Question 67
- (Topic 3)
Which of the following wireless security standards supported by Windows Vista provides the highest level of security?
Correct Answer:D
WPA2 is an updated version of WPA. This standard is also known as IEEE 802.11i. WPA2 offers enhanced protection to wireless networks than WPA and WEP standards. It is also available as WPA2-PSK and WPA2-EAP for home and enterprise environment respectively. Answer B is incorrect. than WEP (Wired Equivalent Protection).
Windows Vista supports both WPA-PSK and WPA-EAP. Each of these is described as follows: WPA-PSK: PSK stands for Preshared key. This standard is meant for home environment. WPA-PSK requires a user to enter an 8- character to 63-character passphrase into a wireless client. The WPA converts the passphrase into a 256-bit key. WPA-EAP: EAP stands for Extensible Authentication Protocol. This standard relies on a back-end server that runs Remote Authentication Dial-In User Service for user authentication. Note: Windows Vista supports a user to use a smart card to connect to a WPA-EAP protected network.
Question 68
- (Topic 4)
Adam works as a Security Analyst for Umbrella Inc. He is retrieving large amount of log data from syslog servers and network devices such as Router and switches. He is facing difficulty in analyzing the logs that he has retrieved. To solve this problem, Adam decides to use software called Sawmill. Which of the following statements are true about Sawmill?
Correct Answer:ABC
Sawmill is a software package for the statistical analysis and reporting of log files, with dynamic contextual filtering, 'live' data zooming, user interface customization, and custom calculated reports. Sawmill incorporates real-time reporting and real-time alerting. Sawmill also includes a page tagging server and JavaScript page tag for the analysis of client side
clicks (client requests) providing a total view of visitor traffic and on-site behavioral activity. Sawmill Analytics is offered in three forms, as a software package for user deployment, as a turnkey on-premise system appliance, and as a SaaS service. Sawmill analyzes any device or software package producing a log file and that includes Web servers, firewalls, proxy servers, mail servers, network devices (switches & routers etc.), syslog servers, databases etc. Its range of potential uses by knowledge workers is essentially limitless. Answer D is incorrect. Sawmill Analytics software is available in three different forms; as a software package for user deployment, as a turnkey on-premise system appliance, and as a SaaS service.
Question 69
- (Topic 1)
An auditor assesses the database environment before beginning the audit. This includes various key tasks that should be performed by an auditor to identify and prioritize the users, data, activities, and applications to be monitored. Which of the following tasks need to be performed by the auditor manually?
Correct Answer:AC
The Internal Audit Association lists the following as key components of a database audit: Create an inventory of all database systems and use classifications. This should include production and test data. Keep it up-to-date. Classify data risk within the database systems. Monitoring should be prioritized for high, medium, and low risk data. Implement an access request process that requires database owners to authorize the "roles" granted to database accounts (roles as in Role Based Access and not the native database roles). Analyze access authority. Users with higher degrees of access permission should be under higher scrutiny, and any account for which access has been suspended should be monitored to ensure access is denieA, Dttempts are identified. Assess application coverage. Determine what applications have built-in controls, and prioritize database auditing accordingly. All privileged user access must have audit priority. Legacy and custom applications are the next highest priority to consider, followed by the packaged applications. Ensure technical safeguards. Make sure access controls are set properly. Audit the activities. Monitor data changes and modifications to the database structure, permission and user changes, and data viewing activities. Consider using network-based database activity monitoring appliances instead of native database audit trails. Archive, analyze, review, and report audit information. Reports to auditors and IT managers must communicate relevant audit information, which can be analyzed and reviewed to determine if corrective action is required. Organizations that must retain audit data for long-term use should archive this information with the ability to retrieve relevant data when needed. The first five steps listed are to be performed by the auditor manually. Answer B, D are incorrect. These tasks are best achieved by using an automated solution.
Question 70
- (Topic 1)
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to see the list of the filesystems mounted automatically at startup by the mount -a command in the /etc/rc startup file. Which of the following Unix configuration files can you use to accomplish the task?
Correct Answer:D
In Unix, the /etc/fstab file is used by system administrators to list the filesystems that are mounted automatically at startup by the mount –a command (in /etc/rc or its equivalent startup file). Answer C is incorrect. In Unix, the /etc/mtab file contains a list of the currently mounted file systems. This is set up by the boot scripts and updated by the mount command. Answer A is incorrect. In Unix, the /etc/named.conf file is used for domain name servers. Answer B is incorrect. In Unix, the /etc/groups file contains passwords to let a user join a group.
Question 71
- (Topic 3)
Which of the following is a basic feature of the Unix operating system? (Choose three)
Correct Answer:ABD
The basic features of Unix are as follows: Multi-user: It supports more than one user to access the system simultaneously through a set of terminals attached to a system. Multi-tasking: A user can execute multiple programs at the same time from a single terminal. Time sharing: The operating system shares CPU time among tasks. Portability: It is highly portable across hardware. Modularity: It allows only needed modules to be loaded into the memory. File structure: It has an inverted tree like file structure, with files and directories created within the file structure. Security: All files can be individually protected using read, write, and execute permissions for the user, group, and others. Network support: It uses the TCP/IP protocol. Advanced graphics: CAD-CAM applications perform the best in a Unix System with its varied support for graphics card.
Question 72
- (Topic 1)
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to print the super block and block the group information for the filesystem present on a system. Which of the following Unix commands can you use to accomplish the task?
Correct Answer:C
In Unix, the dumpe2fs command dumps the filesystem superblock and blocks the group information. Answer B is incorrect. In Unix, the dump command is used to back up an ext2 filesystem. Answer A is incorrect. The e2fsck command is used to check the second extended file system (E2FS) of a Linux computer. Syntax: e2fsck [options]
/dev/hda1). Several options are used with the e2fsck command. Following is a list of some important options: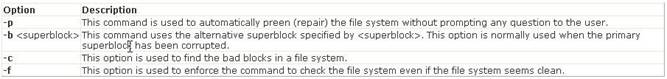
Answer D is incorrect. In Unix, the e2label command is used to change the label of an ext2 filesystem.