Question 13
Identify the policy that defines the standards for the organizational network connectivity and security standards for computers that are connected in the organizational network.
Correct Answer:C
Question 14
You are assisting a Department of Defense contract company to become compliant with the stringent
security policies set by the DoD. One such strict rule is that firewalls must only allow incoming connections that were first initiated by internal computers.
What type of firewall must you implement to abide by this policy?
Correct Answer:D
Question 15
You have compromised a lower-level administrator account on an Active Directory network of a small company in Dallas, Texas. You discover Domain Controllers through enumeration. You connect to one of the Domain Controllers on port 389 using Idp.exe.
What are you trying to accomplish here?
Correct Answer:D
Question 16
Why is a legal agreement important to have before launching a penetration test?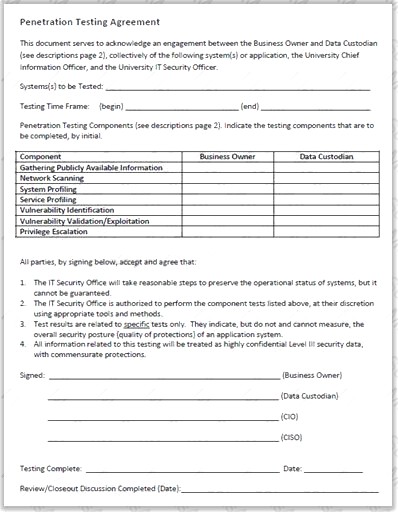
Correct Answer:C
Question 17
One needs to run “Scan Server Configuration” tool to allow a remote connection to Nessus from the remote Nessus clients. This tool allows the port and bound interface of the Nessus daemon to be configured.
By default, the Nessus daemon listens to connections on which one of the following?
Correct Answer:A
Question 18
Identify the framework that comprises of five levels to guide agency assessment of their security programs and assist in prioritizing efforts for improvement:
Correct Answer:D