Question 61
Where is the source address located in an IPv4 header?
Correct Answer:D
Question 62
An employee is currently logged into the corporate web server, without permission. You log into the web server as 'admin" and look for the employee's username: "dmaul" using the "who" command. This is what you get back: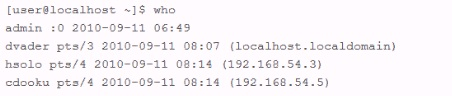
Correct Answer:B
Question 63
Which of the following books deals with confidentiality?
Correct Answer:B
Question 64
An IT security manager is trying to quickly assess the risks associated with not implementing a corporate firewall system. What sort of risk assessment is most appropriate?
Correct Answer:B
Question 65
How many bytes does it take to represent the hexadecimal value OxFEDCBA?
Correct Answer:C
Question 66
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we- are-secure.com. He installs a rootkit on the Linux server of the We-are-secure network. Which of the following statements are true about rootkits?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:BCD