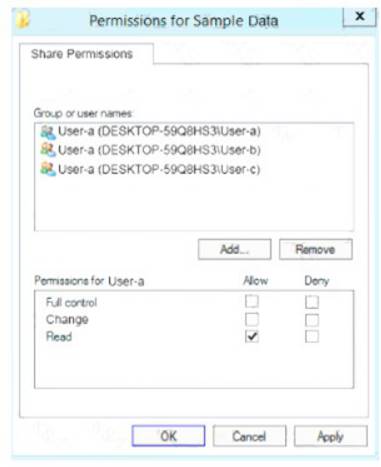
The permissions for user-b are shown in the User-b exhibit. (Click the User-b tab.)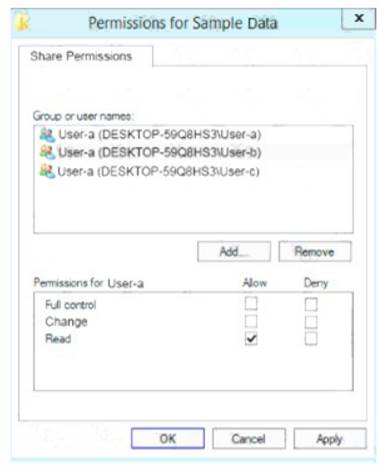
The permissions for user-c are shown in the User-c exhibit. (Click the User-c tab.)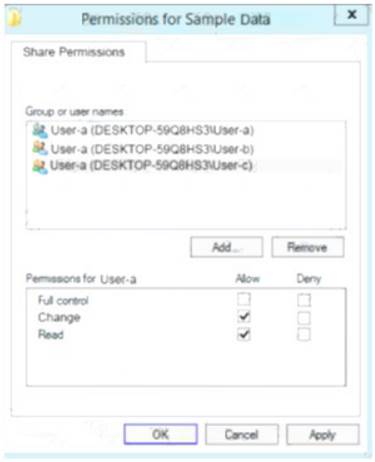
For each of the following statements, select Yes if the statements is true. Otherwise, select No.
NOTE: Reach correct selection is worth one point.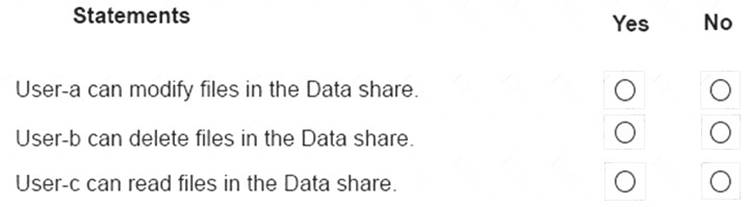
Solution:
No No Yes
Does this meet the goal?
Correct Answer:A