Question 139
- (Exam Topic 9)
Which of the following is considered best practice for preventing e-mail spoofing?
Correct Answer:B
Question 140
- (Exam Topic 4)
An external attacker has compromised an organization’s network security perimeter and installed a sniffer onto an inside computer. Which of the following is the MOST effective layer of security the organization could have implemented to mitigate the attacker’s ability to gain further information?
Correct Answer:D
Question 141
- (Exam Topic 11)
Which of the following is a function of Security Assertion Markup Language (SAML)?
Correct Answer:D
Question 142
- (Exam Topic 11)
A software security engineer is developing a black box-based test plan that will measure the system's reaction to incorrect or illegal inputs or unexpected operational errors and situations. Match the functional testing techniques on the left with the correct input parameters on the right.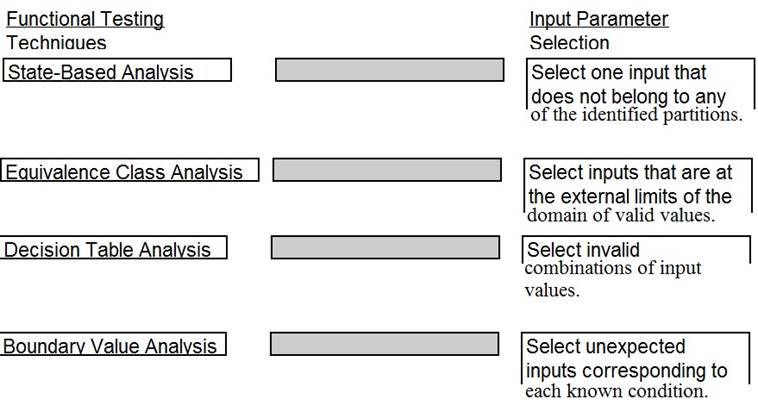
Solution: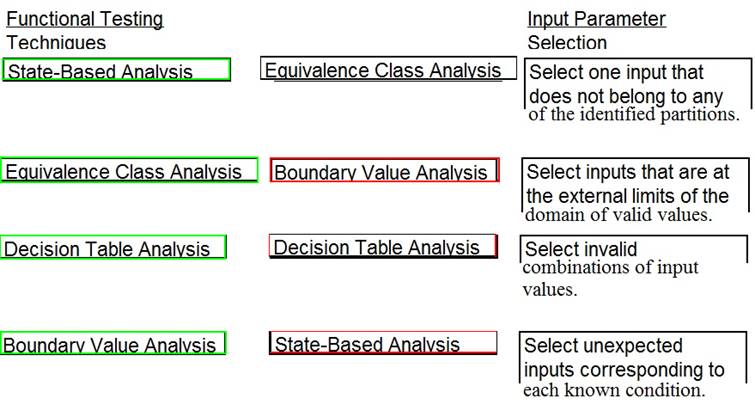
Does this meet the goal?
Correct Answer:A
Question 143
- (Exam Topic 6)
Which of the following is a PRIMARY benefit of using a formalized security testing report format and structure?
Correct Answer:D
Question 144
- (Exam Topic 9)
Copyright provides protection for which of the following?
Correct Answer:B