Online HPE6-A85 Practice TestMore HP Products >
Free HP HPE6-A85 Exam Dumps Questions
HP HPE6-A85: Aruba Certified Campus Access Associate Exam
- Get instant access to HPE6-A85 practice exam questions
- Get ready to pass the Aruba Certified Campus Access Associate Exam exam right now using our HP HPE6-A85 exam package, which includes HP HPE6-A85 practice test plus an HP HPE6-A85 Exam Simulator.
- The best online HPE6-A85 exam study material and preparation tool is here.
Question 1
DRAG DROP
Match the feature to the Aruba OS version (Matches may be used more than once.)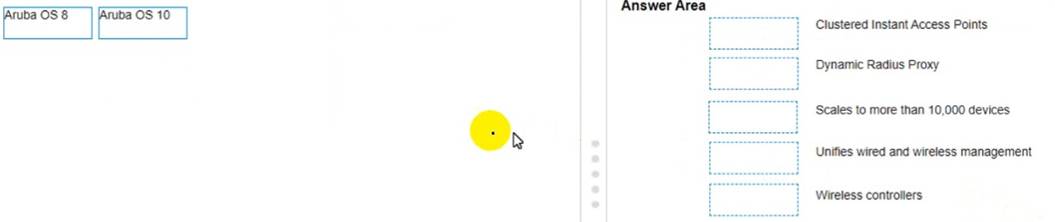
Solution:
Features: 1) Clustered Instant Access Points Aruba OS version: a) Aruba OS 8
Features: 2) Dynamic Radius Proxy Aruba OS version: a) Aruba OS 8
Features: 3) Scales to more than 10,000 devices Aruba OS version: b) Aruba OS 10 Features: 4) Unifies wired and wireless management Aruba OS version: a) Aruba OS 8 Features: 5) Wireless controllers Aruba OS version: a) Aruba OS 8
ArubaOS is the operating system for all Aruba Mobility Controllers (MCs) and controller- managed wireless access points (APs). ArubaOS 8 delivers unified wired and wireless access, seamless roaming, enterprise grade security, and a highly available network with the required reliability to support high density environments1. Some of the features of
ArubaOS 8 are:
✑ Clustered Instant Access Points: This feature allows multiple Instant APs to form a cluster and share configuration and state information. This enables seamless roaming, load balancing, and fast failover for clients2.
✑ Dynamic Radius Proxy: This feature allows an MC to act as a proxy for RADIUS authentication requests from clients or APs. This simplifies the configuration and management of RADIUS servers and reduces the network traffic between MCs and RADIUS servers3.
✑ Wireless controllers: Aruba wireless controllers are devices that centrally manage and control the wireless network. They provide functions such as AP provisioning, configuration, security, policy enforcement, and network optimization.
ArubaOS 10 is the next-generation operating system that works with Aruba Central, a cloud-based network management platform. ArubaOS 10 delivers greater scalability, security, and AI-powered optimization across large campuses, branches, and remote work environments. Some of the features of ArubaOS 10 are:
✑ Scales to more than 10,000 devices: ArubaOS 10 can support up to 10,000
devices per cluster, which is ten times more than ArubaOS 8. This enables customers to scale their networks without compromising performance or reliability.
✑ Unifies wired and wireless management: ArubaOS 10 provides a single platform
for managing both wired and wireless devices across the network. Customers can use Aruba Central to configure, monitor, troubleshoot, and update their devices from anywhere.
Both ArubaOS 8 and ArubaOS 10 share some common features, such as:
✑ Unifies wired and wireless management: Both operating systems provide unified wired and wireless access for customers who use Aruba switches and
APs. Customers can use a single interface to manage their entire network infrastructure1 . References: 1 https://www.arubanetworks.com/resource/arubaos- 8-fundamental-
guide/ 2 https://www.arubanetworks.com/techdocs/Instant_86_WebHelp/Content/i nstant-ug/iap-
maintenance/cluster.htm 3 https://www.arubanetworks.com/techdocs/ArubaOS_86
_Web_Help/Content/arubaos-solutions/1-overview/dynamic-radius-proxy.htm https://www.arubanetworks.com/products/networking/controllers/ https://www.arubanetworks.com/products/network-management- operations/arubaos/ https://blogs.arubanetworks.com/solutions/making-the-switch/ https://www.arubanetworks.com/products/network-management-operations/aruba- central/
Does this meet the goal?
Correct Answer:A
Question 2
Where are wireless client roaming decisions made?
Correct Answer:A
Wireless client roaming decisions are made by the client device based on its own criteria, such as signal strength, noise level, data rate, etc. The network can influence the client??s roaming decision by providing information such as neighbor reports, load
balancing, band steering, etc., but the final decision is up to the client. References:https://www.arubanetworks.com/techdocs/Instant_86_WebHelp/Content/instan t-ug/wlan-roaming/client-roaming.htm
Question 3
DRAG DROP
What is the correct order of the TCP 3-Way Handshake sequence?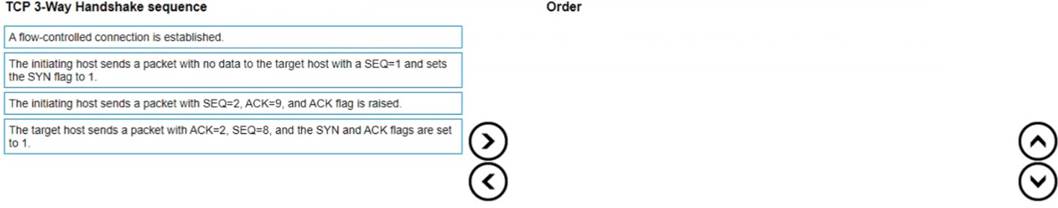
Solution:
TCP 3-Way Handshake sequence is:
✑ Step 1: The initiating host sends a packet with no data to the target host with a SEQ=1 and sets the SYN flag to 1.
✑ Step 2: The target host responds with a packet with ACK=2, SEQ=8, and the SYN and ACK flags set to 1.
✑ Step 3: The initiating host sends a packet with SEQ=2, ACK=9, and the ACK flag set to 1.
✑ Step 4: A normal-controlled connection is established. References: https://en.wikipedia.org/wiki/Transmission_Control_Protocol
https://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13788- 3.html
Does this meet the goal?
Correct Answer:A
Question 4
Which Aruba technology will allow for device-specific passphrases to securely add headless devices to the WLAN?
Correct Answer:B
Multiple Pre-Shared Key (MPSK) is a feature that allows device-specific or group-specific passphrases to securely add headless devices to the WLAN Wireless Local Area Network. WLAN is a wireless computer network that links two or more devices using wireless communication to form a local area network (LAN) within a limited area such as a home, school, computer laboratory, campus, or office building. . MPSK enhances the WPA2 PSK Wi-Fi Protected Access 2 Pre-Shared Key. WPA2 PSK is a method of securing your network using WPA2 with the use of the optional Pre-Shared Key (PSK) authentication, which was designed for home users without an enterprise authentication server. mode by allowing different PSKs for different devices on the same SSID Service Set Identifier. SSID is a case-sensitive, 32 alphanumeric character unique identifier attached to the header of packets sent over a wireless local-area network (WLAN). The SSID acts as a password when a mobile device tries to connect to the basic service set (BSS) — a component of the IEEE 802.11 WLAN architecture. . MPSK passwords can be generated or user-created and are managed by ClearPass Policy Manager12. References:
1 https://blogs.arubanetworks.com/solutions/simplify-iot-authentication-with-multiple-pre-
shared-keys/ 2
https://www.arubanetworks.com/techdocs/ClearPass/6.8/Guest/Content/AdministrationTasks1/Configuring-MPSK.htm
Question 5
Which authentication does Aruba's Captive Portal use?
Correct Answer:A
Aruba??s Captive Portal uses Layer 3 authentication, which means that it intercepts the client??s HTTP requests and redirects them to a web page where the client can enter their credentials. The credentials are then verified by a RADIUS server or a local database before granting network access. References:https://www.arubanetworks.com/techdocs/Instant_86_WebHelp/Content/instan
t-ug/captive-portal/captive-portal-auth.htm
Question 6
Review the configuration below.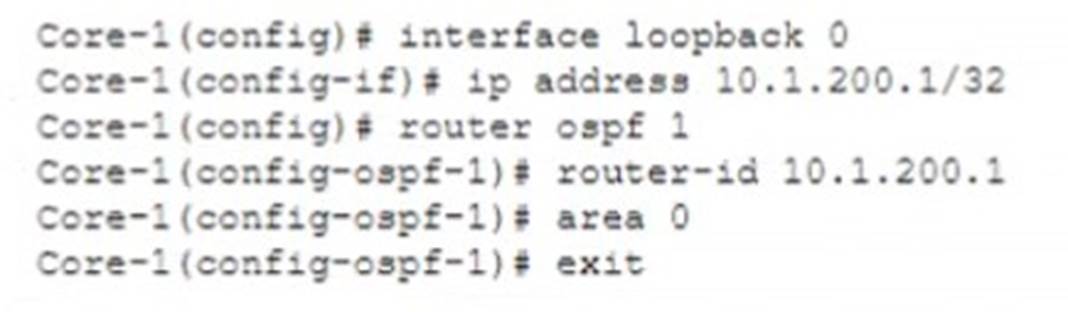
Why would you configure OSPF to use the IP address 10.1.200.1 as the router ID?
Correct Answer:D
The reason why you would configure OSPF Open Shortest Path First (OSPF) is a link-state routing protocol that dynamically calculates the best routes for data transmission within an IP network. OSPF uses a hierarchical structure that divides a network into areas and assigns each router an identifier called router ID (RID). OSPF uses hello packets to discover neighbors and exchange routing information. OSPF uses Dijkstra??s algorithm to compute the shortest path tree (SPT) based on link costs and build a routing table based on SPT. OSPF supports multiple equal-cost paths, load balancing, authentication, and various network types such as broadcast, point-to-point, point-to- multipoint, non-broadcast multi-access (NBMA), etc. OSPF is defined in RFC 2328 for IPv4 and RFC 5340 for IPv6. to use the IP address IP address Internet Protocol (IP) address is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: host or network interface identification and location addressing. There are two versions of IP addresses: IPv4 and IPv6. IPv4 addresses are 32 bits long and written in dotted-decimal notation, such as 192.168.1.1. IPv6 addresses are 128 bits long and written in hexadecimal notation, such as 2001:db8::1. IP addresses can be either static (fixed) or dynamic (assigned by a DHCP server). 10.1.200.1 as the router ID Router ID (RID) Router ID (RID) is a unique identifier assigned to each router in a routing domain or protocol. RIDs are used by routing protocols such as OSPF, IS-IS, EIGRP, BGP, etc., to identify neighbors, exchange routing information, elect designated routers (DRs), etc. RIDs are usually derived from one of the IP addresses configured on the router??s interfaces or loopbacks, or manually specified by network administrators. RIDs must be unique within a routing domain or protocol instance. is that the loopback interface state Loopback interface Loopback interface is a virtual interface on a router that does not correspond to any physical port or connection. Loopback interfaces are used for various purposes such as testing network connectivity, providing stable router IDs for routing protocols, providing management access to routers, etc. Loopback interfaces have some advantages over physical interfaces such as being always up unless administratively shut down, being independent of any hardware failures or link failures, being able to assign any IP address regardless of subnetting constraints, etc. Loopback interfaces are usually numbered from zero (e.g., loopback0) upwards on routers. Loopback interfaces can also be created on PCs or servers for testing or configuration purposes using special IP addresses reserved for loopback testing (e.g., 127.x.x.x for IPv4 or ::1 for IPv6). Loopback interfaces are also
known as virtual interfaces or dummy interfaces . Loopback interface state Loopback interface state refers to whether a loopback interface is up or down on a router . A loopback interface state can be either administratively controlled (by using commands such as no shutdown or shutdown ) or automatically determined by routing protocols (by using commands such as passive-interface or ip ospf network point-to-point ). A loopback interface state affects how routing protocols use the IP address assigned to the loopback interface for neighbor discovery , router ID selection , route advertisement , etc . A loopback interface state can also affect how other devices can access or ping the loopback interface . A loopback interface state can be checked by using commands such as show ip interfacebrief or show ip ospf neighbor . is independent of any physical interface and reduces routing updates.
The loopback interface state is independent of any physical interface because it does not depend on any hardware or link status. This means that the loopback interface state will always be up unless it is manually shut down by an administrator. This also means that the loopback interface state will not change due to any physical failures or link failures that may affect other interfaces on the router.
The loopback interface state reduces routing updates because it provides a stable router ID for OSPF that does not change due to any physical failures or link failures that may affect other interfaces on the router. This means that OSPF will not have to re-elect DRs Designated Routers (DRs) Designated Routers (DRs) are routers that are elected by OSPF routers in a broadcast or non-broadcast multi-access (NBMA) network to act as leaders and coordinators of OSPF operations in that network. DRs are responsible for generating link-state advertisements (LSAs) for the entire network segment, maintaining adjacencies with all other routers in the segment, and exchanging routing information with other DRs in different segments through backup designated routers (BDRs). DRs are elected based on their router priority values and router IDs . The highest priority router becomes the DR and the second highest priority router becomes the BDR . If there is a tie in priority values , then the highest router ID wins . DRs can be manually configured by setting the router priority value to 0 (which means ineligible) or 255 (which means always eligible) on specific interfaces . DRs can also be influenced by using commands such as ip ospf priority , ip ospf dr-delay , ip ospf network point-to-multipoint , etc . DRs can be verified by using commands such as show ip ospf neighbor , show ip ospf interface , show ip ospf database
, etc . , recalculate SPT Shortest Path Tree (SPT) Shortest Path Tree (SPT) is a data structure that represents the shortest paths from a source node to all other nodes in a graph or network . SPT is used by link-state routing protocols such as OSPF and IS-IS to compute optimal routes based on link costs . SPT is built using Dijkstra??s algorithm , which starts from the source node and iteratively adds nodes with the lowest cost paths to the tree until all nodes are included . SPT can be represented by a set of pointers from each node to its parent node in the tree , or by a set of next-hop addresses from each node to its destination node in the network . SPT can be updated by adding or removing nodes or links
, or by changing link costs . SPT can be verified by using commands such as show ip route
, show ip ospf database , show clns route , show clns database , etc . , or send LSAs Link- State Advertisements (LSAs) Link-State Advertisements (LSAs) are packets that contain information about the state and cost of links in a network segment . LSAs are generated and flooded by link-state routing protocols such as OSPF and IS-IS to exchange routing information with other routers in the same area or level . LSAs are used to build link-state databases (LSDBs) on each router , which store the complete topology of the network segment . LSAs are also used to compute shortest path trees (SPTs) on each router , which determine the optimal routes to all destinations in the network . LSAs have different types depending on their origin and scope , such as router LSAs , network LSAs , summary LSAs , external LSAs , etc . LSAs have different formats depending ontheir type and protocol version , but they usually contain fields such as LSA header , LSA type , LSA length , LSA age , LSA sequence number , LSA checksum , LSA body , etc . LSAs can be verified by using commands such as show ip ospf database , show clns database , debug ip ospf hello , debug clns hello , etc . due to changes in router IDs.
The other options are not reasons because:
✑ The IP address associated with the loopback interface is non-routable and prevents loops: This option is false because the IP address associated with the loopback interface is routable and does not prevent loops. The IP address associated with the loopback interface can be any valid IP address that belongs to an existing subnet or a new subnet created specifically for loopbacks. The IP address associated with the loopback interface does not prevent loops because loops are caused by misconfigurations or failures in routing protocols or devices, not by IP addresses.
✑ The loopback interface state is dependent on the management interface state and reduces routing updates: This option is false because
the loopback interface state is independent of any physical interface state, including the management interface state Management interface Management interface is an interface on a device that provides access to management functions such as configuration, monitoring, troubleshooting, etc . Management interfaces can be physical ports such as console ports, Ethernet ports, USB ports, etc., or virtual ports such as Telnet sessions, SSH sessions, web sessions, etc . Management interfaces can use different protocols such as CLI Command-Line Interface (CLI) Command-Line Interface (CLI) is an interactive text- based user interface that allows users to communicate with devices using commands typed on a keyboard . CLI is one of the methods for accessing management functions on devices such as routers, switches, firewalls, servers, etc . CLI can use different protocols such as console port serial communication protocol Serial communication protocol Serial communication protocol is a method of transmitting data between devices using serial ports and cables . Serial communication protocol uses binary signals that represent bits (0s and 1s) and sends them one after another over a single wire . Serial communication protocol has advantages such as simplicity, low cost, long