Online JN0-1332 Practice TestMore Juniper Products >
Free Juniper JN0-1332 Exam Dumps Questions
Juniper JN0-1332: Security Design. Specialist (JNCDS-SEC)
- Get instant access to JN0-1332 practice exam questions
- Get ready to pass the Security Design. Specialist (JNCDS-SEC) exam right now using our Juniper JN0-1332 exam package, which includes Juniper JN0-1332 practice test plus an Juniper JN0-1332 Exam Simulator.
- The best online JN0-1332 exam study material and preparation tool is here.
Question 1
What are two factors you must consider when designing a network for security intelligence? (Choose two.)
Correct Answer:B
Question 2
You are asked to design an automated vulnerability scanner that can actively check to see which ports are open and report on the findings. Which Junker Networks product would you use in this scenario7
Correct Answer:C
Question 3
Multiple customers use the shared infrastructure of your data center. These customers require isolation for compliance and security reasons.
What would you do to satisfy this requirement?
Correct Answer:C
Question 4
Refer to the Exhibit.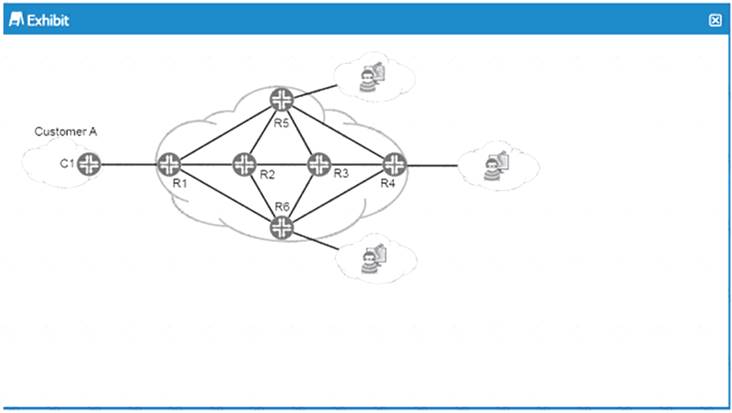
You are asked to provide a proposal for security elements in the service provider network shown in the exhibit. You must provide DOoS protection for Customer A from potential upstream attackers.
Which statements correct in this scenario?
Correct Answer:C
Question 5
You must implement a security solution that uses a central database to authenticate devices without EAP-M05 based on their network interface address. Which solution will accomplish this task'?
Correct Answer:C
Question 6
Which two statements describe Juniper ATP Cloud? (Choose two)
Correct Answer:AD