Online FCSS_SASE_AD-23 Practice TestMore Fortinet Products >
Free Fortinet FCSS_SASE_AD-23 Exam Dumps Questions
Fortinet FCSS_SASE_AD-23: FCSS FortiSASE 23 Administrator
- Get instant access to FCSS_SASE_AD-23 practice exam questions
- Get ready to pass the FCSS FortiSASE 23 Administrator exam right now using our Fortinet FCSS_SASE_AD-23 exam package, which includes Fortinet FCSS_SASE_AD-23 practice test plus an Fortinet FCSS_SASE_AD-23 Exam Simulator.
- The best online FCSS_SASE_AD-23 exam study material and preparation tool is here.
Question 1
Which two advantages does FortiSASE bring to businesses with multiple branch offices? (Choose two.)
Correct Answer:AD
FortiSASE brings the following advantages to businesses with multiple branch offices:
✑ Centralized Management for Simplified Administration:
✑ Eliminates the Need for On-Premises Firewalls:
References:
✑ FortiOS 7.2 Administration Guide: Provides information on the benefits of centralized management and cloud-based security solutions.
✑ FortiSASE 23.2 Documentation: Explains the advantages of using FortiSASE for businesses with multiple branch offices, including reduced need for on-premises firewalls.
Question 2
You are designing a new network for Company X and one of the new cybersecurity policy requirements is that all remote user endpoints must always be connected and protected Which FortiSASE componentfacilitates this always-on security measure?
Correct Answer:C
The unified FortiClient component of FortiSASE facilitates the always-on security measure required for ensuring that all remote user endpoints are always connected and protected.
✑ Unified FortiClient:
✑ Always-On Security:
References:
✑ FortiOS 7.2 Administration Guide: Provides information on configuring and managing FortiClient for endpoint security.
✑ FortiSASE 23.2 Documentation: Explains how FortiClient integrates with FortiSASE to deliver always-on security for remote endpoints.
Question 3
Refer to the exhibit.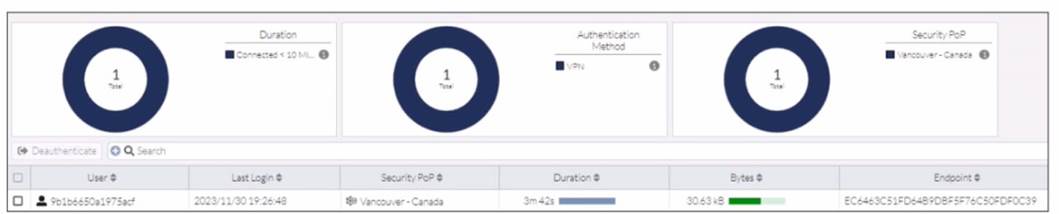
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters. Which configuration change must the administrator make to get proper user information?
Correct Answer:A
In the user connection monitor, the random characters shown for the username indicate that log anonymization is enabled. Log anonymization is a feature that hides the actual user information in the logs for privacy and security reasons. To display proper user information, you need to disable log anonymization.
✑ Log Anonymization:
✑ Disabling Log Anonymization:
References:
✑ FortiSASE 23.2 Documentation: Provides detailed steps on enabling and disabling log anonymization.
✑ Fortinet Knowledge Base: Explains the impact of log anonymization on user monitoring and logging.
Question 4
When deploying FortiSASE agent-based clients, which three features are available compared to an agentless solution? (Choose three.)
Correct Answer:ABD
When deploying FortiSASE agent-based clients, several features are available that are not typically available with an agentless solution. These features enhance the security and management capabilities for endpoints.
✑ Vulnerability Scan:
✑ SSL Inspection:
✑ Web Filter:
References:
✑ FortiOS 7.2 Administration Guide: Explains the features and benefits of deploying agent-based clients.
✑ FortiSASE 23.2 Documentation: Details the differences between agent-based and agentless solutions and the additional features provided by agent-based deployments.
Question 5
An organization wants to block all video and audio application traffic but grant access to videos from CNN Which application override action must you configure in the Application Control with Inline-CASB?
Correct Answer:D
✑ Application Control Configuration:
✑ Blocking Video and Audio Applications:
✑ Granting Access to Specific Videos (CNN):
✑ Configuration Steps:
References:
✑ FortiOS 7.2 Administration Guide: Detailed steps on configuring Application Control and Inline-CASB.
✑ Fortinet Training Institute: Provides scenarios and examples of using Application Control with Inline-CASB for specific use cases.
Question 6
Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)
Correct Answer:AB
Onboarding a Secure Web Gateway (SWG) endpoint involves several components to
ensure secure and effective integration with FortiSASE. Two key components are the FortiSASE CA certificate and the proxy auto-configuration (PAC) file.
✑ FortiSASE CA Certificate:
✑ Proxy Auto-Configuration (PAC) File:
References:
✑ FortiOS 7.2 Administration Guide: Details on onboarding endpoints and configuring SWG.
✑ FortiSASE 23.2 Documentation: Explains the components required for integrating endpoints with FortiSASE and the process for deploying the CA certificate and PAC file.