Question 91
- (Topic 1)
In the screen shot below, which selections would you need click in order to intercept and alter all http traffic passing through OWASP ZAP? 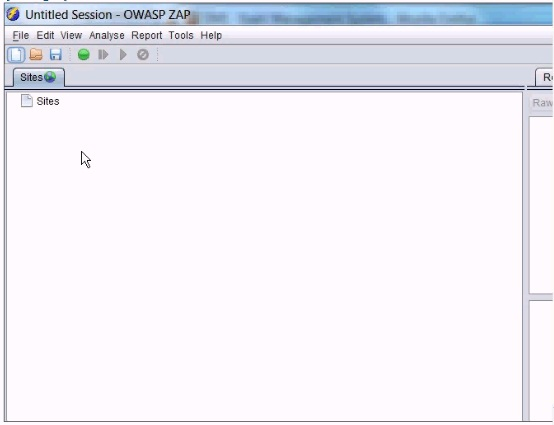
Correct Answer:B
Question 92
- (Topic 4)
You want that some of your Web pages should not be crawled. Which one of the following options will you use to accomplish the task?
Correct Answer:C
Question 93
- (Topic 1)
As pan or a penetration lest, your team is tasked with discovering vulnerabilities that could be exploited from an inside threat vector. Which of the following activities fall within that scope?
Correct Answer:C
Question 94
- (Topic 3)
Which of the following attacks can be overcome by applying cryptography?
Correct Answer:B
Question 95
- (Topic 2)
You are sending a file to an FTP server. The file will be broken into several pieces of information packets (segments) and will be sent to the server. The file will again be reassembled and reconstructed once the packets reach the FTP server. Which of the following information should be used to maintain the correct order of information packets during the reconstruction of the file?
Correct Answer:D
Question 96
- (Topic 2)
Which of the following tools can be used as a Linux vulnerability scanner that is capable of identifying operating systems and network services?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:AD