Question 13
Which three actions are required to implement filter-based forwarding? (Choose three.)
Correct Answer:ACE
Filter-Based Forwarding (FBF) in Junos OS allows traffic to be routed based on specific criteria such as source address, rather than just the destination address. This is useful in scenarios like policy routing or providing multiple paths for different types of traffic.
Step-by-Step Breakdown: Instance-Type Forwarding:You must create aninstance-type forwardingrouting instance. This routing instance allows for different routing tables based on the incoming packet filter.
Instance-Type Forwarding:You must create aninstance-type forwardingrouting instance. This routing instance allows for different routing tables based on the incoming packet filter. Command:
Command:
set routing-instances FBF-instance instance-type forwarding Match Filter:You need to create afilterto match the traffic that will be forwarded according to your custom routing policy. This filter is applied to an interface to determine which traffic will use the custom forwarding instance.
Match Filter:You need to create afilterto match the traffic that will be forwarded according to your custom routing policy. This filter is applied to an interface to determine which traffic will use the custom forwarding instance. Command Example:
Command Example:
set firewall family inet filter FBF-filter term 1 from source-address
set firewall family inet filter FBF-filter term 1 then routing-instance FBF-instance RIB Group:ARIB (Routing Information Base) groupis necessary to share routes between the primary routing table and the custom routing instance. This allows FBF traffic to use the routing information from other routing tables.
RIB Group:ARIB (Routing Information Base) groupis necessary to share routes between the primary routing table and the custom routing instance. This allows FBF traffic to use the routing information from other routing tables. Command Example:
Command Example:
set routing-options rib-groups FBF-group import-rib inet.0
set routing-instances FBF-instance routing-options rib-group FBF-group
Juniper Reference: FBF Configuration: Filter-based forwarding requires these specific steps to redirect traffic to a custom routing table based on filter criteria.
FBF Configuration: Filter-based forwarding requires these specific steps to redirect traffic to a custom routing table based on filter criteria.
Question 14
Which statement is correct about areas in OSPF?
Correct Answer:C
InOSPF (Open Shortest Path First), areas are used to segment a network into smaller, more manageable pieces to improve scalability. By dividing a network into areas, OSPF can reduce the size of thelink-state database (LSDB), which helps routers process updates more efficiently.
Step-by-Step Breakdown:
Purpose of OSPF Areas:OSPF areas allow for hierarchical routing within the OSPF domain. Routers in the same area have identical LSDBs, but routers in different areas do not exchange full link-state information. Instead, they exchange summarized routes, which reduces the LSDB size and CPU/memory usage.
Benefits:Reducing the LSDB size improves scalability and ensures faster convergence in larger networks. Area 0 is the backbone area, and all other areas must connect to it, forming a hierarchical structure.
Juniper Reference:
OSPF Configuration: Areas in OSPF are configured to optimize network performance by limiting the scope of link-state advertisements (LSAs) to within an area.
Question 15
Referring to the exhibit, you notice that after committing the configuration, the ae0 and ae1 interfaces appear in a link down state.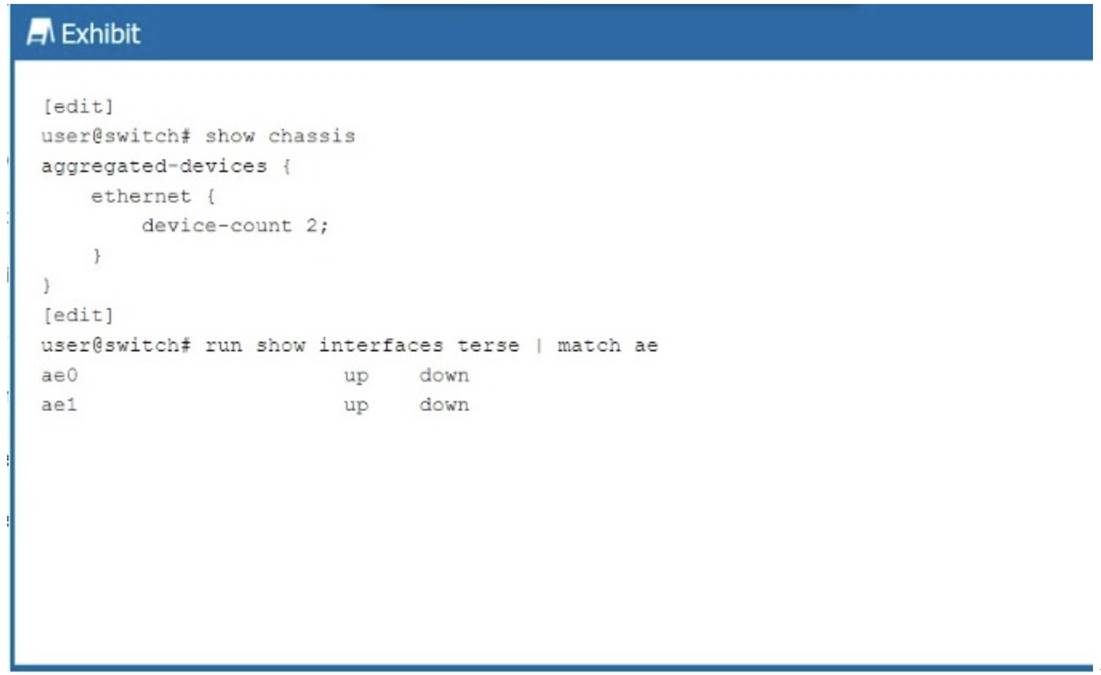
Which statement is correct in this scenario?
Correct Answer:A
In the exhibit, the ae0 and ae1 interfaces are in a link down state. This occurs when no physical interfaces (member interfaces) have been added to the LAG (Link Aggregation Group) interfaces, or the member interfaces are not operational.
Step-by-Step Breakdown:
LAG Configuration:
A LAG interface (aggregated Ethernet interface) is a logical interface that combines multiple physical interfaces for redundancy and increased bandwidth. The LAG will only be operational if at least one member interface is active and configured correctly.
No Operational Member Interfaces:
If no member interfaces are added or if the member interfaces are down, the LAG will remain in a down state, as shown in the exhibit for ae0 and ae1.
Resolution:
Verify that physical interfaces have been added to the LAG using commands like:
LAG Interface Status: In Juniper, the link status of the LAG depends on its member interfaces, which must be operational for the LAG to function.
Question 16
Which three technologies improve high availability and convergence in a data center network? (Choose three.)
Correct Answer:ABE
High availability and fast convergence are critical in data center networks to minimize downtime and maintain optimal performance. The following technologies contribute to achieving these goals: Graceful Restart (GR):
Graceful Restart (GR): GR allows routers to maintain forwarding state during control plane restarts, ensuring continuous packet forwarding while minimizing network disruptions.
GR allows routers to maintain forwarding state during control plane restarts, ensuring continuous packet forwarding while minimizing network disruptions. Bidirectional Forwarding Detection (BFD):
Bidirectional Forwarding Detection (BFD): BFD provides fast detection of path failures, allowing routing protocols to converge quickly by detecting link failures much faster than traditional timers.
BFD provides fast detection of path failures, allowing routing protocols to converge quickly by detecting link failures much faster than traditional timers. Link Aggregation Group (LAG):
Link Aggregation Group (LAG): LAG increases both redundancy and bandwidth by combining multiple physical links into one logical link, providing load balancing and fault tolerance.
LAG increases both redundancy and bandwidth by combining multiple physical links into one logical link, providing load balancing and fault tolerance.
Juniper Reference: High Availability Techniques: These technologies are fundamental in ensuring rapid recovery and failover within Juniper-based data center environments.
High Availability Techniques: These technologies are fundamental in ensuring rapid recovery and failover within Juniper-based data center environments.
Question 17
Which signaling protocol is used for EVPN?
Correct Answer:D
EVPN (Ethernet Virtual Private Network)is a standard protocol used for building Layer 2 and Layer 3 VPNs over an IP or MPLS network. Thesignaling protocolused for EVPN isBGP(Border Gateway Protocol).
Step-by-Step Breakdown:
BGP as the EVPN Signaling Protocol:EVPN uses BGP to exchange MAC address reachability information between routers (PE devices). This enables devices to learn which MAC addresses are reachable through which PE devices, facilitating Layer 2 forwarding across an IP or MPLS core.
BGP Extensions for EVPN:BGP is extended with new address families (e.g., EVPN NLRI) to carry both MAC and IP address information, allowing for scalable and efficient multi-tenant network solutions.
Juniper Reference:
Junos EVPN Configuration: Juniper uses BGP as the control plane for EVPN to exchange MAC and IP route information between different data center devices.
Question 18
MACsec provides protection against which two types of threats? (Choose two.)
Correct Answer:BD
MACsec (Media Access Control Security)provides data confidentiality, integrity, and origin authenticity at
Layer 2, protecting against several types of threats.
Step-by-Step Breakdown:
Man-in-the-Middle Attack Protection:MACsec encrypts traffic at Layer 2, preventingman-in-themiddle
attackswhere an attacker intercepts and manipulates traffic between two communicating
devices. Since the data is encrypted, any intercepted packets are unreadable.
Protection Against Playback Attacks:MACsec also protects againstplayback attacksby using
sequence numbers and timestamps to ensure that old, replayed packets are not accepted by the receiver.
Juniper Reference:
MACsec Configuration: Juniper devices support MACsec for securing Layer 2 communications,
ensuring protection against replay and man-in-the-middle attacks in sensitive environments.