Question 7
You are configuring a firewall filter on a Juniper device.
In this scenario, what are two valid terminating actions? (Choose two.)
Correct Answer:BD
In Juniper firewall filter configurations, "discard" and "accept" are two valid terminating actions for a term within a filter. The "discard" action drops the packet, preventing it from reaching its intended destination, while the "accept" action allows the packet to pass through the filter, proceeding to its next hop or destination. "Count" is a non- terminating action that increments a counter every time a packet matches the term but does not inherently determine the packet's fate. "Next term" directs the evaluation to proceed to the next term in the filter for further processing, also a non-terminating action.
Question 8
Which layer of the OSI model contains the IP address information?
Correct Answer:B
The OSI (Open Systems Interconnection) model is a conceptual framework used to understand network interactions in seven distinct layers. IP (Internet Protocol) addresses are part of Layer 3, known as the Network Layer. This layer is responsible for packet forwarding, including routing through intermediate routers, and it handles the logical addressing scheme of the network to ensure that packets can be routed across multiple networks and reach their destination. IP addresses provide unique identifiers for network interfaces, allowing for communication between devices on a network or across different networks.
Question 9
Which component is considered part of the data plane?
Correct Answer:B
The Packet Forwarding Engine (PFE) is an integral component of Juniper Networks devices, responsible for the data plane operations. The data plane, also known as the forwarding plane, is where the actual processing and forwarding of packets occur
based on the routing and forwarding tables. The PFE executes the forwarding decisions made by the Routing Engine (RE), handling all packet transmissions, including routing, filtering, and switching packets towards their destination. This contrasts with the control plane operations handled by the RE, which involve routing table maintenance, system management, and control protocol processing.
Question 10
Click the Exhibit button.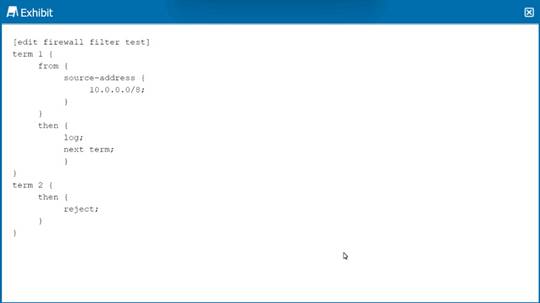
How is traffic, sourced from 10.0.0.0/8, treated by the firewall filter shown in the exhibit?
Correct Answer:D
The firewall filter configuration in the exhibit specifies a filter with two terms. Term 1 matches traffic from the source address 10.0.0.0/8 and has two actions: 'log' and 'next term'. The 'log' action will record the match to a log file, and 'next term' indicates that the firewall should evaluate the next term after logging. There is no explicit action such as 'accept' or 'reject' in term 1, so by default, the traffic will be accepted unless subsequently rejected by another term.
Term 2 has the action 'reject', which discards packets that reach this term. Since there is no 'from' condition in term 2, it acts as a default rule for all traffic not matched by term 1. Because the traffic sourced from 10.0.0.0/8 matches term 1 and there is no reject action in that term, it will be logged and then accepted by the firewall filter. There is no subsequent term that rejects this specific traffic, so the action from term 2 does not apply to it.
Question 11
Which two components are included in a transport header? (Choose two.)
Correct Answer:AC
The transport layer in the OSI model is responsible for end-to-end communication and error recovery. In a transport header, such as TCP or UDP, the key components include the source port number and the destination port number. These port numbers are used to identify sending and receiving applications. The source port number indicates the port of the sending application, and the destination port number refers to the port of the receiving application. MAC addresses, on the other hand, are part of the data link layer (Layer 2) and would be included in an Ethernet header, not a transport header.
Question 12
Exhibit
user@router> show route 192.168.100.2
inet.O: 15 destinations, 17 routes (15 active, 0 holddown, 0 hidden) Limit/Threshold: 1048576/1048576 destinations
+ = Active Route, - = Last Active, * = Both 192.168.100.2/32*[OSPF/IO] 00:14:29, metric 1
> to 172.16.1.6 via ge-0/0/1.0 [BGP/170] 00:06:49, localpref 100
AS path: 65102 I, validation-state: unverified > to 172.16.1.6 via ge-0/0/1.0
Referring to the exhibit, which statement is correct?
Correct Answer:C
Referring to the exhibit, the presence of the "+" symbol next to the OSPF route for 192.168.100.2/32 indicates that this is the active route being used to forward traffic. The BGP route, although present, does not have the "+" symbol, indicating it is not the active route. In Junos OS, the routing table displays the active route with a "+" symbol, and the fact that the OSPF route has this symbol means it is the preferred path based on the routing protocol's decision process, which takes into account factors such as route preference (administrative distance) and metrics.