Question 13
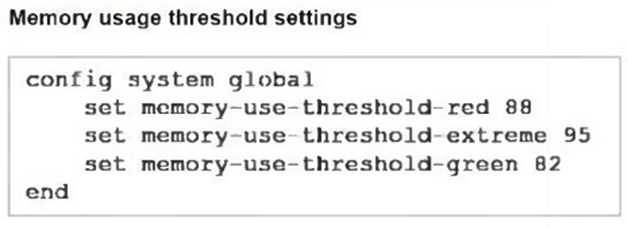
Refer to the exhibits, which show the system performance output and the default configuration of high memory usage thresholds in a FortiGate.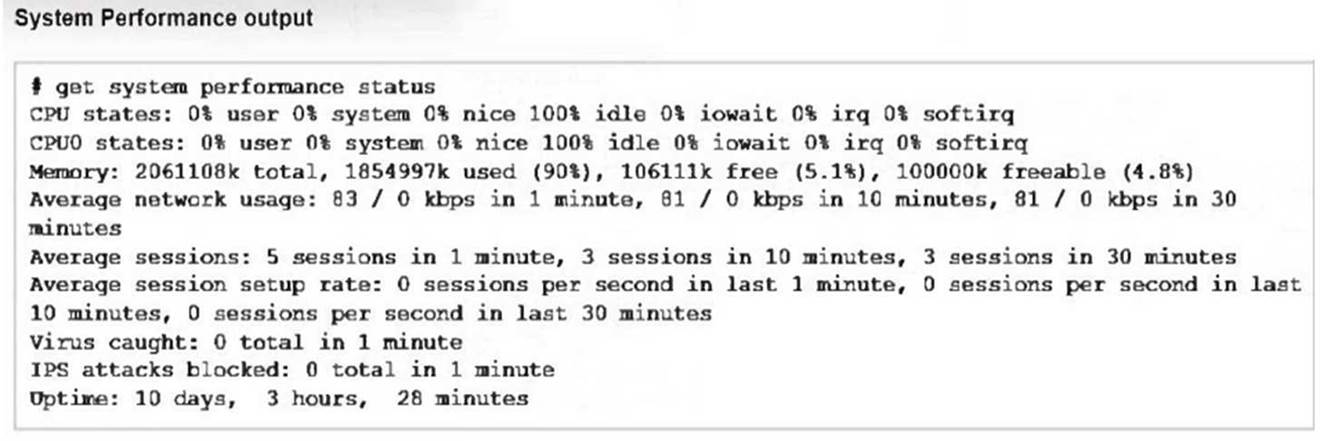
Based on the system performance output, what can be the two possible outcomes? (Choose two.)
Correct Answer:BC
Based on the system performance output provided, the memory usage on the FortiGate device is at 90%, which is above the green threshold (82%) but below the red threshold (88%). Given this high memory usage, the FortiGate device will enter "conserve mode" to prevent further resource exhaustion. In conserve mode: B. FortiGate has entered conserve mode: When the memory usage reaches or exceeds certain thresholds (in this case, the green and red thresholds), the FortiGate enters conserve mode to protect itself from running out of memory entirely. This mode limits some functionalities to reduce memory usage and avoid a potential system crash.
B. FortiGate has entered conserve mode: When the memory usage reaches or exceeds certain thresholds (in this case, the green and red thresholds), the FortiGate enters conserve mode to protect itself from running out of memory entirely. This mode limits some functionalities to reduce memory usage and avoid a potential system crash. D. Administrators can access FortiGate only through the console port: During conserve mode, administrative access might be restricted, and administrators may only be able to connect to the device via the console port. This restriction is in place to ensure that the FortiGate can be managed directly, even under low resource conditions.
D. Administrators can access FortiGate only through the console port: During conserve mode, administrative access might be restricted, and administrators may only be able to connect to the device via the console port. This restriction is in place to ensure that the FortiGate can be managed directly, even under low resource conditions.
The other options are not correct: A. FortiGate will start sending all files to FortiSandbox for inspection: This is unrelated to memory usage and conserve mode.
A. FortiGate will start sending all files to FortiSandbox for inspection: This is unrelated to memory usage and conserve mode. C. Administrators cannot change the configuration: While access may be limited, configuration changes can still be made via the console port.
C. Administrators cannot change the configuration: While access may be limited, configuration changes can still be made via the console port.
References FortiOS 7.4.1 Administration Guide - Monitoring System Resources and Performance, page 325.
FortiOS 7.4.1 Administration Guide - Monitoring System Resources and Performance, page 325.  FortiOS 7.4.1 Administration Guide - Conserve Mode, page 330.
FortiOS 7.4.1 Administration Guide - Conserve Mode, page 330.
Question 14
Which method allows management access to the FortiGate CLI without network connectivity?
Correct Answer:C
The serial console method allows management access to the FortiGate CLI without relying on network connectivity. This method involves directly connecting a computer to the FortiGate device using a serial cable (such as a DB-9 to RJ-45 cable or USB to RJ-45 cable) and using terminal emulation software to interact with the FortiGate CLI. This method is essential for situations where network-based access methods (such as SSH or Telnet) are not available or feasible.
References: FortiOS 7.4.1 Administration Guide: Console connection
FortiOS 7.4.1 Administration Guide: Console connection
Question 15
Which two statements describe how the RPF check is used? (Choose two.)
Correct Answer:AD
The Reverse Path Forwarding (RPF) check is run on the first sent packet of any new session to ensure that the packet arrives on a legitimate interface. This check protects the network from IP spoofing attacks by verifying that a return route exists from the receiving interface back to the source IP address. If the route is invalid or not found, the packet is discarded. Options B and C are incorrect because RPF checks are performed on the first sent packet, not the reply packet.
References: FortiOS 7.4.1 Administration Guide: Reverse Path Forwarding (RPF) Check
FortiOS 7.4.1 Administration Guide: Reverse Path Forwarding (RPF) Check