Question 25
In which of the following malicious hacking steps does email tracking come under?
Correct Answer:A
Question 26
Alice wants to prove her identity to Bob. Bob requests her password as proof of identity, which Alice dutifully provides (possibly after some transformation like a hash function); meanwhile, Eve is eavesdropping the conversation and keeps the password. After the interchange is over, Eve connects to Bob posing as Alice; when asked for a proof of identity, Eve sends Alice's password read from the last session, which Bob accepts. Which of the following attacks is being used by Eve?
Correct Answer:A
Question 27
John works as an Ethical Hacker for Exambible Inc. He wants to find out the ports that are open in Exambible's server using a port scanner. However, he does not want to establish a full TCP connection.
Which of the following scanning techniques will he use to accomplish this task?
Correct Answer:C
Question 28
Which of the following attacks allows an attacker to sniff data frames on a local area network (LAN) or stop the traffic altogether?
Correct Answer:B
Question 29
Choose the correct six -step process of threat modeling from the list of different steps.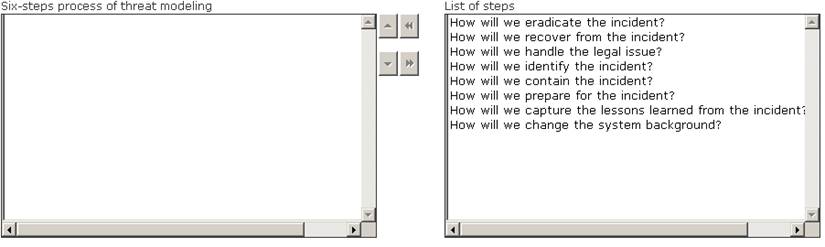
Solution: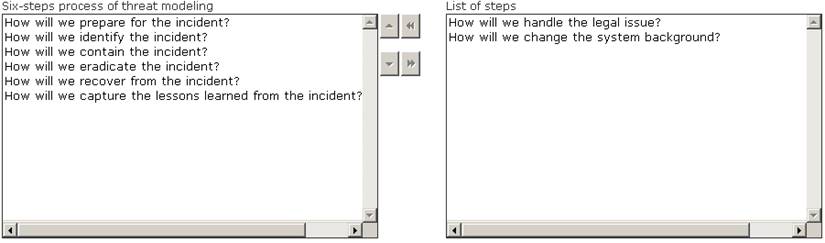
Does this meet the goal?
Correct Answer:A
Question 30
Which of the following attacks come under the category of layer 2 Denial-of-Service attacks?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:AB