Question 37
A system administrator is doing network reconnaissance of a company’s external network to determine the vulnerability of various services that are running. Sending some sample traffic to the external host, the administrator obtains the following packet capture: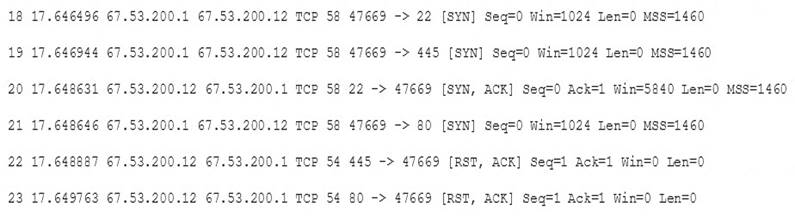
Based on the output, which of the following services should be further tested for vulnerabilities?
Correct Answer:C
Question 38
A security analyst needs to assess the web server versions on a list of hosts to determine which are running a vulnerable version of the software and output that list into an XML file named Webserverlist. Xml. The host list is provided in a file named werbserverlist,text. Which of the fallowing Nmap commands would BEST accomplish this goal?
A)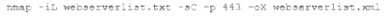
B)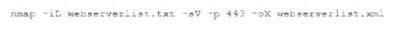
C)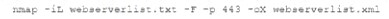
D)
Correct Answer:A
Question 39
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the desk ticket queue. INSTRUCTIONS
Click on me ticket to see the ticket details Additional content is available on tabs within the ticket
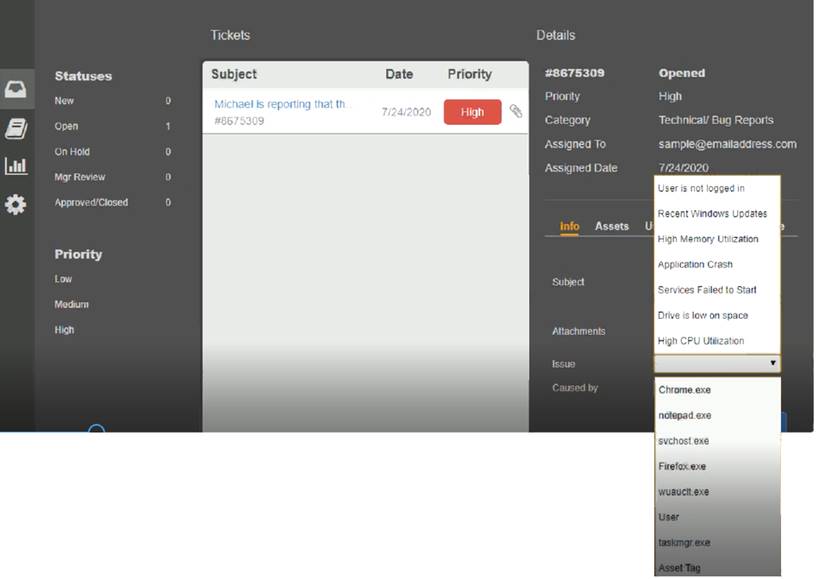
First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button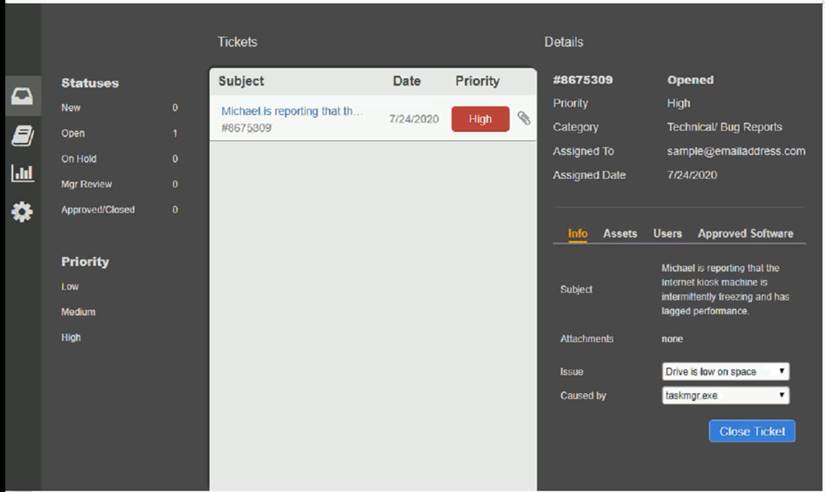
Solution: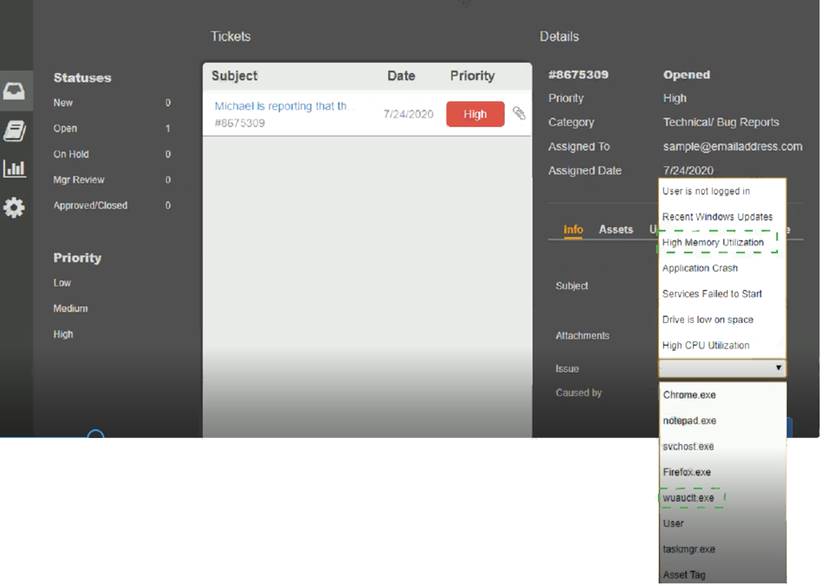
Does this meet the goal?
Correct Answer:A
Question 40
A security analyst discovers a vulnerability on an unpatched web server that is used for testing machine learning on Bing Data sets. Exploitation of the vulnerability could cost the organization $1.5 million in lost productivity. The server is located on an isolated network segment that has a 5% chance of being compromised. Which of the following is the value of this risk?
Correct Answer:A
Question 41
A security analyst for a large financial institution is creating a threat model for a specific threat actor that is likely targeting an organization's financial assets.
Which of the following is the BEST example of the level of sophistication this threat actor is using?
Correct Answer:D
Question 42
An information security analyst is compiling data from a recent penetration test and reviews the following output: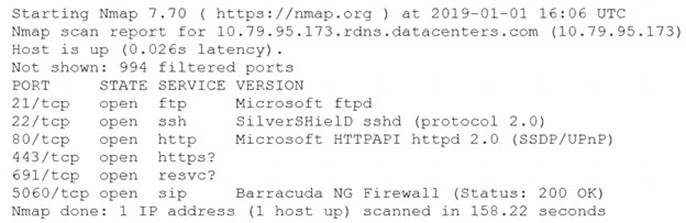
The analyst wants to obtain more information about the web-based services that are running on the target. Which of the following commands would MOST likely provide the needed information?
Correct Answer:B