Online GCIH Practice TestMore GIAC Products >
Free GIAC GCIH Exam Dumps Questions
GIAC GCIH: GIAC Certified Incident Handler
- Get instant access to GCIH practice exam questions
- Get ready to pass the GIAC Certified Incident Handler exam right now using our GIAC GCIH exam package, which includes GIAC GCIH practice test plus an GIAC GCIH Exam Simulator.
- The best online GCIH exam study material and preparation tool is here.
Question 1
Rick works as a Professional Ethical Hacker for Exambible Inc. The company has opened a new branch that uses Windows-based computers. Rick has been assigned a project to check the network security of the new branch office. He wants to ensure that the company is free from remote hacking attacks.
Choose the appropriate steps that Rick should perform to accomplish the task. 
Solution: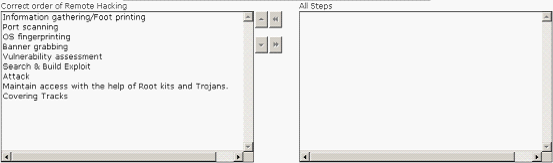
Does this meet the goal?
Correct Answer:A
Question 2
Your friend plans to install a Trojan on your computer. He knows that if he gives you a new version of chess.exe, you will definitely install the game on your computer. He picks up a Trojan and joins it with chess.exe. Which of the following tools are required in such a scenario?
Each correct answer represents a part of the solution. Choose three.
Correct Answer:ACD
Question 3
Which of the following languages are vulnerable to a buffer overflow attack?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:BC
Question 4
Adam, a malicious hacker purposely sends fragmented ICMP packets to a remote target. The total size of this ICMP packet once reconstructed is over 65,536 bytes. On the basis of above information, which of the following types of attack is Adam attempting to perform?
Correct Answer:B
Question 5
Which of the following viruses/worms uses the buffer overflow attack?
Correct Answer:D
Question 6
Which of the following attacks capture the secret value like a hash and reuse it later to gain access to a system without ever decrypting or decoding the hash?
Correct Answer:B