Question 67
- (Topic 2)
Which of the following tools is an automated tool that is used to implement SQL injections and to retrieve data from Web server databases?
Correct Answer:B
Question 68
- (Topic 2)
Which of the following methods will free up bandwidth in a Wireless LAN (WLAN)?
Correct Answer:B
Question 69
- (Topic 1)
You are performing a vulnerability assessment using Nessus and your clients printers begin printing pages of random text and showing error messages. The client is not happy with the situation. What is the best way to proceed?
Correct Answer:B
Question 70
- (Topic 1)
Identify the network activity shown below; 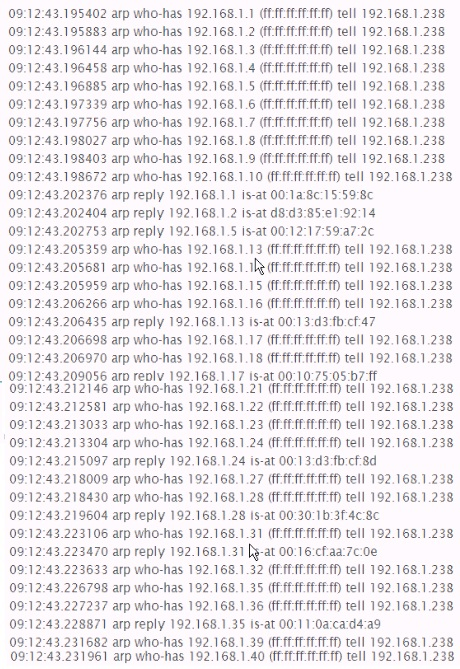
Correct Answer:D
Question 71
- (Topic 2)
Analyze the screenshot below, which of the following sets of results will be retrieved using this search? 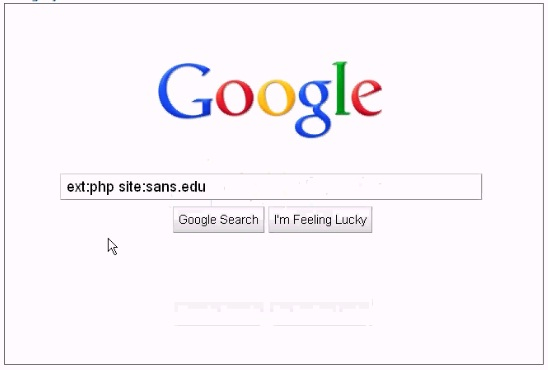
Correct Answer:A
Question 72
- (Topic 1)
A penetration tester used a client-side browser exploit from metasploit to get an unprivileged shell prompt on the target Windows desktop. The penetration tester then tried using the getsystem command to perform a local privilege escalation which failed. Which of the following could resolve the problem?
Correct Answer:B