Question 43
Which of the following is the BEST way to share incident-related artifacts to provide non-repudiation?
Correct Answer:B
Question 44
A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage The security analyst is trying to determine which user caused the malware to get onto the system Which of the following registry keys would MOST likely have this information?
A)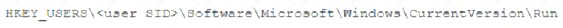
B)
C)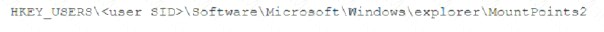
D)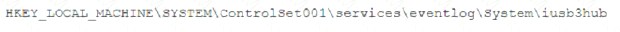
Correct Answer:C
Question 45
An organization wants to move non-essential services into a cloud computing environment. Management has a cost focus and would like to achieve a recovery time objective of 12 hours. Which of the following cloud recovery strategies would work BEST to attain the desired outcome?
Correct Answer:C
Question 46
A security analyst is supporting an embedded software team. Which of the following is the BEST recommendation to ensure proper error handling at runtime?
Correct Answer:B
Question 47
A security analyst, who is working for a company that utilizes Linux servers, receives the following results from a vulnerability scan: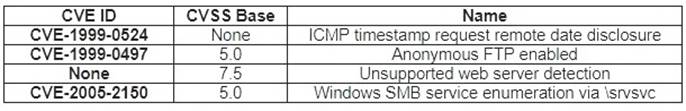
Which of the following is MOST likely a false positive?
Correct Answer:B
Question 48
After a breach involving the exfiltration of a large amount of sensitive data a security analyst is reviewing the following firewall logs to determine how the breach occurred: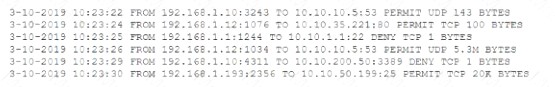
Which of the following IP addresses does the analyst need to investigate further?
Correct Answer:C