Question 43
Northern Trail Outfitters mar ages functional group permissions in a custom security application supported by a relational database and a REST service layer. Group permissions are mapped as permission sets in Salesforce.
Which action should an identity architect use to ensure functional group permissions are reflected as permission set assignments?
Correct Answer:B
Using a Login Flow with invocable Apex to callout to the security application and set permission sets allows the identity architect to dynamically assign or remove permission sets based on the functional group permissions in the custom security application. This ensures that the permission set assignments are consistent with the group permissions. References: Login Flows, Invocable Apex
Question 44
Universal Containers (UC) has a classified information system that its call center team uses only when they are working on a case with a record type "Classified". They are only allowed to access the system when they own an open "Classified" case, and their access to the system is removed at all other times. They would like to implement SAML SSO with Salesforce as the Idp, and automatically allow or deny the staff's access to the classified information system based on whether they currently own an open "Classified" case record when they try to access the system using SSO. What is the recommended solution for automatically allowing or denying access to the classified information system based on the open "classified" case record criteria?
Correct Answer:C
Custom SAML JIT Provisioning allows Salesforce to dynamically create or update user records in the classified information system based on the SAML assertion sent by Salesforce as the IdP. This way, the staff can access the system only when they have an open “Classified” case, and their access is revoked when they don’t. Option A is incorrect because Salesforce reports are not a reliable way to grant or revoke access to the system, as they are not updated in real time and may not reflect the current status of the cases. Option B is incorrect because Apex triggers can only assign or remove permission sets within Salesforce, not in an external system. Option D is incorrect because a Common Connected App Handler using Apex is used to customize the behavior of a connected app, not to control access to an external system based on user attributes. References: Custom SAML JIT Provisioning, Create a Custom Connected App Handler
Question 45
Refer to the exhibit.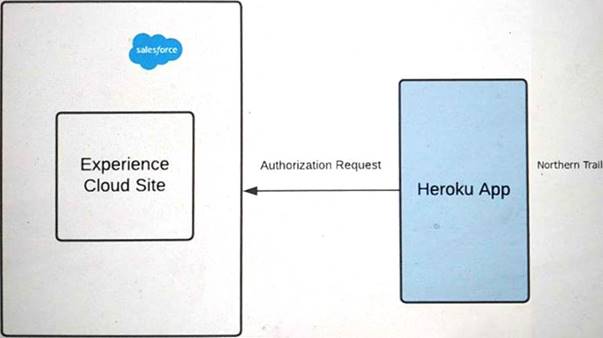
Outfitters (NTO) is using Experience Cloud as an Identity for its application on Heroku. The application on Heroku should be able to handle two brands, Northern Trail Shoes and Northern Trail Shirts.
A user should select either of the two brands in Heroku before logging into the community. The app then performs Authorization using OAuth2.0 with the Salesforce Experience Cloud site.
NTO wants to make sure it renders login page images dynamically based on the user's brand preference selected in Heroku before Authorization.
what should an identity architect do to fulfill the above requirements?
Correct Answer:D
OAuth 2.0 is an open standard for authorization that allows a third-party application to obtain limited access to a protected resource on behalf of a user. To authorize a third-party service using OAuth 2.0 with the Salesforce Experience Cloud site, the identity architect should do the following steps: Create a connected app for the third-party service in Salesforce. A connected app is an application that integrates with Salesforce using APIs and standard protocols, such as SAML, OAuth, and OpenID Connect. To create a connected app, you need to provide the basic information, such as the app name, logo URL, contact email, and API name. You also need to enable OAuth and configure the OAuth settings, such as the callback URL, the scopes, and the policies.
Create a connected app for the third-party service in Salesforce. A connected app is an application that integrates with Salesforce using APIs and standard protocols, such as SAML, OAuth, and OpenID Connect. To create a connected app, you need to provide the basic information, such as the app name, logo URL, contact email, and API name. You also need to enable OAuth and configure the OAuth settings, such as the callback URL, the scopes, and the policies. Authorize the third-party service by sending authorization requests to the
Authorize the third-party service by sending authorization requests to the
community-url/services/oauth2/authorize/expid_value. This is a special endpoint that allows you to specify an experience ID (expid) as a query parameter in the authorization request. The experience ID is a unique identifier for each experience (community or site) in Salesforce. By using this endpoint, you can dynamically render the login page images based on the user’s brand preference selected in the
third-party service before authorization.
References: OAuth 2.0
OAuth 2.0 OAuth 2.0 Web Server Authentication Flow
OAuth 2.0 Web Server Authentication Flow  Connected Apps
Connected Apps Create a Connected App
Create a Connected App  Experience ID
Experience ID Authorize Apps with OAuth
Authorize Apps with OAuth
Question 46
Northern Trail Outfitters manages application functional permissions centrally as Active Directory groups. The CRM_Superllser and CRM_Reportmg_SuperUser groups should respectively give the user the SuperUser and Reportmg_SuperUser permission set in Salesforce. Salesforce is the service provider to a Security Assertion Markup Language (SAML) identity provider.
Mow should an identity architect ensure the Active Directory groups are reflected correctly when a user accesses Salesforce?
Correct Answer:B
Using the Apex Just-in-Time handler to query custom SAML attributes and set permission sets is the best way to ensure that the Active Directory groups are reflected correctly when a user accesses Salesforce. The Apex Just-in-Time handler is a custom class that can process the SAML response from the identity provider and assign permission sets based on the user’s AD groups. The other options are either not feasible or not effective for this use case. References: Just-in-Time Provisioning for SAML, Apex Just-in-Time Handler
Question 47
Universal containers (UC) is setting up Delegated Authentication to allow employees to log in using their corporate credentials. UC's security team is concerned about the risk of exposing the corporate login service on the Internet and has asked that a reliable trust mechanism be put in place between the login service and salesforce. What mechanism should an architect put in place to enable a trusted connection between the login services and salesforce?
Correct Answer:D
To enable a trusted connection between the login services and Salesforce, UC should enforce mutual authentication between systems using SSL. Mutual authentication is a process in which both parties in a communication verify each other’s identity using certificates7. SSL (Secure Sockets Layer) is a protocol that provides secure communication over the Internet using encryption and certificates8. By using mutual authentication with SSL, UC can ensure that only authorized login services can access Salesforce and vice versa. This can prevent unauthorized access, impersonation, or phishing attacks.
References: Mutual Authentication, SSL (Secure Sockets Layer)
Question 48
Universal Containers (UC) has implemented SSO according to the diagram below. uses SAML while Salesforce Org 1 uses OAuth 2.0. Users usually start their day by first attempting to log into Salesforce Org 2 and then later in the day, they will log into either the Financial System or CPQ system depending upon their job position. Which two systems are acting as Identity Providers?
Correct Answer:BD
These are the systems that are acting as identity providers (IdPs) in the SSO scenario. An IdP is a trusted provider that enables a customer to use single sign-on (SSO) to access other websites5. In this case, Pingfederate and Salesforce Org 1 are the IdPs that authenticate the users and issue SAML assertions or
OAuth tokens to the service providers (SPs). The SPs are the websites that host apps and rely on the IdPs for authentication5. In this case, Salesforce Org 2, Financial System, and CPQ System are the SPs that receive the SAML assertions or OAuth tokens from the IdPs and grant access to the users.
Option A is incorrect because Financial System is not an IdP, but an SP. It does not authenticate the users, but receives SAML assertions from Pingfederate. Option C is incorrect because Salesforce Org 2 is not an IdP, but an SP. It does not authenticate the users, but receives OAuth tokens from Salesforce Org 1.
References: 5: Identity Providers and Service Providers - Salesforce 6: Salesforce as Service Provider an Identity Provider for SSO