Question 97
- (Topic 3)
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we-are-secure.com. He has to ping 500 computers to find out whether these computers are connected to the server or not. Which of the following will he use to ping these computers?
Correct Answer:C
Question 98
- (Topic 1)
You are conducting a penetration test for a private company located in Canada. The scope extends to all internal-facing hosts controlled by the company. You have gathered necessary hold-harmless and non-disclosure agreements. Which action by your group can incur criminal liability under Criminal Code of Canada Sections 184 and 542 CC 184?
Correct Answer:D
Question 99
- (Topic 1)
You've been asked to test a non-transparent proxy lo make sure it is working. After confirming the browser is correctly pointed at the proxy, you try to browse a web site. The browser indicates it is "loading" but never displays any part the page. Checking the proxy, you see a valid request in the proxy from your browser. Checking the response to the proxy, you see the results displayed in the accompanying screenshot. Which of the following answers is the most likely reason the browser hasn't displayed the page yet? 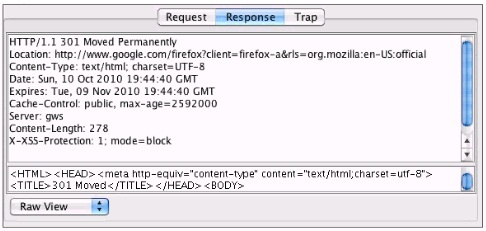
Correct Answer:C
Question 100
- (Topic 4)
Which of the following penetration testing phases involves gathering data from whois, DNS, and network scanning, which helps in mapping a target network and provides valuable information regarding the operating system and applications running on the systems?
Correct Answer:D
Question 101
- (Topic 3)
Which of the following are the countermeasures against WEP cracking? Each correct answer represents a part of the solution. Choose all that apply.
Correct Answer:BCD
Question 102
- (Topic 4)
Victor wants to use Wireless Zero Configuration (WZC) to establish a wireless network connection using his computer running on Windows XP operating system. Which of the
following are the most likely threats to his computer?
Each correct answer represents a complete solution. Choose two.
Correct Answer:BC