Question 91
Which of the following is generally used in packages in order to determine the package or product tampering?
Correct Answer:A
Tamper resistance is resistance tampered by the users of a product, package, or system, or the users who can physically access it. It includes simple as well as complex devices. The complex device encrypts all the information between individual chips, or renders itself inoperable. Tamper resistance is generally used in packages in order to determine package or product tampering. Answer B is incorrect. Tamper evident specifies a process or device that makes unauthorized access to the protected object easily detected. Answer D is incorrect. Tamper proofing makes computers resistant to interference. Tamper proofing measures include automatic removal of sensitive information, automatic shutdown, and automatic physical locking. Answer B is incorrect. Tamper data is used to view and modify the HTTP or HTTPS headers and post parameters.
Question 92
Which of the following processes provides a standard set of activities, general tasks, and a management structure to certify and accredit systems, which maintain the information assurance and the security posture of a system or site?
Correct Answer:B
NIACAP is a process, which provides a standard set of activities, general tasks, and a management structure to certify and accredit systems that maintain the information assurance and the security posture of a system or site. Answer D is incorrect. DITSCAP is a process, which establishes a standard process, a set of activities, general task descriptions, and a management structure to certify and accredit the IT systems that will maintain the required security posture. Answer A is incorrect. The NSA-IAM evaluates information systems at a high level and uses a subset of the SSE-CMM process areas to measure the implementation of information security on these systems. Answer C is incorrect. ASSET is a tool developed by NIST to automate the process of self-assessment through the use of the questionnaire in NIST.
Question 93
Which of the following allows multiple operating systems (guests) to run concurrently on a host computer?
Correct Answer:B
A hypervisor is a virtualization technique that allows multiple operating systems (guests) to run concurrently on a host computer. It is also called the virtual machine monitor (VMM). The hypervisor provides a virtual operating platform to the guest operating systems and checks their execution process. It provides isolation to the host's resources. The hypervisor is installed on server hardware. Answer A is incorrect. Emulator duplicates the functions of one system using a different system, so that the second system behaves like the first system. Answer D is incorrect. CP/CMS is a time-sharing operating system of the late 60s and early 70s, and it is known for its excellent performance and advanced features. Answer B is incorrect. Grid computing refers to the combination of computer resources from multiple administrative domains to achieve a common goal.
Question 94
DRAG DROPSecurity code review identifies the unvalidated input calls made by an attacker and avoids those calls to be processed by the server. It performs various review checks on the stained
calls of servlet for identifying unvalidated input from the attacker. Choose the appropriate review checks and drop them in front of their respective functions.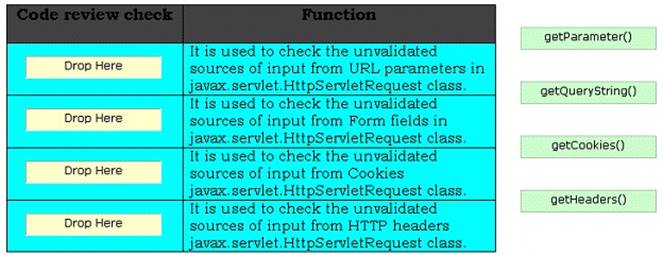
Solution:
The various security code review checks performed on the stained calls of servlet are as follows: getParameter(): It is used to check the unvalidated sources of input from URL parameters in javax.servlet.HttpServletRequest class. getQueryString(): It is used to check the unvalidated sources of input from Form fields in javax.servlet.HttpServletRequest class. getCookies(): It is used to check the unvalidated sources of input from Cookies javax.servlet.HttpServletRequest class. getHeaders(): It is used to check the unvalidated sources of input from HTTP headers javax.servlet.HttpServletRequest class.
Does this meet the goal?
Correct Answer:A
Question 95
An organization monitors the hard disks of its employees' computers from time to time. Which policy does this pertain to?
Correct Answer:C
Monitoring the computer hard disks or e-mails of employees pertains to the privacy policy of an organization. Answer A is incorrect. The backup policy of a company is related to the backup of its datAnswer D is incorrect. The network security policy is related to the security of a company's network. Answer B is incorrect. The user password policy is related to passwords that users provide to log on to the network.
Question 96
Which of the following can be used to accomplish authentication? Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:BCD
The following can be used to accomplish authentication: 1.Password 2.Biometrics 3.Token A password is a secret word or string of characters that is used for authentication, to prove identity, or gain access to a resource.