Question 7
You are concerned about rootkits on your network communicating with attackers outside your network. Without using an IDS how can you detect this sort of activity?
Correct Answer:C
Question 8
Choose the correct actions performed during the Eradication step of the incident handling process.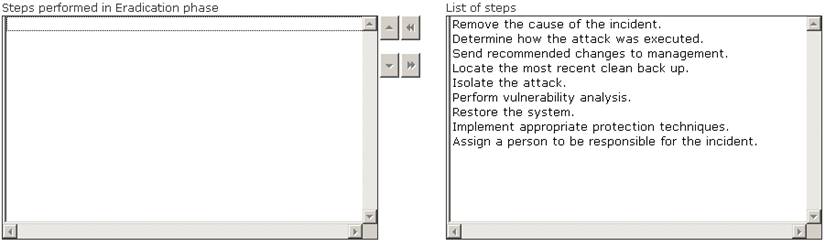
Solution: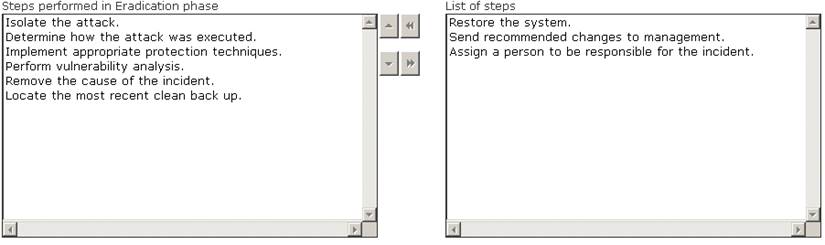
Does this meet the goal?
Correct Answer:A
Question 9
Which of the following provides packet-level encryption between hosts in a LAN?
Correct Answer:B
Question 10
CORRECT TEXT
Fill in the blank with the appropriate name of the rootkit.
A _______ rootkit uses device or platform firmware to create a persistent malware image.
Correct Answer:firmware
Question 11
Which of the following malicious software travels across computer networks without the assistance of a user?
Correct Answer:A
Question 12
Which of the following types of scan does not open a full TCP connection?
Correct Answer:C