Question 37
- (Topic 1)
You work as a Network Administrator for XYZ CORP. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory- based single forest network. You configure a new Windows Server 2008 server in the network. The new server is not yet linked to Active Directory. You are required to accomplish the following tasks: Add a new group named "Sales". Copy the "Returns" group from the older server to the new one. Rename the "Returns" group to "Revenue". View all group members, including for multiple groups/entire domain. You use Hyena to simplify and centralize all of these tasks. Which of the assigned tasks will you be able to accomplish?
Correct Answer:ABC
Hyena supports the following group management functions: Full group administration such as add, modify, delete, and copy Rename groups Copy groups from one computer to another View both direct and indirect (nested) group members for one or more groups [only for Active Directory] View all group members, including for multiple groups/entire domain [only for Active Directory] Answer D is incorrect. All group members can neither be viewed nor managed until the new server is linked to Active Directory.
Question 38
- (Topic 4)
You work as an Exchange Administrator for XYZ CORP. The network design of the company is given below: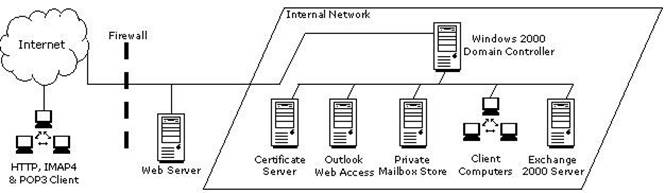
Employees are required to use Microsoft Outlook Web Access to access their emails remotely. You are required to accomplish the following goals: Ensure fault tolerance amongst the servers. Ensure the highest level of security and encryption for the Outlook Web Access clients. What will you do to accomplish these goals?
Correct Answer:C
To ensure fault tolerance among the servers and to get the highest possible level of security and encryption for OWA clients, you must install two front-end Exchange 2000 servers. Place the new servers on the perimeter network and configure load balancing between them. To enhance security, you should also configure Certificate Services and create a rule on the firewall to redirect port 443 to the servers. The most secure firewall configuration is placing a firewall on either side of the front-end servers. This isolates the front-end servers in a perimeter network, commonly referred to as a demilitarized zone (DMZ). It is always better to configure more than one front-end server to get fault tolerance.
Question 39
- (Topic 4)
You work as a Network Administrator for Infosec Inc. Nowadays, you are facing an unauthorized access in your Wi-Fi network. Therefore, you analyze a log that has been
recorded by your favorite sniffer, Ethereal. You are able to discover the cause of the unauthorized access after noticing the following string in the log file: (Wlan.fc.type_subtype eq 32 and llc.oui eq 0x00601d and llc.pid eq 0x0001) When you find All your 802.11b are belong to us as the payload string, you are convinced about which tool is being used for the unauthorized access. Which of the following tools have you ascertained?
Correct Answer:D
NetStumbler, a war driving tool, uses an organizationally unique identifier (OID) of 0x00601A, D protocol identifier (PID) of 0x0001. Each version has a typical payload string. For example, NetStumbler 3.2.3 has a payload string: 'All your 802.11b are belong to us'. Therefore, when you see the OID and PID values, you discover that the attacker is using NetStumbler, and when you see the payload string, you are able to ascertain that the attacker is using NetStumbler 3.2.3.
Question 40
- (Topic 3)
Which of the following listeners need not be configured in the deployment descriptor? (Choose two)
Correct Answer:AD
Except for the HttpSessionActivationListener and the HttpSessionBindingListener, all other listeners must be configured in the deployment descriptor.
HttpSessionBindingListener has methods that notify the object when it is added to or removed from a session. It has methods that informs the attributes when the session is about to be activated or passivated. These methods are related to the attributes and not to the complete session. Hence, the container takes care of them and need not be configured in the deployment descriptor.
Question 41
- (Topic 3)
Which of the following statements are true about WPA?
Correct Answer:ABCD
WPA stands for Wi-Fi Protected Access. It is a wireless security standard. It provides better security than WEP (Wired Equivalent Protection). Windows Vista supports both WPA-PSK and WPA-EAP. Each of these is described as follows: WPA-PSK: PSK stands for Preshared key. This standard is meant for home environment. WPA-PSK requires a user to enter an 8- character to 63-character passphrase into a wireless client. The WPA converts the passphrase into a 256-bit key. WPA-EAP: EAP stands for Extensible Authentication Protocol. This standard relies on a back-end server that runs Remote Authentication Dial-In User Service for user authentication. Note: Windows Vista supports a user to use a smart card to connect to a WPA-EAP protected network. Shared- key WPA is vulnerable to password cracking attacks if a weak passphrase is used. To protect against a brute force attack, a truly random passphrase of 13 characters (selected from the set of 95 permitted characters) is probably sufficient.
Question 42
- (Topic 1)
George works as an office assistant in Soft Well Inc. The company uses the Windows Vista operating system. He wants to disable a program running on a computer. Which of the following Windows Defender tools will he use to accomplish the task?
Correct Answer:D
Software Explorer is used to remove, enable, or disable a program running on a computer. Answer A is incorrect. Allowed items contains a list of all the programs that a user has chosen not to monitor with Windows Defender. Answer C is incorrect. Options is used to choose how Windows Defender should monitor all the programs running on a computer. Answer B is incorrect. Quarantined items is used to remove or restore a program blocked by Windows Defender.