Question 25
Which of the following statements is true about the LM hash?
Correct Answer:A
Question 26
Which of the following will not handle routing protocols properly?
Correct Answer:B
Question 27
Identify the person who will lead the penetration-testing project and be the client point of contact.
Correct Answer:C
Question 28
Wireshark is a network analyzer. It reads packets from the network, decodes them, and presents them in an easy-to-understand format. Which one of the following is the command-line version of Wireshark, which can be used to capture the live packets from the wire or to read the saved capture files?
Correct Answer:B
Question 29
Windows stores user passwords in the Security Accounts Manager database (SAM), or in the Active Directory database in domains. Passwords are never stored in clear text; passwords are hashed and the results are stored in the SAM.
NTLM and LM authentication protocols are used to securely store a user's password in the SAM database using different hashing methods.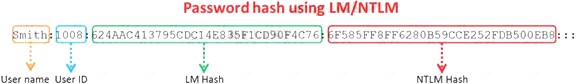
The SAM file in Windows Server 2008 is located in which of the following locations?
Correct Answer:D
Question 30
Identify the type of authentication mechanism represented below: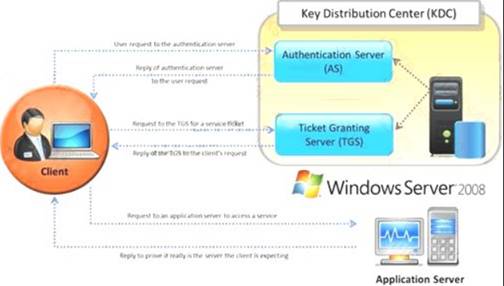
Correct Answer:D