Question 31
The Linux command to make the /etc/shadow file, already owned by root, readable only by root is which of the following?
Correct Answer:C
Question 32
Which of the following is a backup strategy?
Correct Answer:A
Question 33
A sensor that uses a light beam and a detecting plate to alarm if the light beam is obstructed is most commonly used to identify which of the following threats?
Correct Answer:B
Question 34
Which of the following statements about IPSec are true?
Each correct answer represents a complete solution. Choose two.
Correct Answer:BD
Question 35
Analyze the screenshot below. What is the purpose of this message?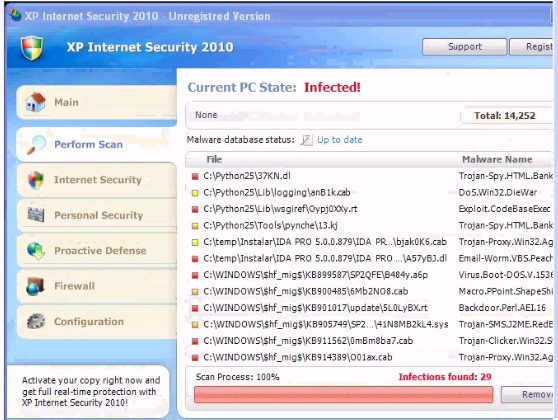
Correct Answer:D
Question 36
You work as a Network Administrator for NetTech Inc. The company wants to encrypt its e-mails. Which of the following will you use to accomplish this?
Correct Answer:C