Question 7
Refer to the exhibit.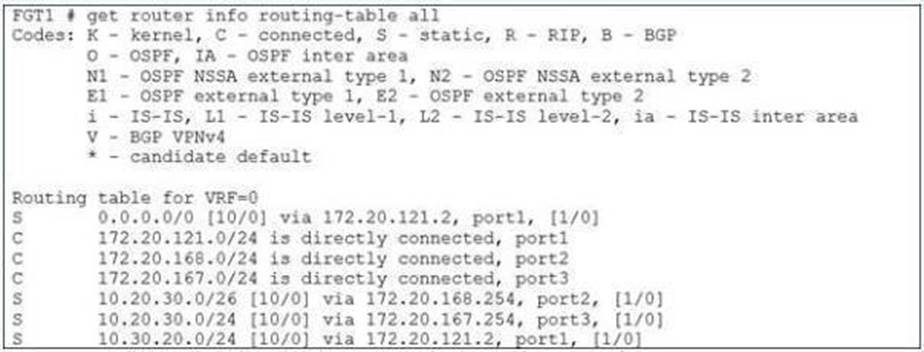
Which route will be selected when trying to reach 10.20.30.254?
Correct Answer:A
The correct route selected when trying to reach 10.20.30.254 is 10.20.30.0/24 [10/0] via 172.20.167.254,
port3, [1/0].
Prefix Length: The routing process prioritizes routes with the most specific (longest) prefix. In this case, 10.20.30.0/24 has a shorter prefix than 10.20.30.0/26 (option C), but it still matches the target address 10.20.30.254. The /24 subnet includes all addresses from 10.20.30.0 to 10.20.30.255, so 10.20.30.254 falls within this range.
• Administrative Distance and Metric: In the exhibit, all routes have the same administrative distance (AD) and metric, meaning they are considered equal in terms of preference. Hence, the prefix length becomes the primary factor for route selection.
Why the other options are less appropriate: B. 10.30.20.0/24 [10/0] via 172.20.121.2, port1, [1/0]
B. 10.30.20.0/24 [10/0] via 172.20.121.2, port1, [1/0]
• This route is for a different subnet, 10.30.20.0/24, which does not include the target address 10.20.30.254. Therefore, it is not a valid match. C. 10.20.30.0/26 [10/0] via 172.20.168.254, port2, [1/0]
C. 10.20.30.0/26 [10/0] via 172.20.168.254, port2, [1/0]
• Although this has a more specific prefix (/26), which means it should cover a smaller range of
addresses, the /26 subnet only includes addresses from 10.20.30.0 to 10.20.30.63. The target
address 10.20.30.254 does not fall within this range, so this route will not be selected. D. 0.0.0.0/0 [10/0] via 172.20.121.2, port1, [1/0]
D. 0.0.0.0/0 [10/0] via 172.20.121.2, port1, [1/0]
• This is a default route (0.0.0.0/0) used for any address that doesn??t match a more specific route.
Since 10.20.30.254 matches the 10.20.30.0/24 route (option A), the default route will not be selected.
Question 8
Consider the topology:
Application on a Windows machine <--{SSL VPN} -->FGT--> Telnet to Linux server.
An administrator is investigating a problem where an application establishes a Telnet session to a Linux
server over the SSL VPN through FortiGate and the idle session times out after about 90 minutes. The administrator would like to increase or disable this timeout.
The administrator has already verified that the issue is not caused by the application or Linux server.
This issue does not happen when the application establishes a Telnet connection to the Linux server directly on the LAN.
What two changes can the administrator make to resolve the issue without affecting services running through FortiGate? (Choose two.)
Correct Answer:CD
The issue with the idle session timing out after 90 minutes can be resolved by adjusting the session Time-
To-Live (TTL) for the TELNET service used over the SSL VPN connection. Here's how the administrator
can address the problem:
• C. Create a new service object for TELNET and set the maximum session TTL:
By creating a new service object specifically for TELNET and setting a custom maximum session TTL, the administrator can ensure that the TELNET session does not time out prematurely. This way, the session will last longer or indefinitely, depending on the configured TTL.
• D. Create a new firewall policy and place it above the existing SSLVPN policy for the SSL VPN traffic, and set the new TELNET service object in the policy:
Creating a dedicated firewall policy for SSL VPN traffic and placing it above the existing one allows the administrator to apply the new TELNET service object with a longer session TTL. This will ensure the new policy with the adjusted settings takes precedence for TELNET traffic.
Why the other options are less appropriate:
• A. Set the maximum session TTL value for the TELNET service object:
This would work if you were adjusting an existing TELNET service object. However, creating a new service object for TELNET and applying it in the firewall policy (as described in options C and D) is more granular and won't affect other services using the same TELNET object.
• B. Set the session TTL on the SSLVPN policy to maximum:
While this would extend the session timeout for the entire SSL VPN traffic, it could affect other services running through the SSL VPN, which may not be desirable. This option would lack the necessary specificity for only the TELNET traffic.
Question 9
FortiGate is integrated with FortiAnalyzer and FortiManager.
When a firewall policy is created, which attribute is added to the policy to improve functionality and to support recording logs to FortiAnalyzer or FortiManager?
Correct Answer:D
When a firewall policy is created in FortiGate integrated with FortiAnalyzer and FortiManager, a Universally Unique Identifier (UUID) is added to the policy to support logging and management.
Question 10
Refer to the exhibits.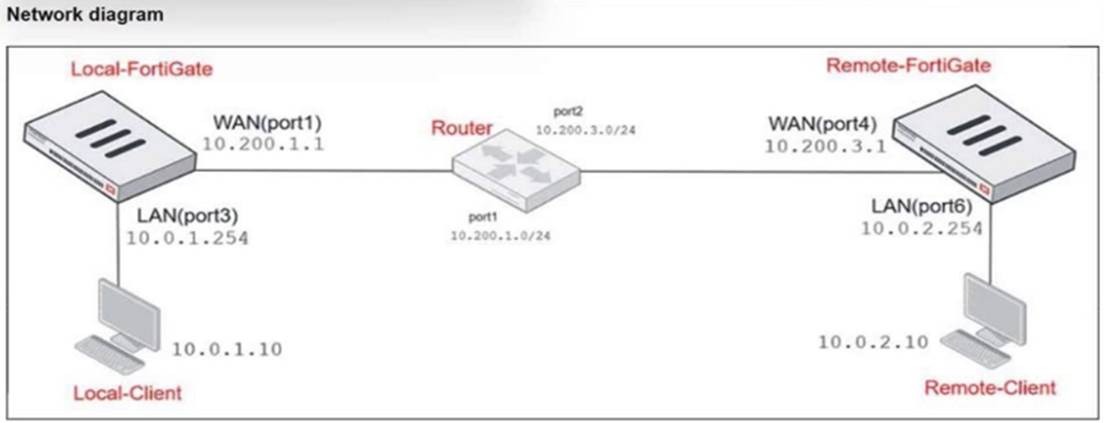
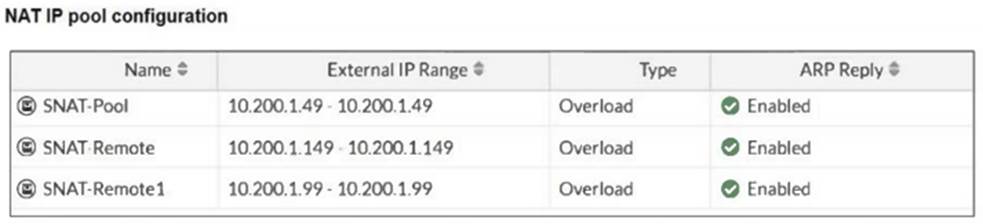
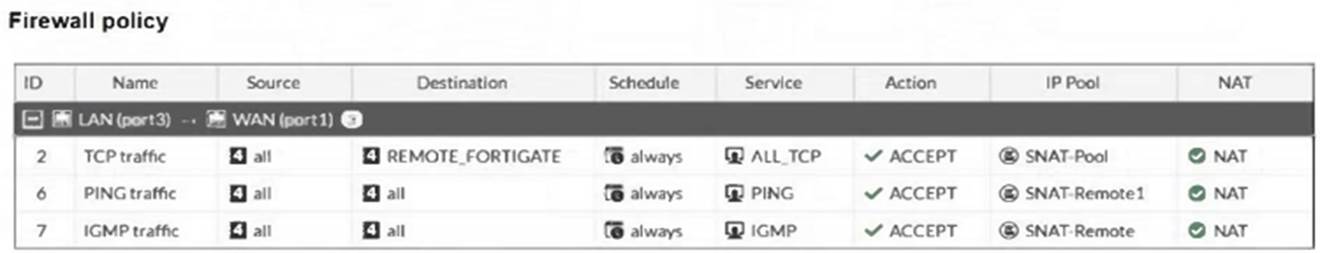
The exhibits show a diagram of a FortiGate device connected to the network, as well as the IP pool configuration and firewall policy objects.
The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port3) interface has the IPaddress 10.0.1.254/24.
Which IP address will be used to source NAT (SNAT) the traffic, if the user on Local-Client (10.0.1.10) pings the IP address of Remote-FortiGate (10.200.3.1)?
Correct Answer:C
The traffic from the user on Local-Client (10.0.1.10) pinging the IP address of Remote-FortiGate (10.200.3.1) will match the firewall policy with the service "PING traffic". According to the firewall policy: Policy ID 6 is set for PING traffic and uses the NAT IP pool "SNAT-Remote1", which is defined as 10.200.1.99.
Policy ID 6 is set for PING traffic and uses the NAT IP pool "SNAT-Remote1", which is defined as 10.200.1.99.
Question 11
Refer to the exhibit.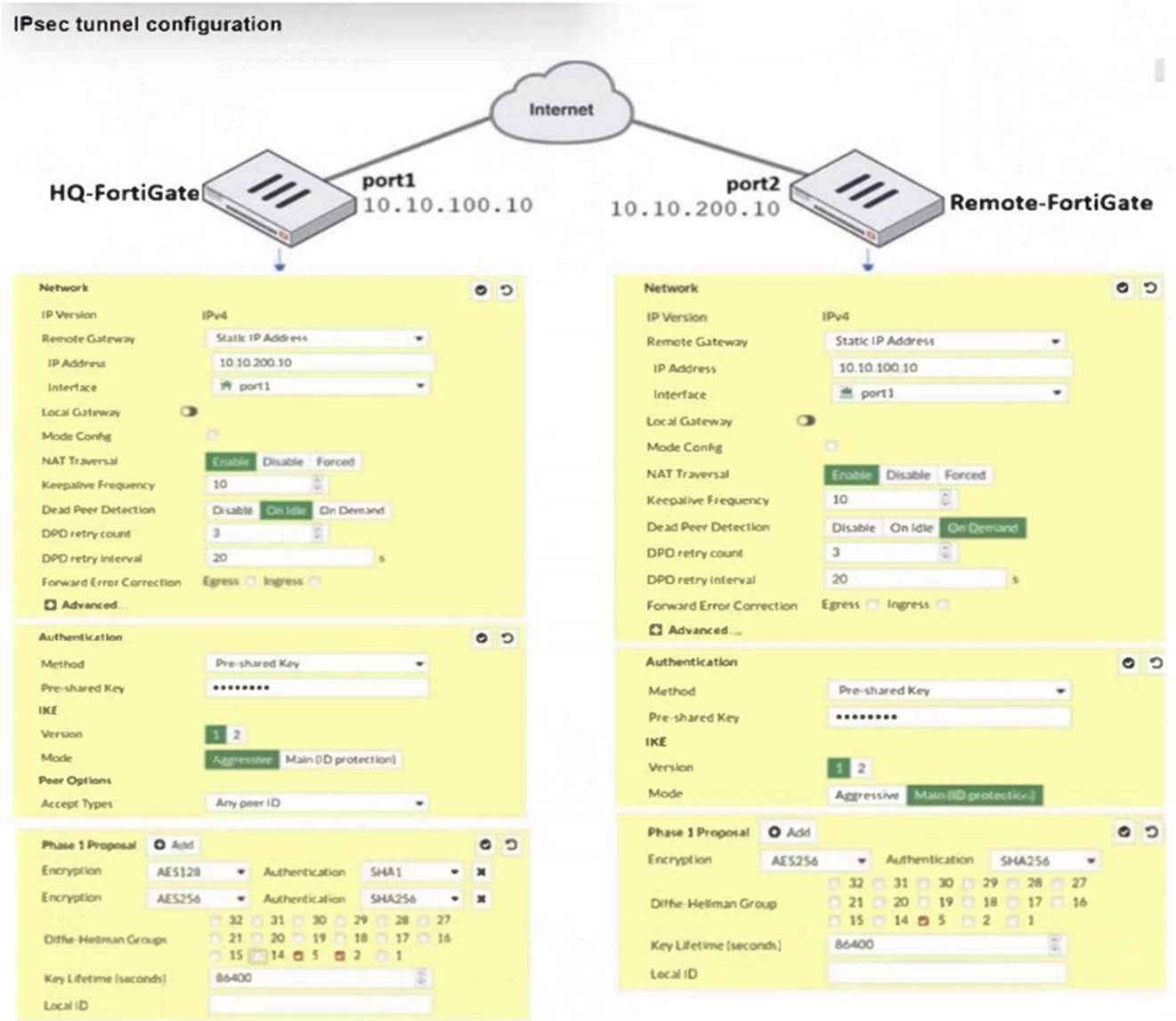
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 failed to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes can the administrator make to bring phase 1 up? (Choose two.)
Correct Answer:CD
To bring Phase 1 up, the following changes can be made: A. On HQ-FortiGate, disable Diffie-Helman group 2: This is incorrect because Diffie-Hellman group 2 is already selected on both devices. Disabling it would not help.
A. On HQ-FortiGate, disable Diffie-Helman group 2: This is incorrect because Diffie-Hellman group 2 is already selected on both devices. Disabling it would not help. B. On Remote-FortiGate, set port2 as Interface: This is incorrect as both sides should be consistent in their interface settings for the IPsec tunnel, and the interface is correctly set to port1 on both FortiGates in the IPsec configuration.
B. On Remote-FortiGate, set port2 as Interface: This is incorrect as both sides should be consistent in their interface settings for the IPsec tunnel, and the interface is correctly set to port1 on both FortiGates in the IPsec configuration. C. On both FortiGate devices, set Dead Peer Detection to On Demand: This is a valid option.
C. On both FortiGate devices, set Dead Peer Detection to On Demand: This is a valid option.
Setting Dead Peer Detection (DPD) to "On Demand" helps maintain the IPsec connection by checking if the peer is still available, which can help in some cases where the connection fails due to timeouts. D. On HQ-FortiGate, set IKE mode to Main (ID protection): This is also a valid option because the Remote-FortiGate is already set to Main mode (ID protection). Ensuring that both ends use the same mode is crucial for successful phase 1 negotiation.
D. On HQ-FortiGate, set IKE mode to Main (ID protection): This is also a valid option because the Remote-FortiGate is already set to Main mode (ID protection). Ensuring that both ends use the same mode is crucial for successful phase 1 negotiation.
Thus, the correct answers are:C. On both FortiGate devices, set Dead Peer Detection to On Demand.D. On HQ-FortiGate, set IKE mode to Main (ID protection).
Question 12
Refer to the exhibits, which show the firewall policy and an antivirus profile configuration.
Why is the user unable to receive a block replacement message when downloading an infected file for the first time?
Correct Answer:D
In flow-based inspection mode, FortiGate sends a reset (RST) packet to the client instead of providing a replacement message, which causes the block message not to be displayed.