Online JN0-280 Practice TestMore Juniper Products >
Free Juniper JN0-280 Exam Dumps Questions
Juniper JN0-280: Data Center Associate (JNCIA-DC)
- Get instant access to JN0-280 practice exam questions
- Get ready to pass the Data Center Associate (JNCIA-DC) exam right now using our Juniper JN0-280 exam package, which includes Juniper JN0-280 practice test plus an Juniper JN0-280 Exam Simulator.
- The best online JN0-280 exam study material and preparation tool is here.
Question 1
Which two statements about IBGP are correct? (Choose two.)
Correct Answer:CD
:
IBGP (Internal Border Gateway Protocol)is used to exchange routing information betweenrouters within the same AS (Autonomous System).
Step-by-Step Breakdown:
TTL of 255:
By default, IBGP sessions are established with aTTL (Time to Live)value of255. This allows IBGP neighbors to communicate over multiple hops within the AS without requiring any additional configuration.
Full Mesh Requirement:
IBGP requires alogical full meshbetween all IBGP routers to ensure that routing information is fully distributed within the AS. Since IBGP does not propagate routes learned from one IBGP peer to another by default, a full mesh topology is needed unlessroute reflectorsorBGP confederationsare used.
Juniper Reference:
IBGP Full Mesh: Juniper recommends using route reflectors in large networks to simplify IBGP full-mesh requirements.
Question 2
Which statement is correct about member interfaces when creating a LAG?
Correct Answer:B
When creating aLAG (Link Aggregation Group)in Junos, theduplex settingsandlink speedmust be the same across all member interfaces.
Step-by-Step Breakdown:
LAG Overview:A LAG combines multiple physical interfaces into a single logical interface to increase bandwidth and provide redundancy. All member links must act as a single cohesive unit.
Interface Requirements:
Duplex: All member interfaces must operate in the same duplex mode (either full-duplex or half-duplex). Mismatched duplex settings can cause performance issues, packet drops, or interface errors.
Link Speed: All interfaces in the LAG must have the same link speed (e.g., all interfaces must be 1 Gbps or 10 Gbps). Mismatched speeds would prevent the interfaces from functioning correctly within the LAG.
Configuration and Validation: Ensure that all member interfaces have identical settings before adding them to the LAG. These settings can be checked using the show interfaces command, and the LAG can be configured using:
set interfaces ae0 aggregated-ether-options link-speed 10g
set interfaces ge-0/0/1 ether-options 802.3ad ae0
Juniper Reference:
LAG Configuration: Duplex and link speed must be consistent across member interfaces to ensure proper LAG operation in Juniper devices.
Question 3
Exhibit: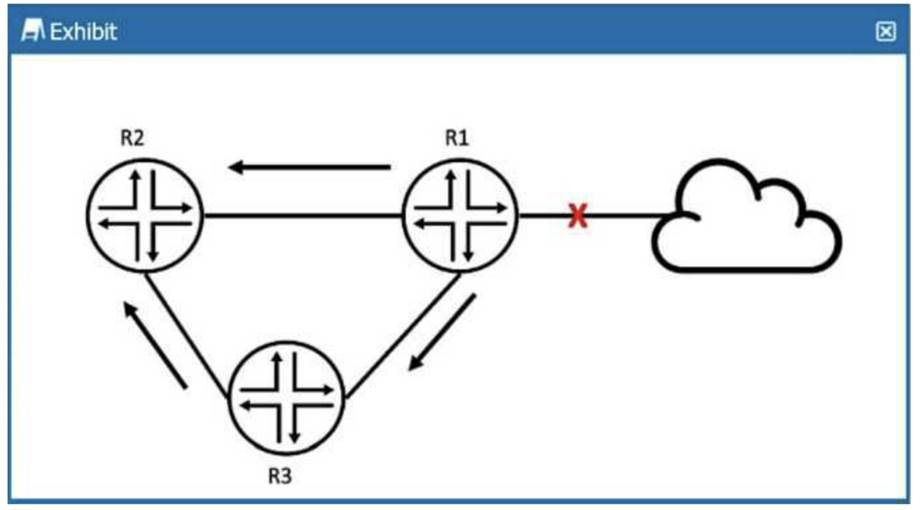
R2 received an OSPF update from R1, and it received the same update from R3.
Referring to the exhibit, what will R2 do?
Correct Answer:C
In the exhibit, R2 receives the same OSPF update from both R1 and R3. OSPF has mechanisms toprevent
unnecessary processing of duplicate LSAs (Link-State Advertisements).
Step-by-Step Breakdown:
OSPF LSA Processing:
OSPF uses LSAs to exchange link-state information between routers. When a router receives an
LSA, it checks if it already has a copy of the LSA in its Link-State Database (LSDB).
Duplicate LSAs:If R2 has already received and processed the update from R1, it willignore the update
from R3because it already has the same LSA in its database. OSPF uses the concept of flooding, but it
does not reprocess LSAs that it already knows about.
R2 Behavior:R2 will keep the update from R1 (the first one it received) and will ignore the same LSA
from R3, as it is already in the LSDB.
Juniper Reference:
OSPF LSA Processing: Junos adheres to OSPF standards, ensuring that duplicate LSAs are not
processed multiple times to avoid unnecessary recalculations.
Question 4
Which two statements are true about how switches handle Layer 2 traffic? (Choose two.)
Correct Answer:BD
In Layer 2 switching, switches learn MAC addresses based on thesource MAC addressof incoming frames and forward frames based on thedestination MAC address.
Step-by-Step Breakdown: MAC Learning:When a switch receives a frame, it records thesource MAC addressand the port on which it arrived. This allows the switch to know where to send traffic destined for that MAC address.
MAC Learning:When a switch receives a frame, it records thesource MAC addressand the port on which it arrived. This allows the switch to know where to send traffic destined for that MAC address. Forwarding Based on Destination:The switch then looks at thedestination MAC addressand forwards the frame out of the port associated with that MAC address. If the MAC is unknown, the switch floods the frame to all ports.
Forwarding Based on Destination:The switch then looks at thedestination MAC addressand forwards the frame out of the port associated with that MAC address. If the MAC is unknown, the switch floods the frame to all ports.
Juniper Reference: Layer 2 Switching: Juniper switches use source MAC addresses to build MAC tables and forward traffic based on the destination MAC address.
Layer 2 Switching: Juniper switches use source MAC addresses to build MAC tables and forward traffic based on the destination MAC address.
Question 5
Which two statements are correct about EVPN-VXLAN overlay networking? (Choose two.)
Correct Answer:BC
EVPN-VXLANis an overlay technology used in data center networks to extend Layer 2 services over a Layer 3 network.
Step-by-Step Breakdown:
BGP Control Plane:BGP (Border Gateway Protocol)is used as the control plane for EVPN-VXLAN. BGP advertises MAC addresses and IP address reachability information across the VXLAN network, enabling efficient multi-tenant Layer 2 connectivity over a Layer 3 infrastructure.
Encapsulation:VXLAN (Virtual Extensible LAN)encapsulates Layer 2 frames into Layer 3 packets. This encapsulation allows Layer 2 traffic to be transported across a Layer 3 network, effectively creating a tunnel for Ethernet frames.
Juniper Reference:
EVPN-VXLAN Configuration: Juniper supports EVPN-VXLAN with BGP as the control plane, allowing scalable Layer 2 connectivity over a routed infrastructure in modern data centers.
Question 6
How many stages are shown in the exhibit?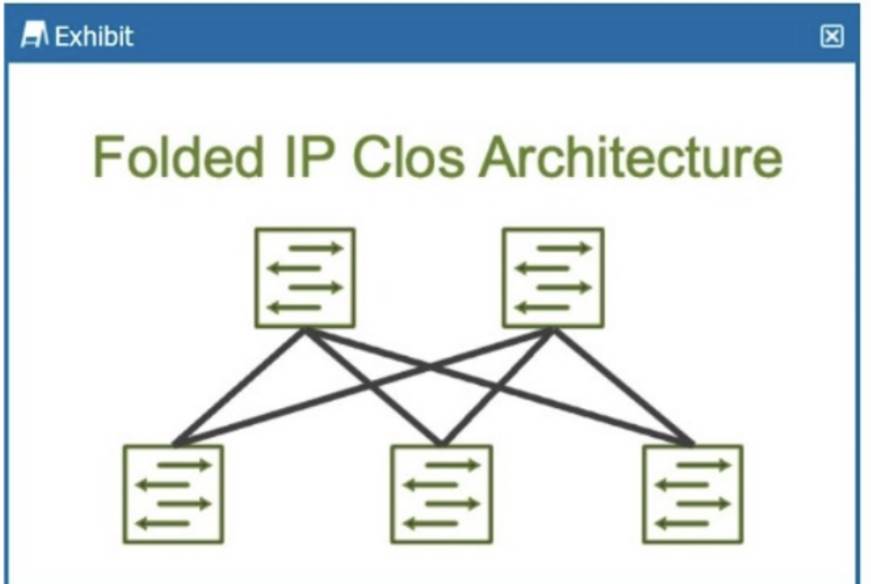
Correct Answer:D
The exhibit shows aFolded IP Clos Architecture, which is also referred to as a3-stage Closnetwork design. This architecture typically consists of two layers of switches:
Spine Layer: The top row of switches.
Leaf Layer: The bottom row of switches.
Step-by-Step Breakdown:
Clos Architecture:A 3-stage Clos network has two types of devices: spine and leaf. In this design, each leaf switch connects to every spine switch, providing a high level of redundancy and load balancing.
Stage Explanation:
Stage 1: The first set of leaf switches.
Stage 2: The spine switches.
Stage 3: The second set of leaf switches.
TheFolded Closarchitecture shown here effectively "folds" the 3-stage design by combining the ingress and egress leaf layers into one, reducing it to two visible layers, but still maintaining the overall3-stage architecture.
Juniper Reference:
IP Clos Architecture: The 3-stage Clos design is commonly used in modern data centers for high availability, redundancy, and scalability.