Question 19
John works as a professional Ethical Hacker for SecureEnet Inc. The company has a Windowsbased network. All client computers run on Windows XP. A project has been assigned to John to investigate about the open ports responsible for various malicious attacks on the network. John wants to use the DOS command-line utility to find out the open ports. Which of the following DOS commands will John use to accomplish the task?
Correct Answer:D
Question 20
The following output is generated by running the show ip route command:
RouterA#show ip route
< - - Output Omitted for brevity - -> 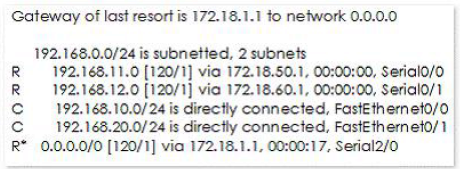
Which next hop address will RouterA use in forwarding traffic to 10.10.100.0/24?
Correct Answer:C
Question 21
Which of the following is the best method of accurately identifying the services running on a victim host?
Correct Answer:D
Question 22
You are the Network Administrator for a large corporate network. You want to monitor all network traffic on your local network for suspicious activities and receive a notification when a possible attack is in process. Which of the following actions will you take for this?
Correct Answer:B
Question 23
Which of the following organizations is dedicated to computer security research and information sharing?
Correct Answer:C
Question 24
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate computer of an unfaithful employee of SecureEnet Inc. Suspect's computer runs on Windows operating system. Which of the following sources will Adam investigate on a Windows host to collect the electronic evidences?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:BCD