Question 49
In the process of hacking a web application, attackers manipulate the HTTP requests to subvert the application authorization schemes by modifying input fields that relate to the user ID, username, access group, cost, file names, file identifiers, etc.
They first access the web application using a low privileged account and then escalate privileges to access protected resources. What attack has been carried out?
Correct Answer:B
Question 50
A Demilitarized Zone (DMZ) is a computer host or small network inserted as a “neutral zone” between a company’s private network and the outside public network. Usage of a protocol within a DMZ environment is highly variable based on the specific needs of an organization.
Privilege escalation, system is compromised when the code runs under root credentials, and DoS attacks are the basic weakness of which one of the following Protocol?
Correct Answer:D
Question 51
A penetration test consists of three phases: pre-attack phase, attack phase, and post-attack phase.
Active reconnaissance which includes activities such as network mapping, web profiling, and perimeter mapping is a part which phase(s)?
Correct Answer:D
Question 52
NTP protocol is used to synchronize the system clocks of computers with a remote time server or time source over a network. Which one of the following ports is used by NTP as its transport layer?
Correct Answer:C
Question 53
What is the target host IP in the following command?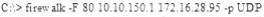
Correct Answer:A
Question 54
Which one of the following tools of trade is an automated, comprehensive penetration testing product for assessing the specific information security threats to an organization?
Correct Answer:C